SOA-C02 Online Practice Questions and Answers
A company is partnering with an external vendor to provide data processing services. For this integration, the vendor must host the company's data in an Amazon S3 bucket in the vendor's AWS account. The vendor is allowing the company to provide an AWS Key Management Service (AWS KMS) key to encrypt the company's data. The vendor has provided an IAM role Amazon Resource Name (ARN) to the company for this integration.
What should a SysOps administrator do to configure this integration?
A. Create a new KMS key. Add the vendor's IAM role ARN to the KMS key policy. Provide the new KMS key ARN to the vendor.
B. Create a new KMS key. Create a new IAM user. Add the vendor's IAM role ARN to an inline policy that is attached to the IAM user. Provide the new IAM user ARN to the vendor.
C. Configure encryption using the KMS managed S3 key. Add the vendor's IAM role ARN to the KMS managed S3 key policy. Provide the KMS managed S3 key ARN to the vendor.
D. Configure encryption using the KMS managed S3 key. Create an S3 bucket. Add the vendor's IAM role ARN to the S3 bucket policy. Provide the S3 bucket ARN to the vendor.
A SysOps administrator is required to monitor free space on Amazon EBS volumes attached to Microsoft Windows-based Amazon EC2 instances within a company's account. The administrator must be alerted to potential issues.
What should the administrator do to receive email alerts before low storage space affects EC2 instance performance?
A. Use built-in Amazon CloudWatch metrics, and configure CloudWatch alarms and an Amazon SNS topic for email notifications
B. Use AWS CloudTrail logs and configure the trail to send notifications to an Amazon SNS topic.
C. Use the Amazon CloudWatch agent to send disk space metrics, then set up CloudWatch alarms using an Amazon SNS topic.
D. Use AWS Trusted Advisor and enable email notification alerts for EC2 disk space
A company's web application is available through an Amazon CloudFront distribution and directly through an internet-facing Application Load Balancer (ALB) A SysOps administrator must make the application accessible only through the CloudFront distribution and not directly through the ALB. The SysOps administrator must make this change without changing the application code.
Which solution will meet these requirements?
A. Modify the ALB type to internal Set the distribution's origin to the internal ALB domain name
B. Create a Lambda@Edge function Configure the function to compare a custom header value in the request with a stored password and to forward the request to the origin in case of a match Associate the function with the distribution.
C. Replace the ALB with a new internal ALB Set the distribution's origin to the internal ALB domain name Add a custom HTTP header to the origin settings for the distribution In the ALB listener add a rule to forward requests that contain the matching custom header and the header's value Add a default rule to return a fixed response code of 403.
D. Add a custom HTTP header to the origin settings for the distribution in the ALB listener add a rule to forward requests that contain the matching custom header and the header's value Add a default rule to return a fixed response code of 403.
A SysOps administrator needs to track the costs of data transfer between AWS Regions. The SysOps administrator must implement a solution to send alerts to an email distribution list when transfer costs reach 75% of a specific threshold.
What should the SysOps administrator do to meet these requirements?
A. Create an AWS Cost and Usage Report. Analyze the results in Amazon Athena. Configure an alarm to publish a message to an Amazon Simple Notification Service (Amazon SNS) topic when costs reach 75% of the threshold. Subscribe the email distribution list to the topic.
B. Create an Amazon CloudWatch billing alarm to detect when costs reach 75% of the threshold. Configure the alarm to publish a message to an Amazon Simple Notification Service (Amazon SNS) topic. Subscribe the email distribution list to the topic.
C. Use AWS Budgets to create a cost budget for data transfer costs. Set an alert at 75% of the budgeted amount. Configure the budget to send a notification to the email distribution list when costs reach 75% of the threshold.
D. Set up a VPC flow log. Set up a subscription filter to an AWS Lambda function to analyze data transfer. Configure the Lambda function to send a notification to the email distribution list when costs reach 75% of the threshold.
A global company handles a large amount of personally identifiable information (Pll) through an internal web portal. The company's application runs in a corporate data center that is connected to AWS through an AWS Direct Connect connection. The application stores the Pll in Amazon S3. According to a compliance requirement, traffic from the web portal to Amazon S3 must not travel across the internet.
What should a SysOps administrator do to meet the compliance requirement?
