Linux Foundation CKS dumps - 100% Pass Guarantee!
Vendor: Linux Foundation
Certifications: Linux Foundation Certifications
Exam Name: Linux Foundation Certified Kubernetes Security Specialist (CKS)
Exam Code: CKS
Total Questions: 46 Q&As ( View Details)
Last Updated: Mar 13, 2025
Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Linux Foundation CKS Last Month Results
 97.1% Pass Rate
97.1% Pass Rate 365 Days Free Update
365 Days Free Update Verified By Professional IT Experts
Verified By Professional IT Experts 24/7 Live Support
24/7 Live Support Instant Download PDF&VCE
Instant Download PDF&VCE 3 Days Preparation Before Test
3 Days Preparation Before Test 18 Years Experience
18 Years Experience 6000+ IT Exam Dumps
6000+ IT Exam Dumps 100% Safe Shopping Experience
100% Safe Shopping Experience
CKS Q&A's Detail
| Exam Code: | CKS |
| Total Questions: | 46 |
| Simulation Labs | 46 |
CertBus Has the Latest CKS Exam Dumps in Both PDF and VCE Format
- Linux Foundation_certbus_CKS_by_WJS_41.pdf
- 263.46 KB
- Linux Foundation_certbus_CKS_by_shabib_45.pdf
- 502.37 KB
- Linux Foundation_certbus_CKS_by_J2B_40.pdf
- 1.09 MB
- Linux Foundation_certbus_CKS_by_hera_39.pdf
- 217.27 KB
- Linux Foundation_certbus_CKS_by_Ravi_Dubey_43.pdf
- 239.36 KB
- Linux Foundation_certbus_CKS_by_Stephen_Lui_37.pdf
- 1018.92 KB
CKS Online Practice Questions and Answers
Create a network policy named allow-np, that allows pod in the namespace staging to connect to port 80 of other pods in the same namespace.
Ensure that Network Policy:
1.
Does not allow access to pod not listening on port 80.
2.
Does not allow access from Pods, not in namespace staging.
A. See the explanation below:
B. PlaceHolder
Given an existing Pod named nginx-pod running in the namespace test-system, fetch the service-account-name used and put the content in /candidate/KSC00124.txt
Create a new Role named dev-test-role in the namespace test-system, which can perform update operations, on resources of type namespaces.
Create a new RoleBinding named dev-test-role-binding, which binds the newly created Role to the Pod's ServiceAccount ( found in the Nginx pod running in namespace test- system).
A. See explanation below.
B. PlaceHolder
Cluster: dev Master node: master1 Worker node: worker1 You can switch the cluster/configuration context using the following command: [desk@cli] $ kubectl config use-context dev Task:
Retrieve the content of the existing secret named adam in the safe namespace.
Store the username field in a file names /home/cert-masters/username.txt, and the password field in a file named /home/cert-masters/password.txt.
1.
You must create both files; they don't exist yet.
2.
Do not use/modify the created files in the following steps, create new temporary files if needed.
