SC-300 Online Practice Questions and Answers
HOTSPOT
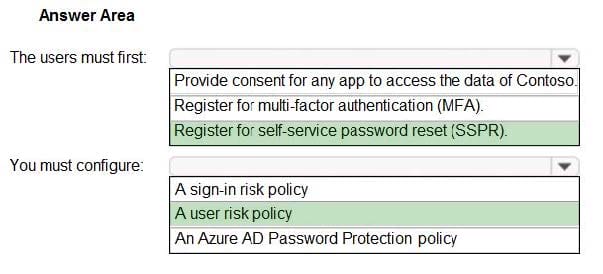
You need to meet the technical requirements for the probability that user identities were compromised.
What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Hot Area:
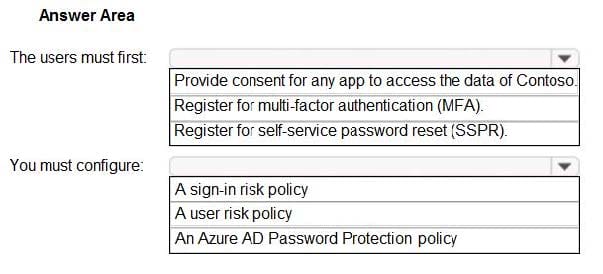
You need to resolve the recent security incident issues.
What should you configure for each incident? To answer, drag the appropriate policy types to the correct issues. Each policy type may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

You have an Azure Active Directory (Azure AD) tenant named contoso.com that has Azure AD Identity Protection policies enforced.
You create an Azure Sentinel instance and configure the Azure Active Directory connector.
You need to ensure that Azure Sentinel can generate incidents based on the risk alerts raised by Azure AD Identity Protection.
What should you do first?
A. Add an Azure Sentinel data connector.
B. Configure the Notify settings in Azure AD Identity Protection.
C. Create an Azure Sentinel playbook.
D. Modify the Diagnostics settings in Azure AD.
Your network contains an on-premises Active Directory domain that syncs to an Azure Active Directory (Azure AD) tenant. The tenant contains the users shown in the following table.
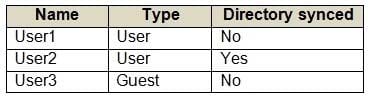
All the users work remotely.
Azure AD Connect is configured in Azure AD as shown in the following exhibit.
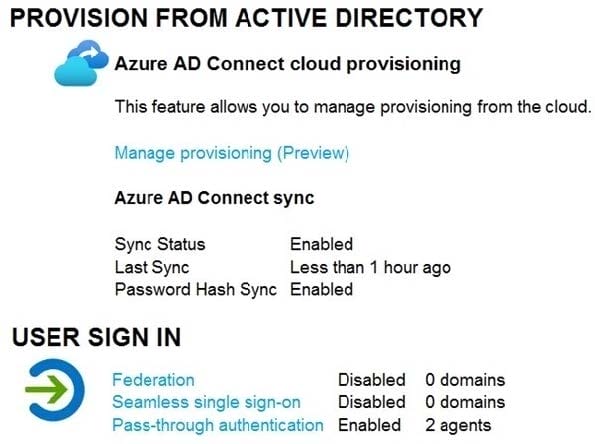
Connectivity from the on-premises domain to the internet is lost. Which users can sign in to Azure AD?
A. User1 and User3 only
B. User1 only
C. User1, User2, and User3
D. User1 and User2 only
You have a Microsoft 365 tenant.
The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain. The domain contains the servers shown in the following table.
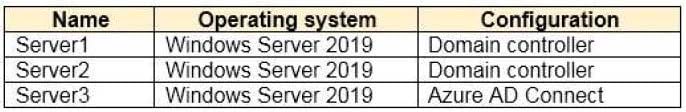
The domain controllers are prevented from communicating to the internet.
You implement Azure AD Password Protection on Server1 and Server2.
You deploy a new server named Server4 that runs Windows Server 2019.
You need to ensure that Azure AD Password Protection will continue to work if a single server fails.
What should you implement on Server4?
A. Azure AD Connect
B. Azure AD Application Proxy
C. Password Change Notification Service (PCNS)
D. the Azure AD Password Protection proxy service
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant.
You have 100 IT administrators who are organized into 10 departments.
You create the access review shown in the exhibit. (Click the Exhibit tab.)
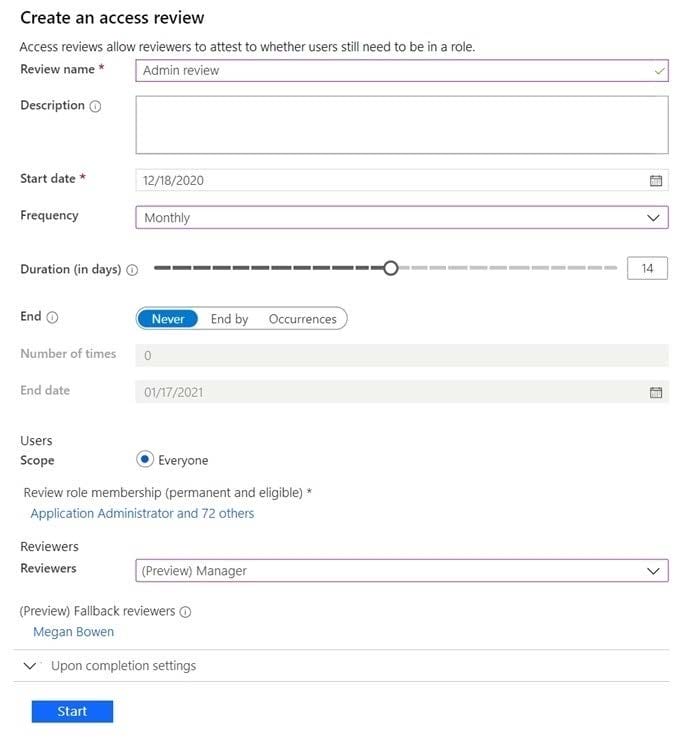
You discover that all access review requests are received by Megan Bowen.
You need to ensure that the manager of each department receives the access reviews of their respective department.
Solution: You modify the properties of the IT administrator user accounts.
Does this meet the goal?
A. Yes
B. No
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
All users who run applications registered in Azure AD are subject to conditional access policies.
You need to prevent the users from using legacy authentication.
What should you include in the conditional access policies to filter out legacy authentication attempts?
A. a cloud apps or actions condition
B. a user risk condition
C. a client apps condition
D. a sign-in risk condition
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps and Conditional Access policies.
You need to block access to cloud apps when a user is assessed as high risk.
Which type of policy should you create in the Microsoft Defender for Cloud Apps portal?
A. access policy
B. OAuth app policy
C. anomaly detection policy
D. activity policy
You create a conditional access policy that blocks access when a user triggers a high-severity sign-in alert. You need to test the policy under the following conditions:
1.
A user signs in from another country.
2.
A user triggers a sign-in risk. What should you use to complete the test?
A. the Conditional Access What If tool
B. sign-ins logs in Azure Active Directory (Azure AD)
C. the activity logs in Microsoft Defender for Cloud Apps
D. access reviews in Azure Active Directory (Azure AD)
You have a Microsoft 365 ES subscription that contains a user named User1. User1 is eligible for the Application administrator role.
User1 needs to configure a new connector group for an application proxy.
What should you to activate the role for User1?
A. the Microsoft Defender for Cloud Apps portal
B. the Microsoft 365 admin center
C. the Azure Active Directory admin center
D. the Microsoft 365 Defender portal
You need to resolve the issue of IT.Group1. What should you do first?
A. Recreate the IT_Group 1 group.
B. Change Membership type of IT.Group1 to Dynamic Device.
C. Add an owner to IT_Group1.
D. Change Membership type of IT.Group1 to Dynamic User.
You need to track application access assignments by using Identity Governance. The solution must meet the delegation requirements. What should you do first?
A. Modify the User consent settings for the enterprise applications.
B. Create a catalog.
C. Create a program.
D. Modify the Admin consent requests settings for the enterprise applications.
You need to configure the detection of multi staged attacks to meet the monitoring requirements. What should you do?
A. Customize the Azure Sentinel rule logic.
B. Create a workbook.
C. Add an Azure Sentinel playbook.
D. Add Azure Sentinel data connectors.
You need to sync the ADatum users. The solution must meet the technical requirements. What should you do?
A. From the Microsoft Azure Active Directory Connect wizard, select Customize synchronization options.
B. From PowerShell, run Set-ADSyncScheduler.
C. From PowerShell, run Start-ADSyncSyncCycle.
D. From the Microsoft Azure Active Directory Connect wizard, select Change user sign-in.
You need to meet the planned changes for the User administrator role. What should you do?
A. Create an access review.
B. Create an administrative unit.
C. Modify Active assignments.
D. Modify Role settings.