SECRET-SEN Online Practice Questions and Answers
What is a main advantage of using dual accounts in password management?
A. Since passwords are cached for both rotation accounts, it ensures the password for an application will not be changed, reducing the amount of blackout dates when a password expires.
B. It ensures passwords are rotated every 90 days, which respects the expected downtime for a system, database, or application
C. It ensures no delays are incurred when the application needs credentials because a password that is currently used by an application will never be changed
D. Since there are two active accounts, it doubles the probability that a system, database, or application will successfully authenticate.
You have a PowerShell script that is being used on 1000 workstations. It requires a Windows Domain credential that is currently hard coded in the script.
What is the simplest solution to remove that credential from the Script?
A. Modify the script to use the CLI SDK to fetch the secret at runtime using Credential Providers installed on each workstation.
B. Modify the script to make a SOAP call to retrieve the secret from the Central Credential Provider.
C. Modify the script to run on WebSphere using the Application Server Credential Provider to retrieve the secret.
D. Use Conjur Summon to invoke the script and inject the secret at run time.
After manually failing over to your disaster recovery site (Site B) for testing purposes, you need to failback to your primary site (Site A).
Which step is required?
A. Contact CyberArk for a new license file.
B. Reconfigure the Vault Conjur Synchronizer to point to the new Conjur Leader.
C. Generate a seed for the new Leader to be deployed in Site A.
D. Trigger autofailover to promote the Standby in Site A to Leader.
You are enabling synchronous replication on Conjur cluster.
What should you do?
A. Execute this command on the Leader: docker exec
B. Execute this command on each Standby: docker exec
C. In Conjur web UI, click the Tools icon in the top right corner of the main window. Choose Conjur Cluster and click "Enable synchronous replication" in the entry for Leader.
D. In Conjur web UI, click the Tools icon in the top right corner of the main window. Choose Conjur Cluster and click "Enable synchronous replication" in the entry for Standbys.
When an application is retrieving a credential from Conjur, the application authenticates to Follower A. Follower B receives the next request to retrieve the credential.
What happens next?
A. The Coniur Token is stateless and Follower B is able to validate the Token and satisfy the request.
B. The Coniur Token is stateful and Follower B is unable to validate the Token promptinq the application to re-authenticate.
C. The Coryur Token is stateless and Follower B redirects the request to Follower A to satisfy the request.
D. The Coniur Token is stateful and Follower B redirects the request to Follower A to satisfy the request.
You modified a Conjur host policy to change its annotations for authentication.
How should you load the policy to make those changes?
A. Use the default "append" method (e.g. conjur policy load
B. Use the "replace" method (e.g. conjur policy load ?璻eplace<;branc>;<;policy-fil>;).
C. Use the "delete" method (e.g. conjur policy load ?璬elete<;branc>;<;policy-fil>;).
D. Use the "update" method (e.g. conjur policy load ?璾pdate<;branc>;<;policy-fil>;).
When installing the CCP and configuring it for use behind a load balancer, which authentication methods may be affected? (Choose two.)
A. Allowed Machines authentication
B. [Client Certificate authentication
C. OS User
D. Path
E. Hash
An application owner reports that their application is suddenly receiving an incorrect password. CPM logs show the password was recently changed, but the value currently being retrieved by the application is a different value. The Vault Conjur Synchronizer service is running.
What is the most likely cause of this issue?
A. The Vault Conjur Synchronizer is not configured with the DR Vault IP address and there has been a failover event.
B. Dual Accounts are in use, but after the CPM changed the password for the Inactive account, it accidentally updated the password for the Active account instead.
C. The CPM is writing password changes to the Primary Vault while the Vault Conjur Synchronizer is configured to replicate from the DR Vault.
D. The application has been configured to retrieve the wrong password.
When attempting to retrieve a credential managed by the Synchronizer, you receive this error:
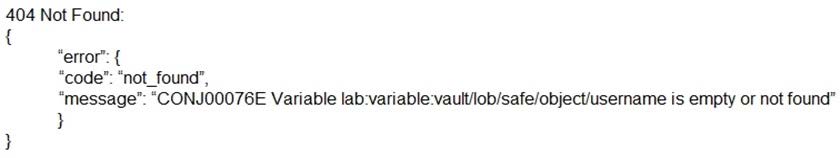
What is the cause of the issue?