Create a new secret names newsecret in the safe namespace, with the following content:
Username: dbadmin Password: moresecurepas
Finally, create a new Pod that has access to the secret newsecret via a volume:
Namespace:safe Pod name:mysecret-pod Container name:db-container Image:redis Volume name:secret-vol Mount path:/etc/mysecret
A. See the explanation below
B. PlaceHolder
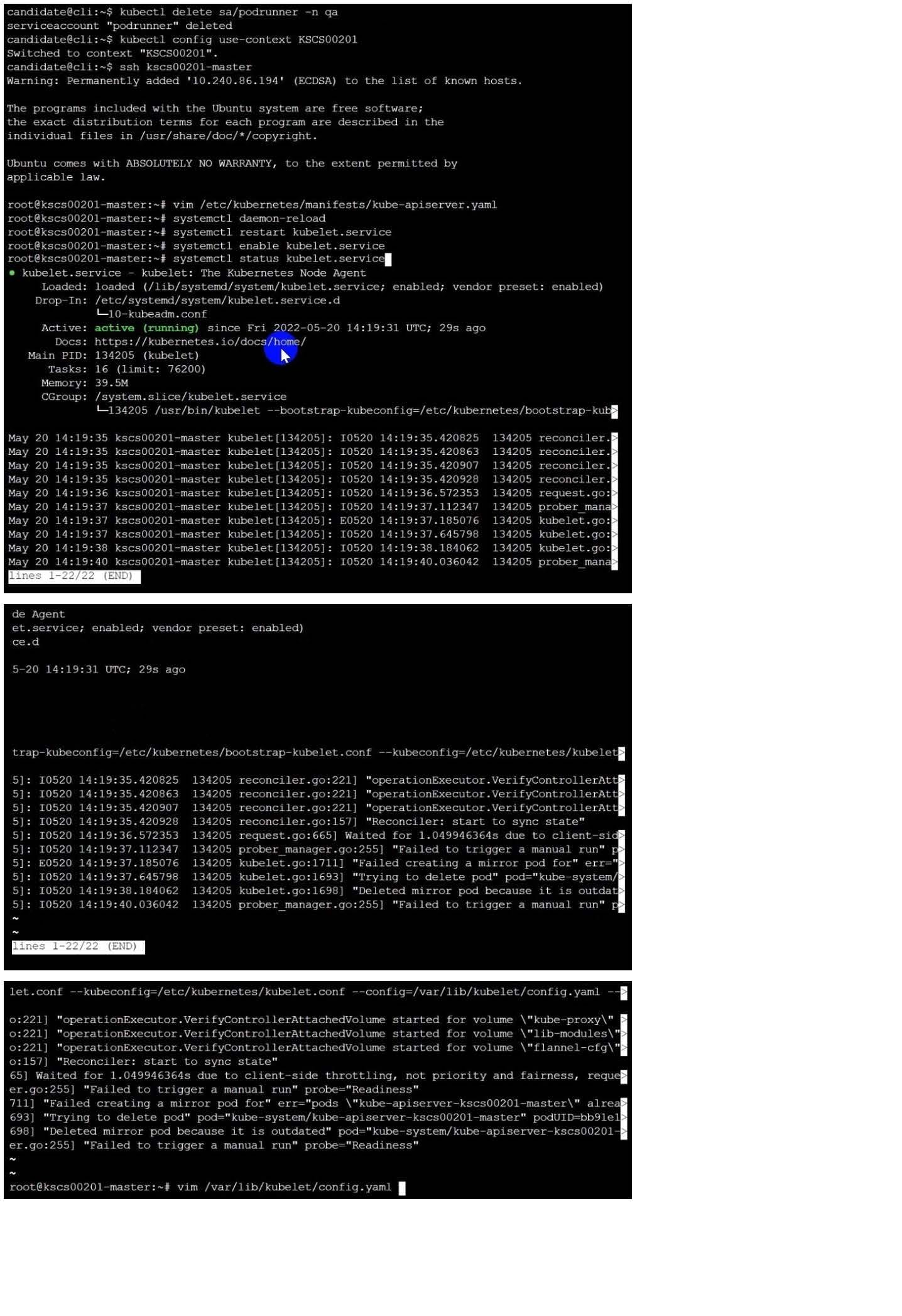
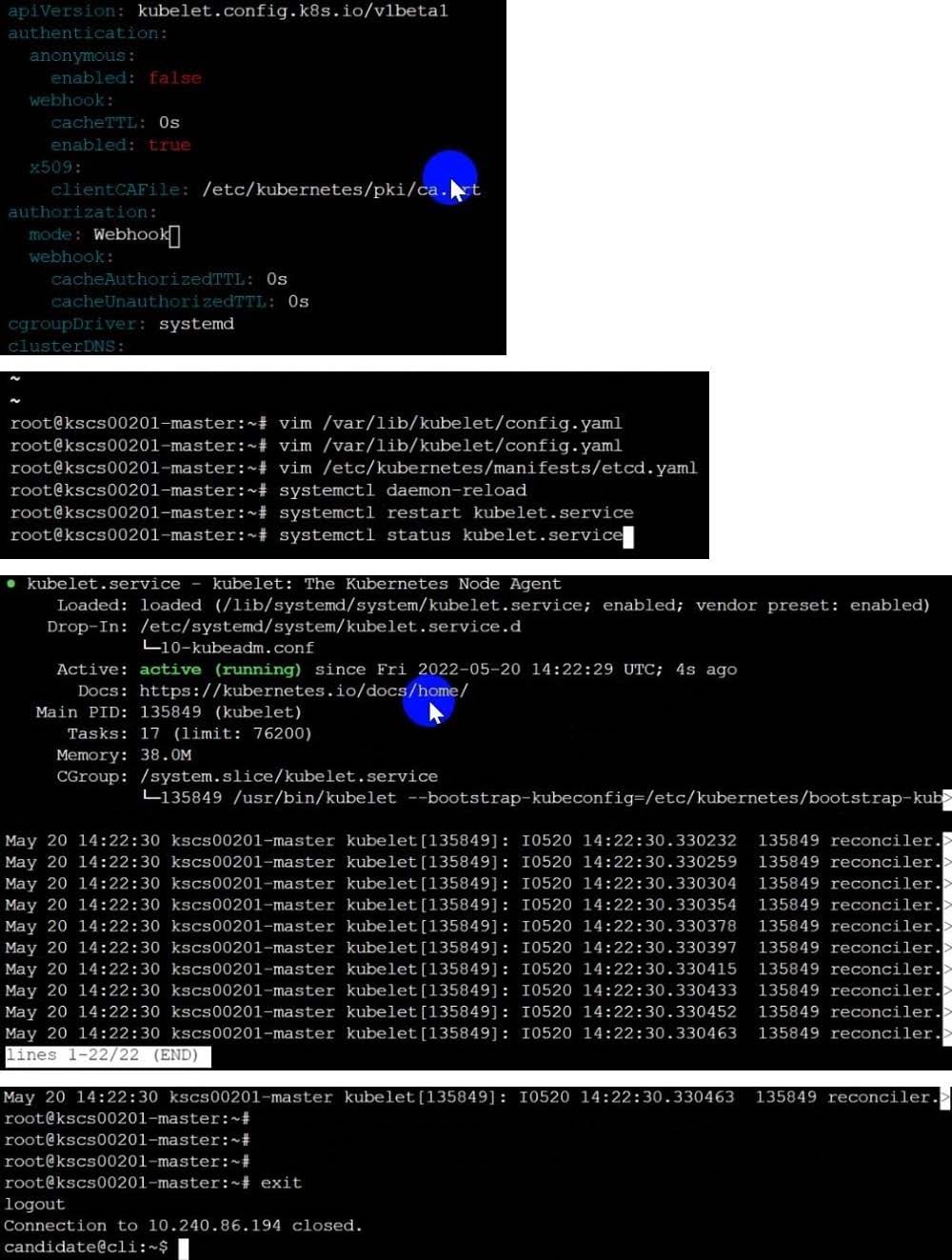
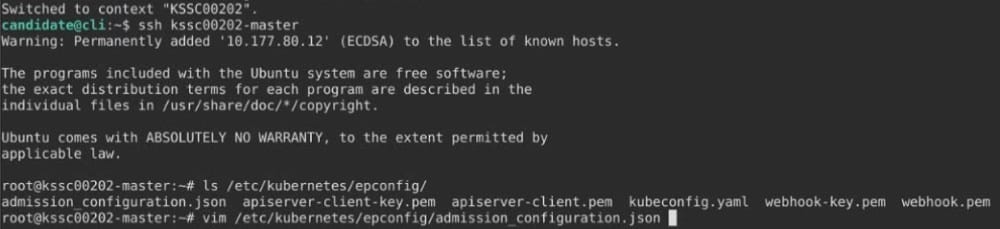
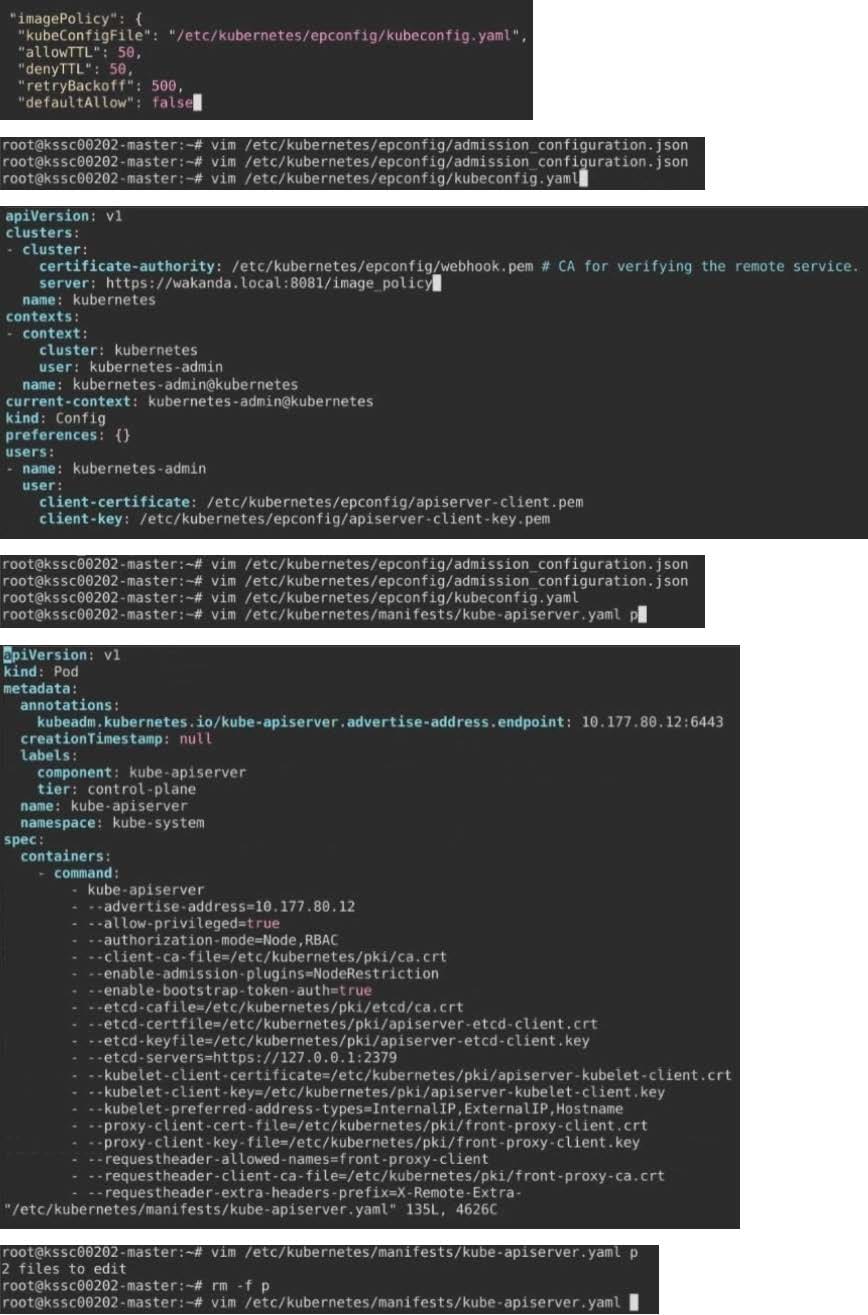
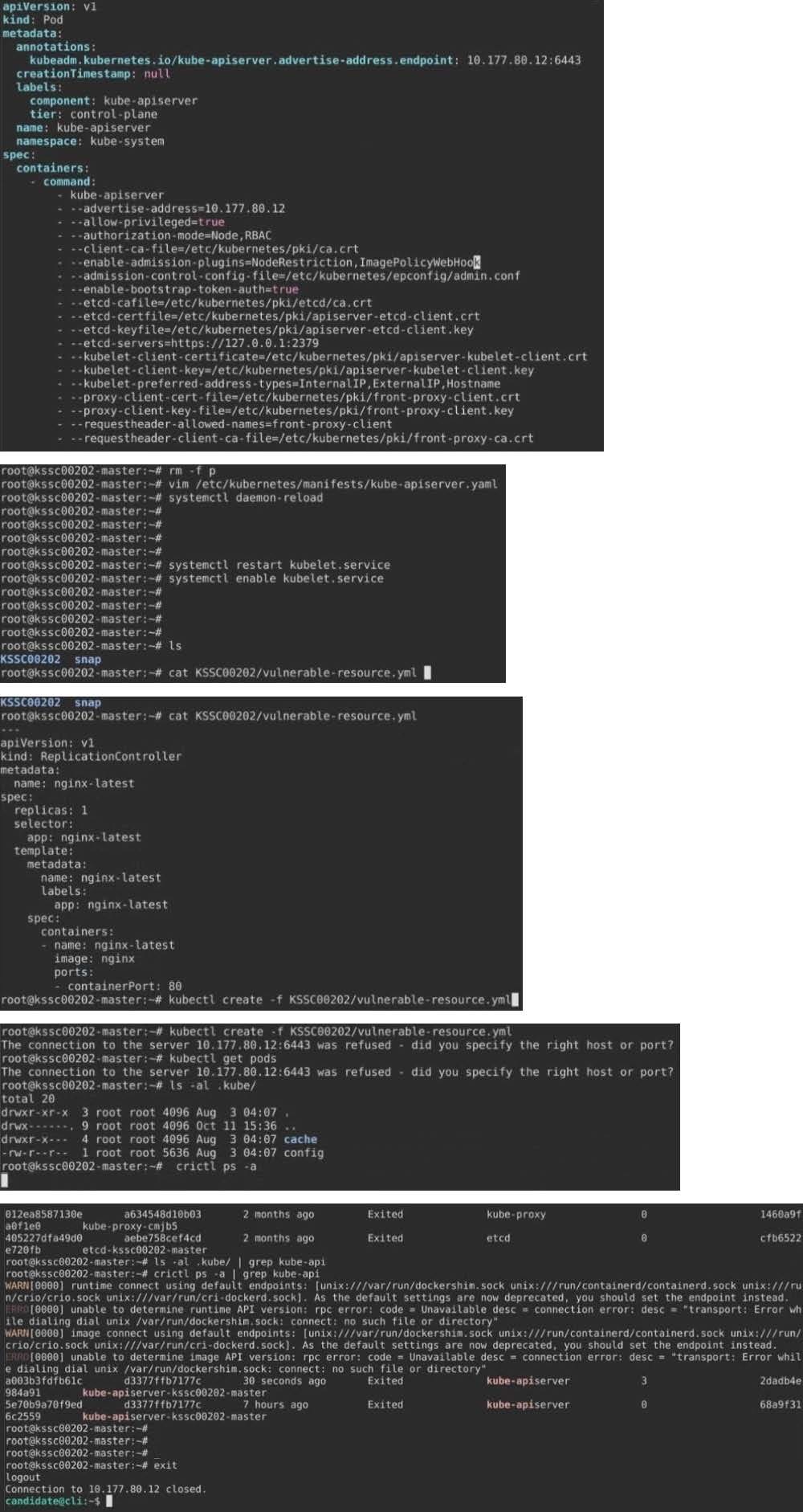
Fix all issues via configuration and restart the affected components to ensure the new setting takes effect.
Fix all of the following violations that were found against the API server:
1.
Ensure the --authorization-mode argument includes RBAC
2.
Ensure the --authorization-mode argument includes Node
3.
Ensure that the --profiling argument is set to false
Fix all of the following violations that were found against the Kubelet:
1.
Ensure the --anonymous-auth argument is set to false.
2.
Ensure that the --authorization-mode argument is set to Webhook. Fix all of the following violations that were found against the ETCD:
Ensure that the --auto-tls argument is not set to true Hint: Take the use of Tool Kube-Bench
