PCNSE Online Practice Questions and Answers
DRAG DROP
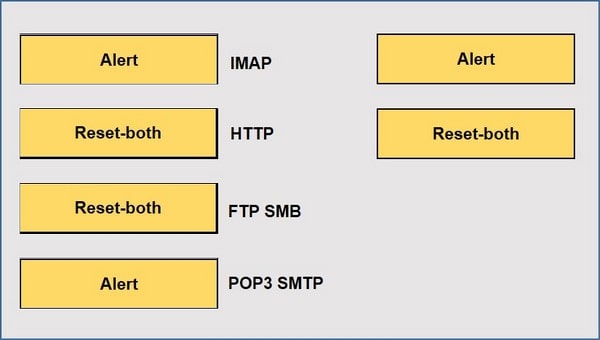
When using the predefined default profile, the policy will inspect for viruses on the decoders. Match each decoder with its default action. Answer options may be used more than once or not at all.
Select and Place:
What happens when an A P firewall cluster synchronies IPsec tunnel security associations (SAs)?
A. Phase 2 SAs are synchronized over HA2 finks
B. Phase 1 and Phase 2 SAs are synchronized over HA2 links
C. Phase 1 SAs are synchronized over HA1 links
D. Phase 1 and Phase 2 SAs are synchronized over HA3 links
The firewall identifies a popular application as an unknown-tcp.
Which two options are available to identify the application? (Choose two.)
A. Create a custom application.
B. Create a custom object for the custom application server to identify the custom application.
C. Submit an App-ID request to Palo Alto Networks.
D. Create a Security policy to identify the custom application.
Which option describes the operation of the automatic commit recovery feature?
A. It enables a firewall to revert to the previous configuration if rule shadowing is detected
B. It enables a firewall to revert to the previous configuration if a commit causes Panorama connectivity failure.
C. It enables a firewall to revert to the previous configuration if application dependency errors are found
D. It enables a firewall to revert to the previous configuration if a commit causes HA partner connectivity failure
Which is not a valid reason for receiving a decrypt-cert-validation error?
A. Unsupported HSM
B. Unknown certificate status
C. Client authentication
D. Untrusted issuer
Which CLI command displays the current management plan memory utilization?
A. > show system info
B. > show system resources
C. > debug management-server show
D. > show running resource-monitor
Which three options are available when creating a security profile? (Choose three)
A. Anti-Malware
B. File Blocking
C. Url Filtering
D. IDS/ISP
E. Threat Prevention
F. Antivirus
A company is deploying User-ID in their network. The firewall learn needs to have the ability to see and choose from a list of usernames and user groups directly inside the Panorama policies when creating new security rules.
How can this be achieved?
A. By configuring Data Redistribution Client in Panorama > Data Redistribution
B. By configuring User-ID source device in Panorama > Managed Devices
C. By configuring User-ID group mapping in Panorama > User Identification
D. By configuring Master Device in Panorama > Device Groups
An engineer is tasked with configuring a Zone Protection profile on the untrust zone.
Which three settings can be configured on a Zone Protection profile? (Choose three.)
A. Ethernet SGT Protection
B. Protocol Protection
C. DoS Protection
D. Reconnaissance Protection
E. Resource Protection
Four configuration choices are listed, and each could be used to block access to a specific URL.
If you configured each choice to block the same URL, then which choice would be evaluated last in the processing order to block access to the URL?
A. PAN-DB URL category in URL Filtering profile
B. Custom URL category in Security policy rule
C. Custom URL category in URL Filtering profile
D. EDL in URL Filtering profile
An administrator connected a new fiber cable and transceiver to interface Ethernetl/l on a Palo Alto Networks firewall. However, the link does not seem to be coming up.
If an administrator were to troubleshoot, how would they confirm the transceiver type, tx-power, rx-power, vendor name, and part number via the CLI?
A. show system state filter sw.dev.interface.config
B. show chassis status slot s1
C. show system state filter-pretty sys.s1.*
D. show system state filter ethernet1/1
A security team has enabled real-time WildFire signature lookup on all its firewalls.
Which additional action will further reduce the likelihood of newly discovered malware being allowed through the firewalls?
A. increase the frequency of the applications and threats dynamic updates.
B. Increase the frequency of the antivirus dynamic updates
C. Enable the "Hold Mode" option in Objects > Security Profiles > Antivirus.
D. Enable the "Report Grayware Files" option in Device > Setup > WildFire.
A firewall engineer is managing a Palo Alto Networks NGFW that does not have the DHCP server on DHCP agent configuration.
Which interface mode can the broadcast DHCP traffic?
A. Virtual ware
B. Tap
C. Layer 2
D. Layer 3
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits. Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
A. Use SSL Forward Proxy instead of SSL Inbound Inspection for decryption.
B. Use RSA instead of ECDSA for traffic that isn't sensitive or high-priority.
C. Use the highest TLS protocol version to maximize security.
D. Use ECDSA instead of RSA for traffic that isn't sensitive or high-priority.
Given the following snippet of a WildFire submission log, did the end user successfully download a file?
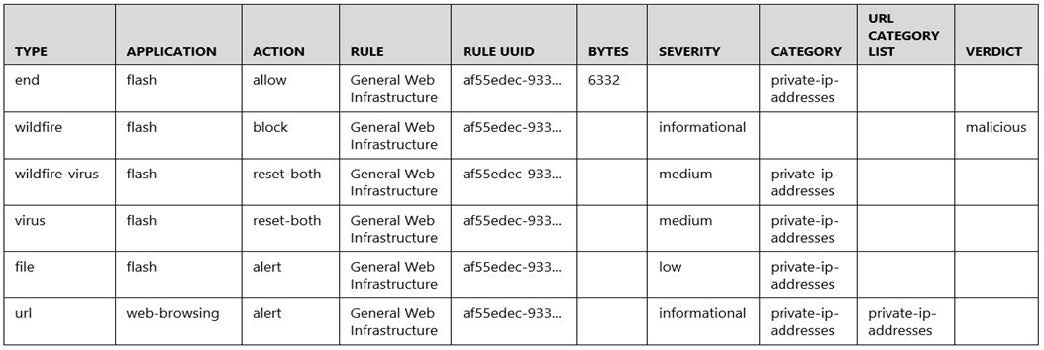
A. Yes, because the final action is set to "allow."
B. No, because the action for the wildfire-virus is "reset-both."
C. No, because the URL generated an alert.
D. Yes, because both the web-browsing application and the flash file have the "alert" action.