A. The Conjur Leader has lost upstream connectivity to the Vault Conjur Synchronizer.
B. The host does not have access to the credential.
C. The path to the credential was not properly encoded.
D. The Vault Conjur Synchronizer has crashed and needs to be restarted.
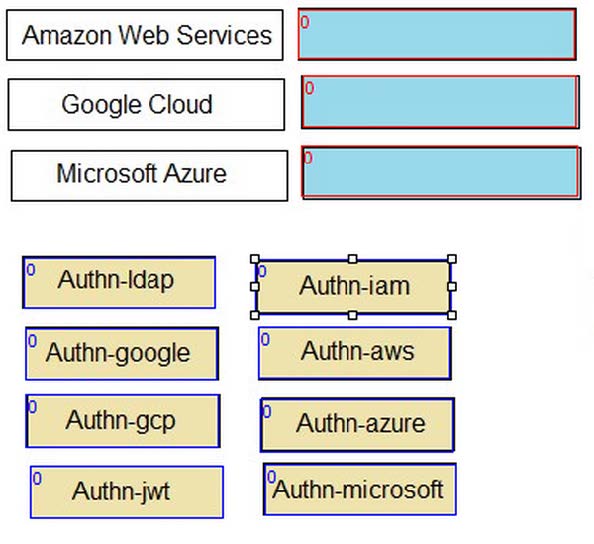
DRAG DROP
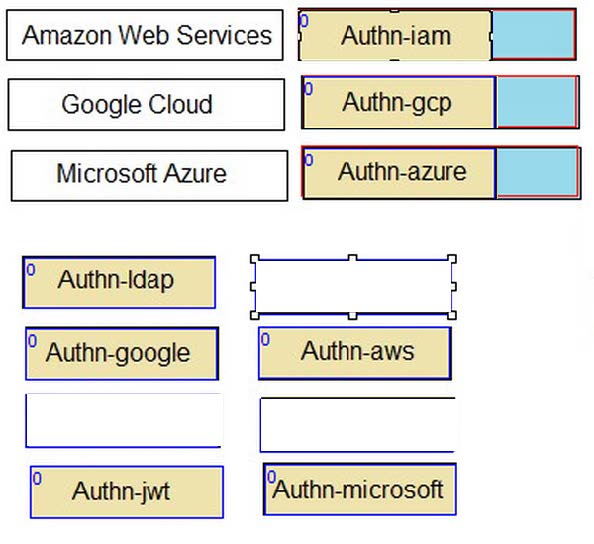
Match each cloud platform to the correct Conjur authenticator.
Select and Place:
DRAG DROP
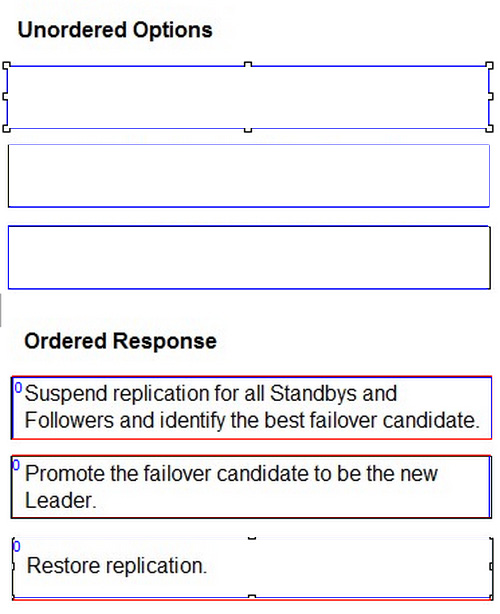
Arrange the manual failover configuration steps in the correct sequence.
Select and Place:

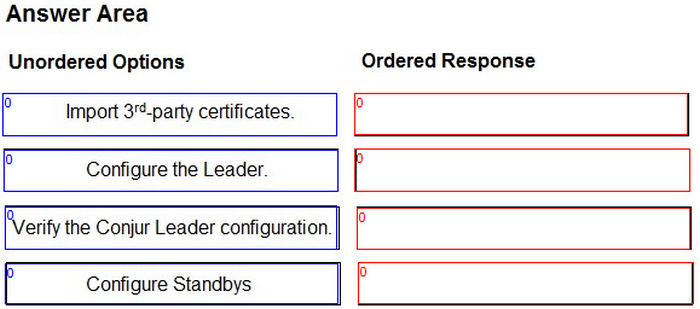
DRAG DROP
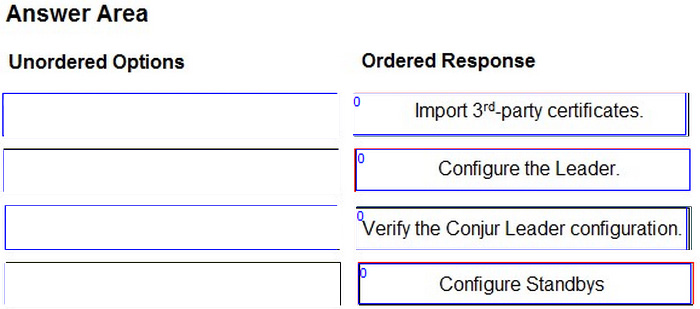
You are configuring the Conjur Cluster with 3rd-party certificates.