A. See the below.
B. PlaceHolder
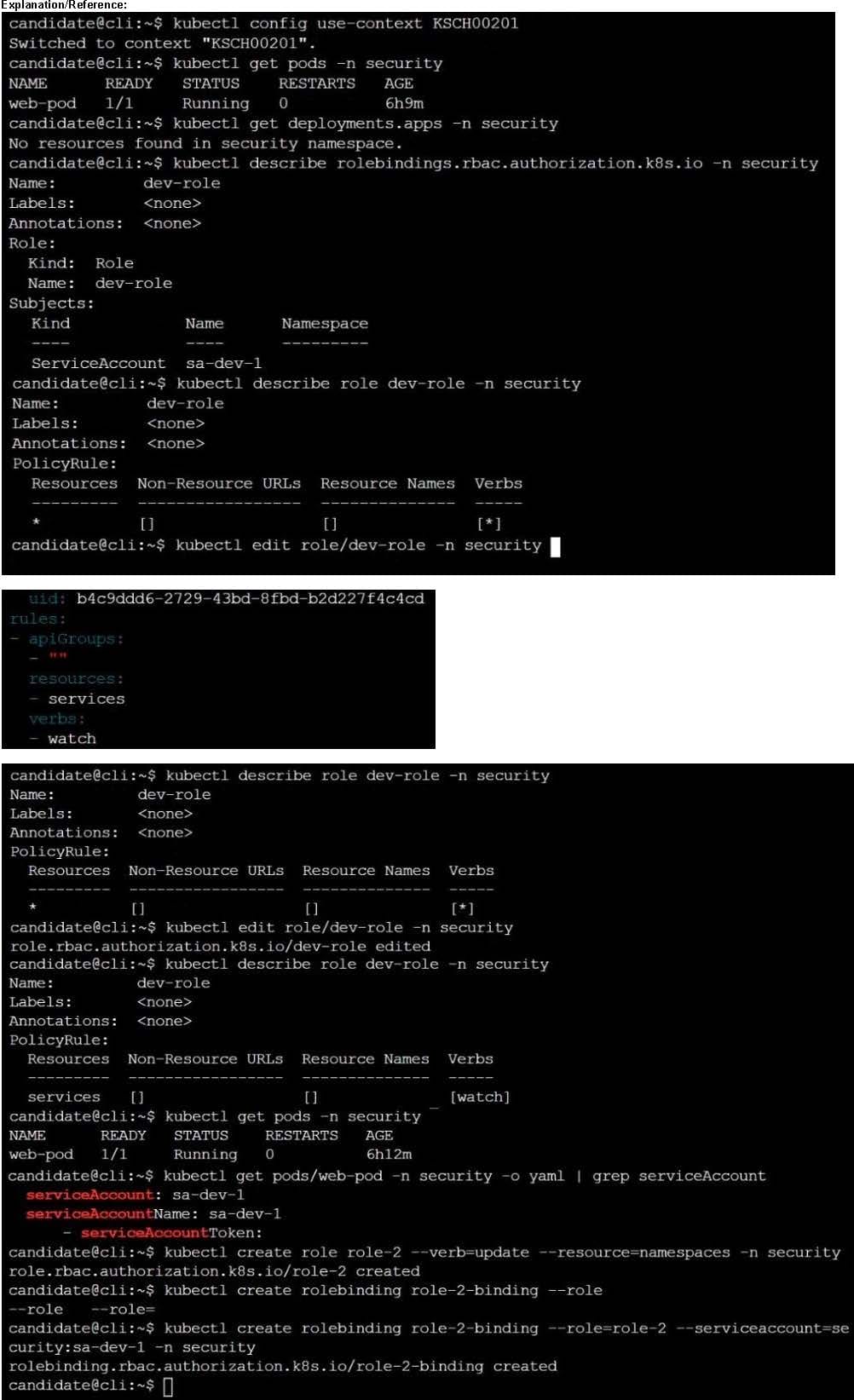
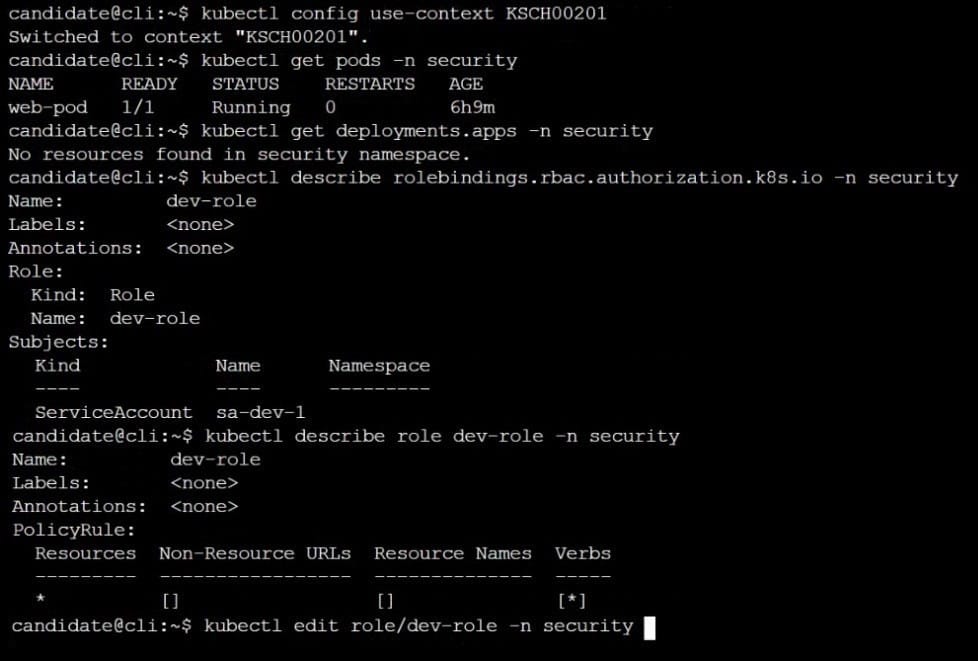
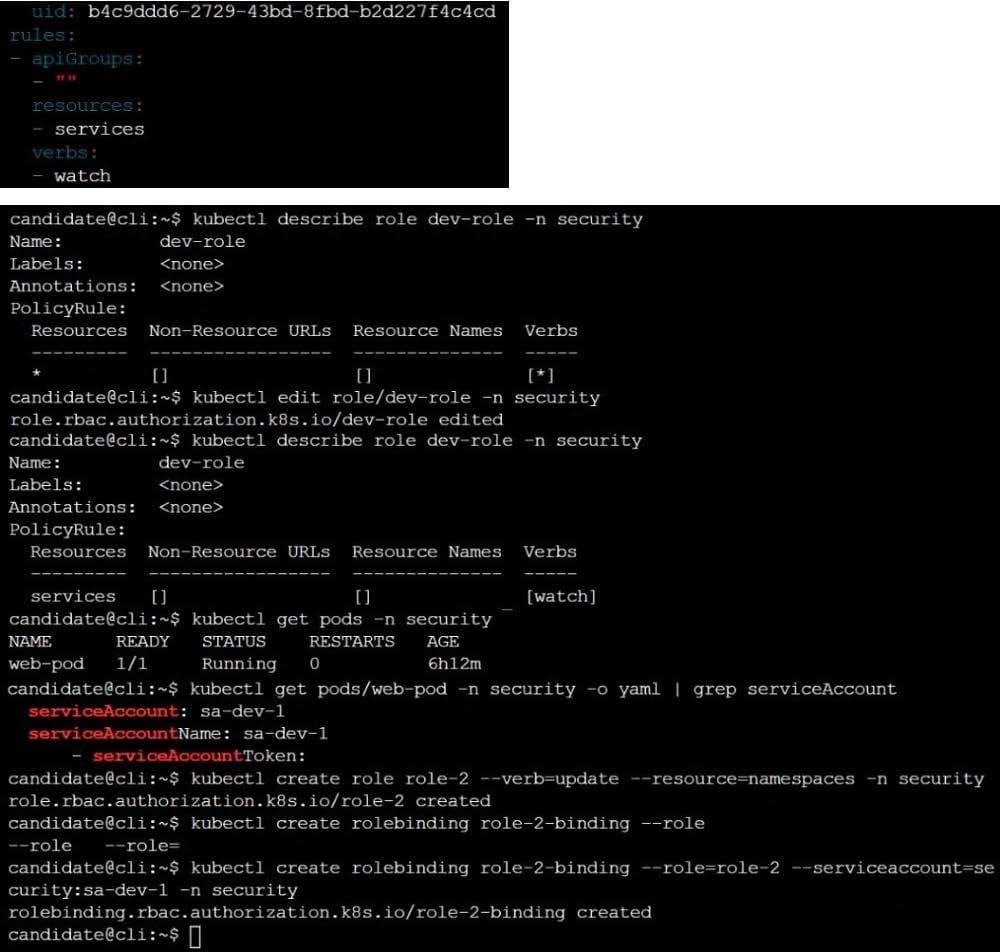
A Role bound to a Pod's ServiceAccount grants overly permissive permissions. Complete the following tasks to reduce the set of permissions.
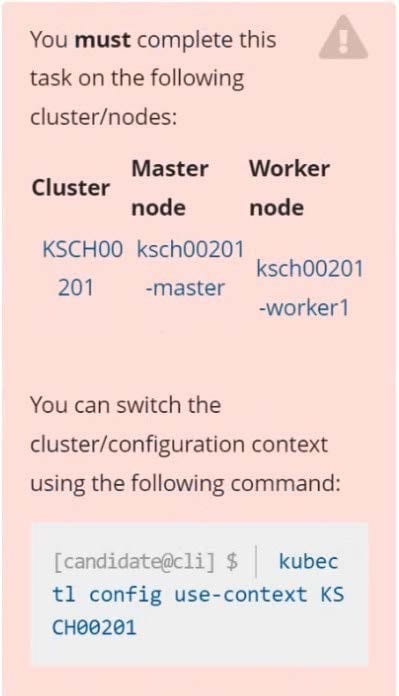
Task
Given an existing Pod named web-pod running in the namespace security.
Edit the existing Role bound to the Pod's ServiceAccount sa-dev-1 to only allow performing watch operations, only on resources of type services.
Create a new Role named role-2 in the namespace security, which only allows performing update
operations, only on resources of type namespaces.
Create a new RoleBinding named role-2-binding binding the newly created Role to the Pod's ServiceAccount.

A. See the explanation below
B. PlaceHolder
Add Comments
Success Stories
- Pakistan
- Keeley
- Mar 21, 2025
- Rating: 4.8 / 5.0
![]()
Valid material !! I will continue using this material and introduced it to other friend. Good thing should be shared with friend.
- Quebec
- Ludo
- Mar 19, 2025
- Rating: 5.0 / 5.0
Save your money on expensive classroom courses. Buy these dumps, it will be more helpful if you want to pass the CKS exam!!!
- South Africa
- Wyatt
- Mar 19, 2025
- Rating: 4.3 / 5.0
![]()
This is the valid dumps. I passed mine yesterday. All the questions are from this dumps. Thanks.
- Rwanda
- Wanda
- Mar 18, 2025
- Rating: 4.5 / 5.0
![]()
Dump is still valid, I just passed my CKS exam today. Thanks to you all.
- Ghana
- Kevin
- Mar 17, 2025
- Rating: 4.1 / 5.0
![]()
The Dumb is valid 100%.
- Australia
- Pasi
- Mar 15, 2025
- Rating: 4.7 / 5.0
![]()
took the exams yesterday and passed. I was very scared at first because the labs came in first so I was spending like 10 to 13mins so I started rushing after the first three labs thinking that I will have more labs. I ended up finishing the exam in an hour.. dumps are valid.
- United States
- Zouleha
- Mar 15, 2025
- Rating: 5.0 / 5.0
![]()
Update quickly and be rich in content,this dumps is really valid. Thanks.
- Cambodia
- William
- Mar 14, 2025
- Rating: 4.8 / 5.0
![]()
Yes, i have passed the exam by using this dumps,so you also can try it and you will have unexpected achievements. Recommend to all.
- Greece
- Ramon
- Mar 14, 2025
- Rating: 4.9 / 5.0
![]()
The answers are accurate. Well you should notice some of the questions are slightly changed. Be careful.
- Sri Lanka
- Whalen
- Mar 13, 2025
- Rating: 4.1 / 5.0
![]()
This dumps is very valid, and i have passed the exam perfectly. Thanks very much, I will continue using it.
Linux Foundation CKS exam official information: CKS is a performance-based certification exam that tests candidates' knowledge of Kubernetes and cloud security in a simulated, real world environment. Candidates must have taken and passed the Certified Kubernetes Administrator (CKA) exam prior to attempting the CKS exam.


 Printable PDF
Printable PDF