A. Provision an interface VPC endpoint for Amazon S3. Modify the application to use the interface endpoint.
B. Configure AWS Network Firewall to redirect traffic to the internal S3 address.
C. Modify the application to use the S3 path-style endpoint.
D. Set up a range of VPC network ACLs to redirect traffic to the Internal S3 address.
A Sysops administrator needs to configure automatic rotation for Amazon RDS database credentials. The credentials must rotate every 30 days. The solution must integrate with Amazon RDS. Which solution will meet these requirements with the LEAST operational overhead?
A. Store the credentials in AWS Systems Manager Parameter Store as a secure string. Configure automatic rotation with a rotation interval of 30 days.
B. Store the credentials in AWS Secrets Manager. Configure automatic rotation with a rotation interval of 30 days.
C. Store the credentials in a file in an Amazon S3 bucket. Deploy an AWS Lambda function to automatically rotate the credentials every 30 days.
D. Store the credentials in AWS Secrets Manager. Deploy an AWS Lambda function to automatically rotate the credentials every 30 days.
A company has launched a social media website that gives users the ability to upload images directly to a centralized Amazon S3 bucket. The website is popular in areas that are geographically distant from the AWS Region where the S3 bucket is located. Users are reporting that uploads are slow. A SysOps administrator must improve the upload speed.
What should the SysOps administrator do to meet these requirements?
A. Create S3 access points in Regions that are closer to the users.
B. Create an accelerator in AWS Global Accelerator for the S3 bucket.
C. Enable S3 Transfer Acceleration on the S3 bucket.
D. Enable cross-origin resource sharing (CORS) on the S3 bucket.
A manufacturing company uses an Amazon RDS DB instance to store inventory of all stock items. The company maintains several AWS Lambda functions that interact with the database to add, update, and delete items. The Lambda
functions use hardcoded credentials to connect to the database.
A SysOps administrator must ensure that the database credentials are never stored in plaintext and that the password is rotated every 30 days.
Which solution will meet these requirements in the MOST operationally efficient manner?
A. Store the database password as an environment variable for each Lambda function. Create a new Lambda function that is named PasswordRotate. Use Amazon EventBridge (Amazon CloudWatch Events) to schedule the PasswordRotate function every 30 days to change the database password and update the environment variable for each Lambda function.
B. Use AWS Key Management Service (AWS KMS) to encrypt the database password and to store the encrypted password as an environment variable for each Lambda function. Grant each Lambda function access to the KMS key so that the database password can be decrypted when required. Create a new Lambda function that is named PasswordRotate to change the password every 30 days.
C. Use AWS Secrets Manager to store credentials for the database. Create a Secrets Manager secret, and select the database so that Secrets Manager will use a Lambda function to update the database password automatically. Specify an automatic rotation schedule of 30 days. Update each Lambda function to access the database password from SecretsManager.
D. Use AWS Systems Manager Parameter Store to create a secure string to store credentials for the database. Create a new Lambda function called PasswordRotate. Use Amazon EventBridge (Amazon CloudWatch Events) to schedule the PasswordRotate function every 30 days to change the database password and to update the secret within Parameter Store. Update each Lambda function to access the database password from Parameter Store.
A company uses AWS CloudFormation to deploy its application infrastructure Recently, a user accidentally changed a property of a database in a CloudFormation template and performed a stack update that caused an interruption to the application A SysOps administrator must determine how to modify the deployment process to allow the DevOps team to continue to deploy the infrastructure, but prevent against accidental modifications to specific resources.
Which solution will meet these requirements?
A. Set up an AWS Config rule to alert based on changes to any CloudFormation stack An AWS Lambda function can then describe the stack to determine if any protected resources were modified and cancel the operation
B. Set up an Amazon CloudWatch Events event with a rule to trigger based on any CloudFormation API call An AWS Lambda function can then describe the stack to determine if any protected resources were modified and cancel the operation
C. Launch the CloudFormation templates using a stack policy with an explicit allow for all resources and an explicit deny of the protected resources with an action of Update:*.
D. Attach an IAM policy to the DevOps team role that prevents a CloudFormation stack from updating, with a condition based on the specific Amazon Resource Names (ARNs) of the protected resources
A company is implementing security and compliance by using AWS Trusted Advisor. The company's SysOps team is validating the list of Trusted Advisor checks that it can access. Which factor will affect the quantity of available Trusted Advisor checks?
A. Whether at least one Amazon EC2 instance is in the running state
B. The AWS Support plan
C. An AWS Organizations service control policy (SCP)
D. Whether the AWS account root user has multi-factor authentication (MFA) enabled
A SysOps administrator is attempting to deploy resources by using an AWS CloudFormation template. An Amazon EC2 instance that is defined in the template fails to launch and produces an InsufficientInstanceCapacity error. Which actions should the SysOps administrator take to resolve this error? (Choose two.)
A. Create a separate AWS CloudFormation template for the EC2 instance.
B. Modify the AWS CloudFormation template to not specify an Availability Zone for the EC2 instance.
C. Modify the AWS CloudFormation template to use a different EC2 instance type.
D. Use a different Amazon Machine Image (AMI) for the EC2 instance.
E. Use the AWS CLI's validate-template command before creating a stack from the template.
A company runs an application that uses a MySQL database on an Amazon EC2 instance. The EC2 instance has a General Purpose SSD Amazon Elastic Block Store (Amazon EBS) volume. The company made changes to the application
code and now wants to perform load testing to evaluate the impact of the code changes. A SysOps administrator must create a new MySQL instance from a snapshot of the existing production instance. This new instance needs to perform as
similarly as possible to the production instance.
Which restore option meets these requirements?
A. Use EBS fast snapshot restore to create a new General Purpose SSD EBS volume from the production snapshot.
B. Use EBS fast snapshot restore to create a new Provisioned IOPS SSD EBS volume from the production snapshot.
C. Use EBS snapshot restore to create a new General Purpose SSD EBS volume from the production snapshot.
D. Use EBS snapshot restore to create a new Provisioned IOPS SSD EBS volume from the production snapshot.
An Amazon CloudFront distribution has a single Amazon S3 bucket as its origin. A SysOps administrator must ensure that users can access the S3 bucket only through requests from the CloudFront endpoint. Which solution will meet these requirements?
A. Configure S3 Block Public Access on the S3 bucket. Update the S3 bucket policy to allow the GetObject action from only the CloudFront distribution.
B. Configure Origin Shield in the CloudFront distribution. Update the CloudFront origin to include a custom Origin_Shield header.
C. Create an origin access identity (OAI). Assign the OAI to the CloudFront distribution. Update the S3 bucket policy to restrict access to the OAI.
D. Create an origin access identity (OAI). Assign the OAI to the S3 bucket. Update the CloudFront origin to include a custom Origin header with the OAI value.
A SysOps administrator needs to design a disaster recovery (DR) plan for an application on AWS. The application runs on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances are in an Auto Scaling group. The application uses an Amazon Aurora PostgreSQL database. The recovery time objective (RTO) and recovery point objective (RPO) are 15 minutes each.
Which combination of steps should the SysOps administrator take to meet these requirements MOST cost-effectively? (Choose two.)
A. Configure Aurora backups to be exported to the DR Region.
B. Configure the Aurora cluster to replicate data to the DR Region by using the Aurora global database option.
C. Configure the DR Region with an ALB and an Auto Scaling group. Use the same configuration as in the primary Region.
D. Configure the DR Region with an ALB and an Auto Scaling group. Set the Auto Scaling group's minimum capacity, maximum capacity, and desired capacity to 1.
E. Manually launch a new ALB and a new Auto Scaling group by using AWS CloudFormation during a failover activity.
A SysOps administrator needs to create an Amazon S3 bucket as a resource in an AWS CloudFormation template. The bucket name must be randomly generated, and the bucket must be encrypted. Other resources in the template will reference the bucket.
Which CloudFormation resource definition should the SysOps administrator use to meet these requirements?
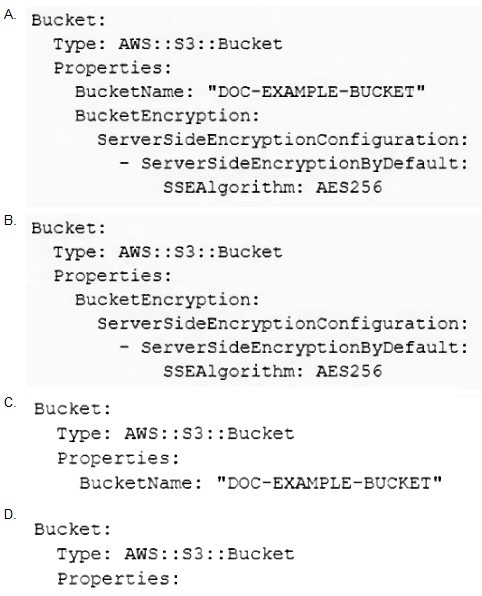
A. Option A
B. Option B
C. Option C
D. Option D