Arrange the steps to accomplish this in the correct sequence.
Select and Place:
DRAG DROP
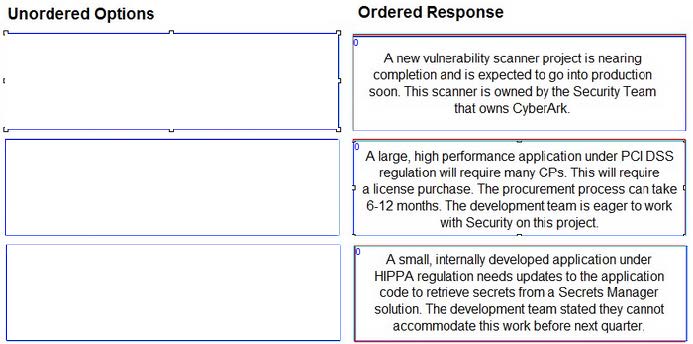
Findings were obtained after cataloging pending Secrets Manager use cases.
Arrange the findings in the correct order for prioritization.
Select and Place:

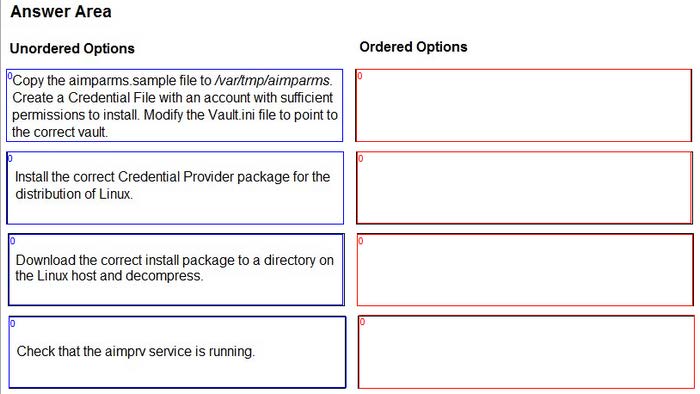
DRAG DROP
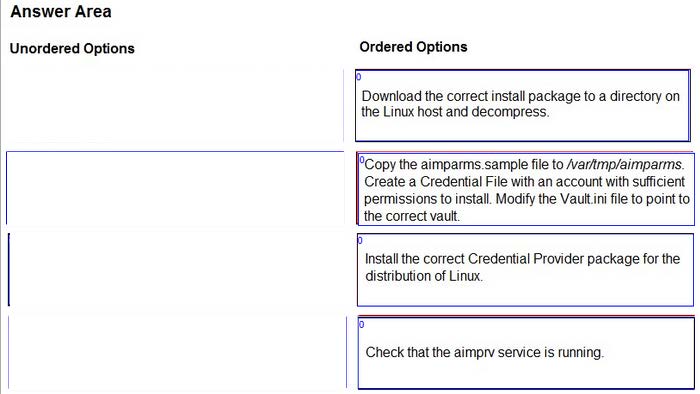
You are installing a Credential Provider on a Linux host. Arrange the installation steps in the correct sequence.
Select and Place:
DRAG DROP
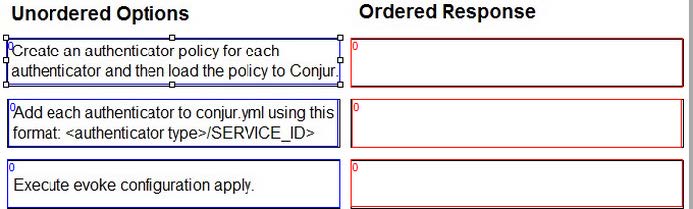
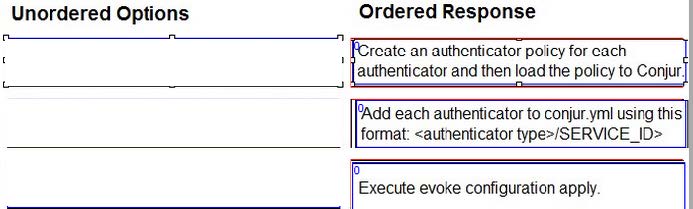
Arrange the steps to configure authenticators in the correct the sequence.
Select and Place: