SC-400 Online Practice Questions and Answers
You are creating a custom trainable classifier to identify organizational product codes referenced in Microsoft 365 content.
You identify 300 files to use as seed content.
Where should you store the seed content?
A. a Microsoft SharePoint Online folder
B. a Microsoft OneDrive for Business folder
C. an Azure file share
D. Microsoft Exchange Online shared mailbox
You need to ensure that documents in a Microsoft SharePoint Online site that contain a reference to Project Alpha are retained for two years, and then deleted.
Which two objects should you create? Each correct answer presents part of the solution. (Choose two.)
NOTE: Each correct selection is worth one point.
A. a retention policy
B. an auto-apply label policy
C. a sensitive info type
D. a retention label
E. a sensitivity label
F. a publishing label policy
You need to test Microsoft Office 365 Message Encryption (OME) capabilities for your company. The test must verify the following information:
1.
The acquired default template names
2.
The encryption and decryption verification status Which PowerShell cmdlet should you run?
A. Test-ClientAccessRule
B. Test-Mailflow
C. Test-OAuthConnectivity
D. Test-IRMConfiguration
You have a Microsoft 365 tenant that uses trainable classifiers.
You are creating a custom trainable classifier.
You collect 300 sample file types from various geographical locations to use as seed content. Some of the file samples are encrypted.
You organize the files into categories as shown in the following table.
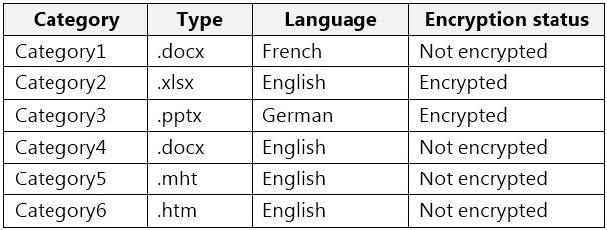
Which file categories can be used as seed content?
A. Category2, Category3, and Category5 only
B. Category1 and Category3 only
C. Category4 and Category6 only
D. Category4 and Category5 only
You need to protect documents that contain credit card numbers from being opened by users outside your company. The solution must ensure that users at your company can open the documents. What should you use?
A. a sensitivity label policy
B. a sensitivity label
C. a retention policy
D. a data loss prevention (DLP) policy
You have a Microsoft 365 subscription that contains a user named User1.
You need to assign User1 permissions to search Microsoft Office 365 audit logs.
What should you use?
A. the Azure Active Directory admin center
B. the Microsoft Purview compliance portal
C. the Exchange admin center
D. the Microsoft 365 Defender portal
You have a Microsoft 365 subscription.
The Global Administrator role is assigned to your user account.
You have a user named Admin1.
You create an eDiscovery case named Case1.
You need to ensure that Admin1 can view the results of Case1.
What should you do first?
A. From the Microsoft Entra admin center, assign a role group to Admin1.
B. From the Microsoft Purview compliance portal, assign a role group to Admin1.
C. From the Microsoft 365 admin center, assign a role to Admin1.
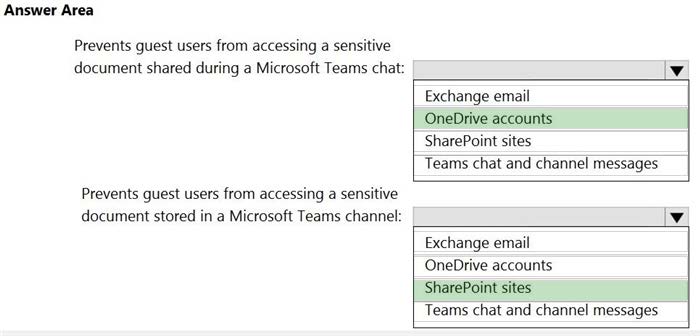
HOTSPOT
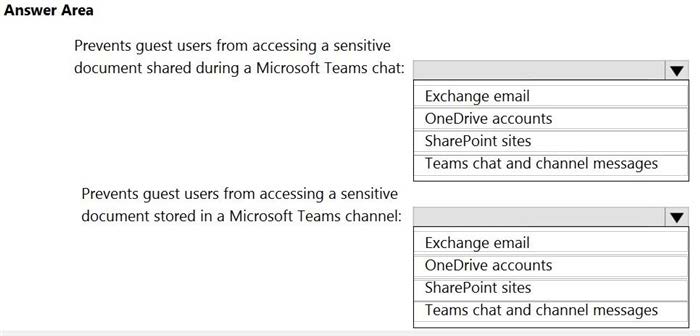
You create a data loss prevention (DLP) policy that meets the following requirements:
1.
Prevents guest users from accessing a sensitive document shared during a Microsoft Teams chat
2.
Prevents guest users from accessing a sensitive document stored in a Microsoft Teams channel
Which location should you select for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
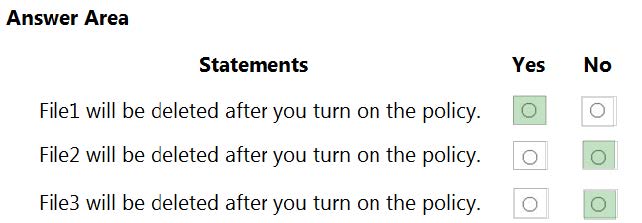
HOTSPOT
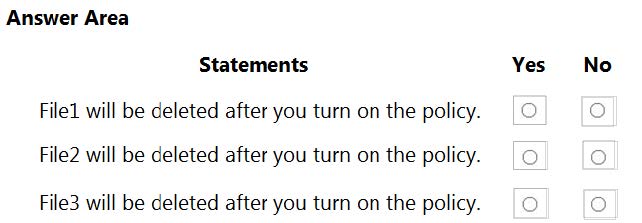
You have the files shown in the following table.
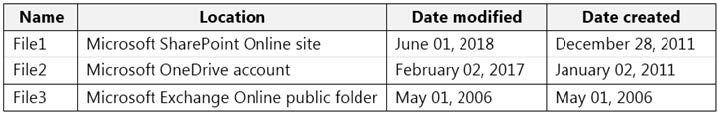
You configure a retention policy as shown in the exhibit.
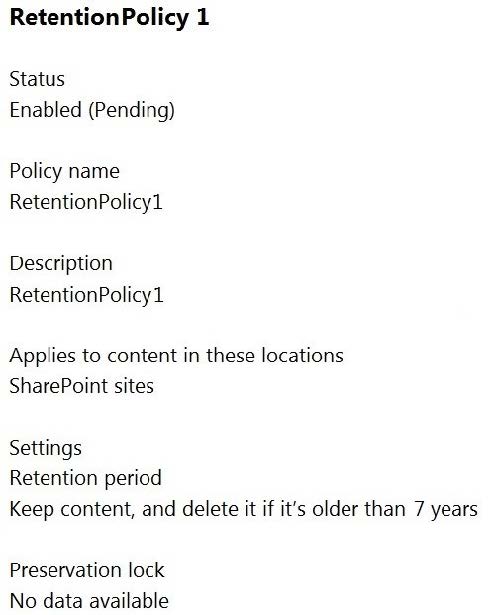
The start of the retention period is based on when items are created. The current date is January 01, 2021.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
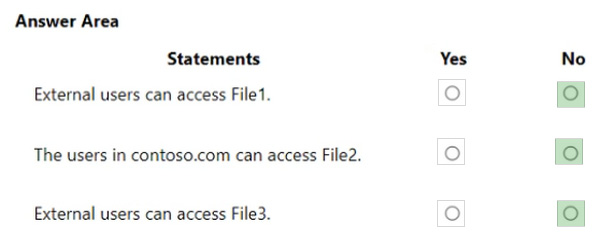
HOTSPOT
You have a Microsoft 365 subscription that uses an Azure AD tenant named contoso.com.
OneDrive stores files that are shared with external users. The files are configured as shown in the following table.
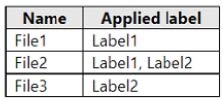
You create a data loss prevention (DLP) policy that applies to the content stored in OneDrive accounts. The policy contains the following three rules:
Rule1
1.
Conditions: Label1, Detect content that's shared with people outside my organization
2.
Actions: Restrict access to the content for external users
3.
User notifications: Notify the user who last modified the content
4.
User overrides: On
5.
Priority: 0
Rule2:
1.
Conditions: Label1 or Label2
2.
Actions: Restrict access to the content
3.
Priority: 1
Rule3:
1.
Conditions: Label2, Detect content that's shared with people outside my organization
2.
Actions: Restrict access to the content for external users
3.
User notifications: Notify the user who last modified the content
4.
User overrides: On
5.
Priority: 2
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

HOTSPOT
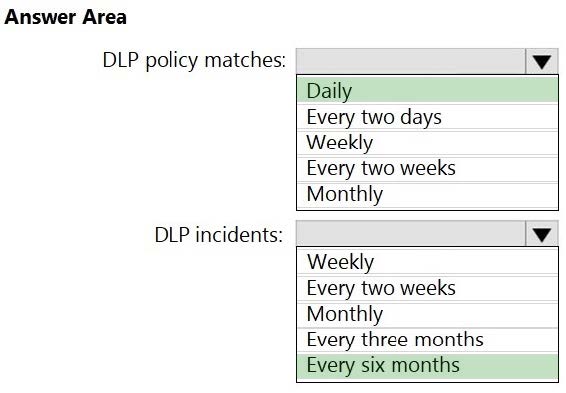
You have a Microsoft 365 E5 subscription that uses data loss prevention (DLP) to protect sensitive information.
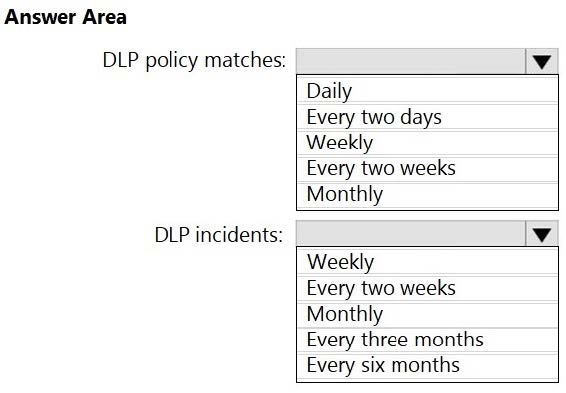
You need to create scheduled reports that generate:
1.
DLP policy matches reported over the shortest frequency of time
2.
DLP incidents reported over the longest frequency of time
Which frequency should you configure for each report? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
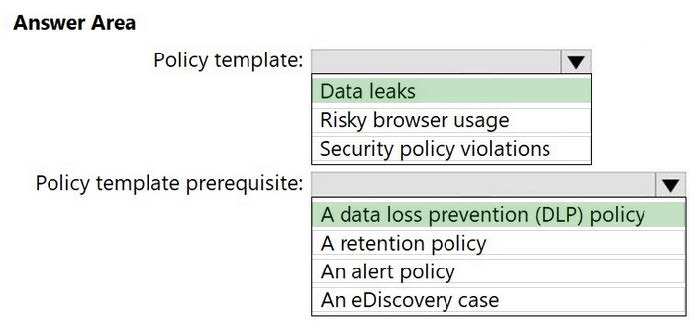
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You need to deploy a compliance solution that will detect the accidental oversharing of information outside of an organization. The solution must minimize administrative effort.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
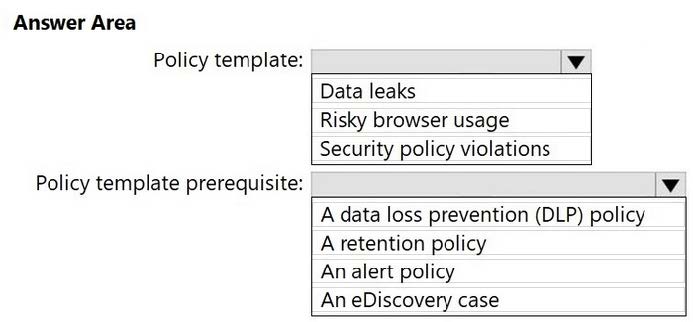
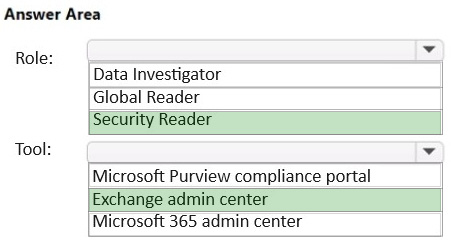
HOTSPOT
You plan to provide a user named User1 with the ability to view data loss prevention (DLP) reports.
You need to identify the following:
1.
Which role you should assign to User1
2.
Which tool you should use to assign the role
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

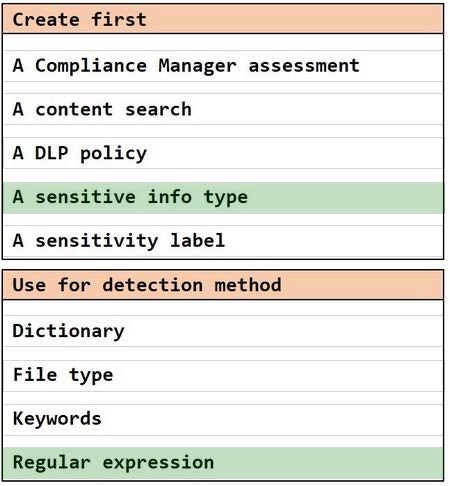
HOTSPOT
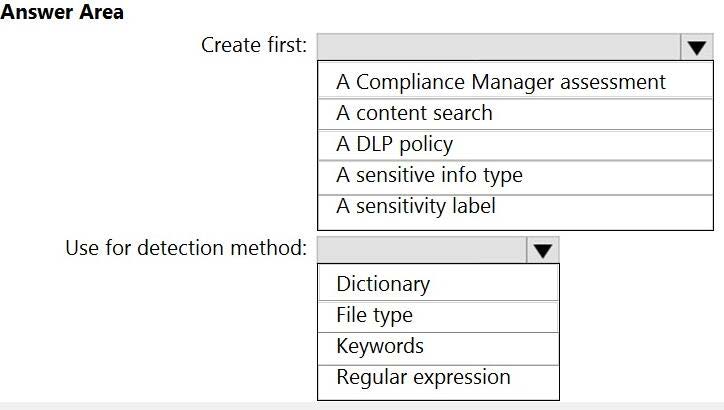
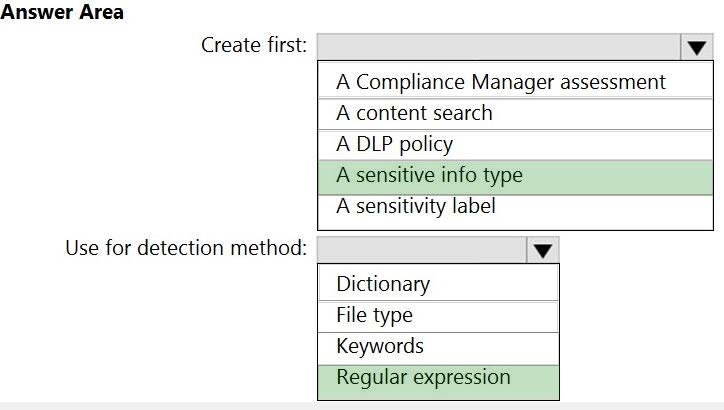
You need to meet the technical requirements for the confidential documents.
What should you created first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
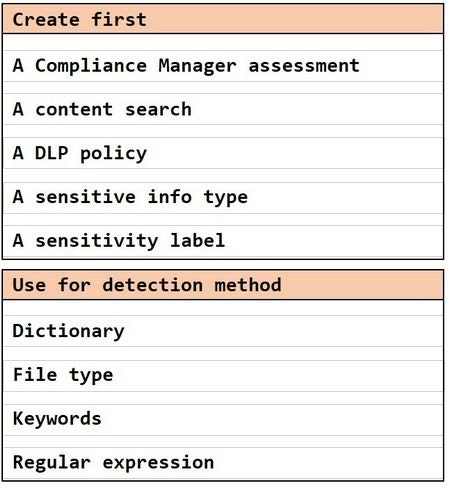
HOTSPOT
You need to meet the technical requirements for the confidential documents.
What should you create first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: