SC-200 Online Practice Questions and Answers
You need to minimize the effort required to investigate the Microsoft Defender for Identity false positive alerts. What should you review?
A. the status update time
B. the resolution method of the source computer
C. the alert status
D. the certainty of the source computer
You need to implement the Defender for Cloud requirements. Which subscription-level role should you assign to Group1?
A. Security Admin
B. Owner
C. Security Assessment Contributor
D. Contributor
You are investigating a potential attack that deploys a new ransomware strain.
You plan to perform automated actions on a group of highly valuable machines that contain sensitive information.
You have three custom device groups.
You need to be able to temporarily group the machines to perform actions on the devices.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Add a tag to the device group.
B. Add the device users to the admin role.
C. Add a tag to the machines.
D. Create a new device group that has a rank of 1.
E. Create a new admin role.
F. Create a new device group that has a rank of 4.
You use Azure Sentinel.
By using a built-in role, you have to provide a security analyst with the ability to edit the queries of custom Azure Sentinel workbooks.
Which role should you assign to the analyst if using the principle of least privilege ?
A. Security Administrator
B. Azure Sentinel Responder
C. Azure Sentinel Contributor
D. Logic App Contributor
You have the following environment:
1.
Azure Sentinel
2.
A Microsoft 365 subscription
3.
Microsoft Defender for Identity
4.
An Azure Active Directory (Azure AD) tenant
You configure Azure Sentinel to collect security logs from all the Active Directory member servers and domain controllers.
You deploy Microsoft Defender for Identity by using standalone sensors.
You need to ensure that you can detect when sensitive groups are modified in Active Directory.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Configure the Advanced Audit Policy Configuration settings for the domain controllers.
B. Modify the permissions of the Domain Controllers organizational unit (OU).
C. Configure auditing in the Microsoft 365 compliance center.
D. Configure Windows Event Forwarding on the domain controllers.
You have a Microsoft Sentinel workspace.
You receive multiple alerts for failed sign in attempts to an account.
You identify that the alerts are false positives.
You need to prevent additional failed sign-in alerts from being generated for the account. The solution must meet the following requirements:
1.
Ensure that failed sign-in alerts are generated for other accounts.
2.
Minimize administrative effort What should do?
A. Create an automation rule.
B. Create a watchlist.
C. Modify the analytics rule.
D. Add an activity template to the entity behavior.
You have a Microsoft Sentinel workspace.
You need to identify which rules are used to detect advanced multistage attacks that comprise two or more alerts or activities. The solution must minimize administrative effort.
Which rule type should you query?
A. Fusion
B. Microsoft Security
C. ML Behavior Analytics
D. Scheduled
You have a Microsoft Sentinel workspace named Workspace1 and 200 custom Advanced Security Information Model (ASIM) parsers based on the DNS schema.
You need to make the 200 parses available in Workspace1. The solution must minimize administrative effort.
What should you do first?
A. Copy the parsers to the Azure Monitor Logs page.
B. Create a JSON file based on the DNS template.
C. Create an XML file based on the DNS template.
D. Create a YAML file based on the DNS template.
You have an Azure subscription that uses Microsoft Defender for Servers Plan 1 and contains a server named Server1.
You enable agentless scanning.
You need to prevent Server1 from being scanned. The solution must minimize administrative effort.
What should you do?
A. Create an exclusion tag.
B. Upgrade the subscription to Defender for Servers Plan 2.
C. Create a governance rule.
D. Create an exclusion group.
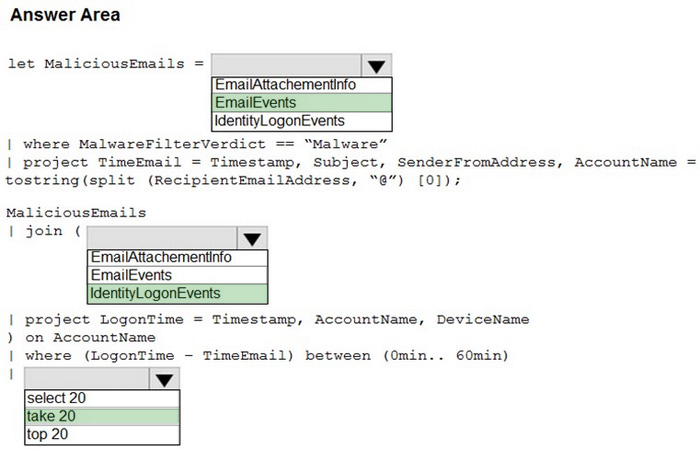
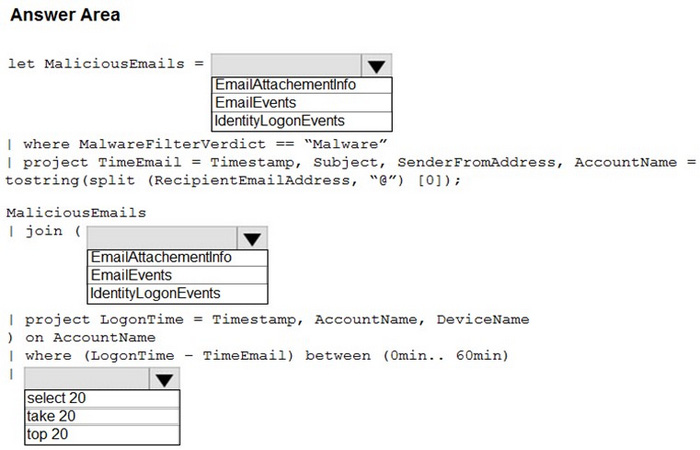
HOTSPOT
You are informed of an increase in malicious email being received by users.
You need to create an advanced hunting query in Microsoft 365 Defender to identify whether the accounts of the email recipients were compromised. The query must return the most recent 20 sign-ins performed by the recipients within an
hour of receiving the known malicious email.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
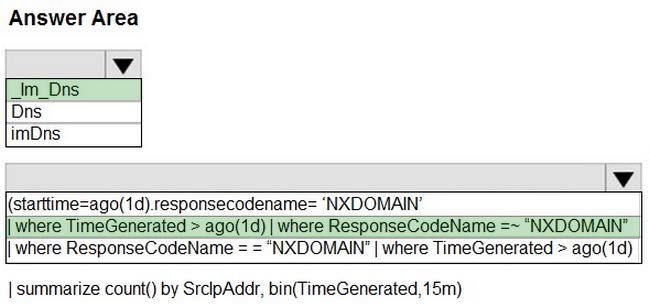
HOTSPOT
You have a Microsoft Sentinel workspace named Workspace1.
You configure Workspace1 to collect DNS events and deploy the Advanced Security Information Model (ASIM) unifying parser for the DNS schema.
You need to query the ASIM DNS schema to list all the DNS events from the last 24 hours that have a response code of ‘NXDOMAIN
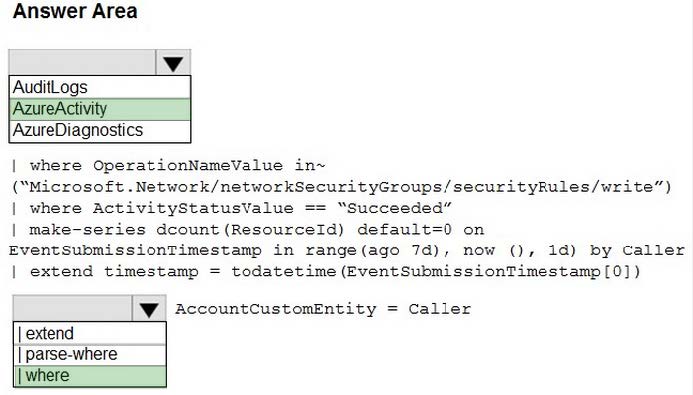
HOTSPOT
You have an Azure subscription that contains an Microsoft Sentinel workspace.
You need to create a hunting query using Kusto Query Language (KQL) that meets the following requirements:
1.
Identifies an anomalous number of changes to the rules of a network security group (NSG) made by the same security principal
2.
Automatically associates the security principal with an Microsoft Sentinel entity
How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Hot Area:

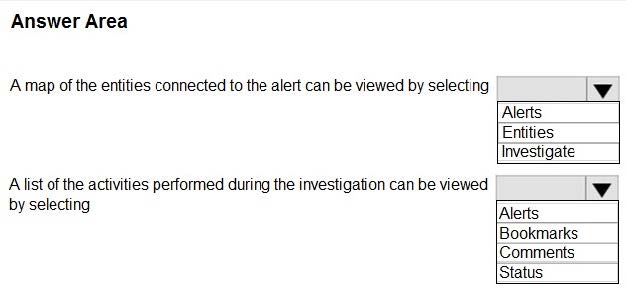
HOTSPOT
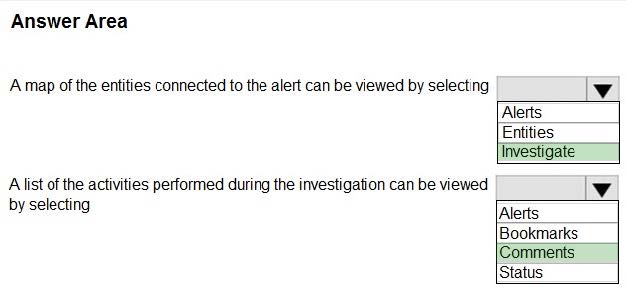
You have a Microsoft Sentinel workspace.
A Microsoft Sentinel incident is generated as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
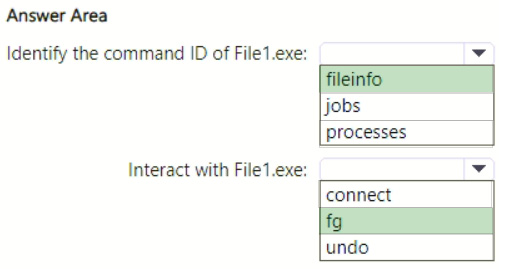
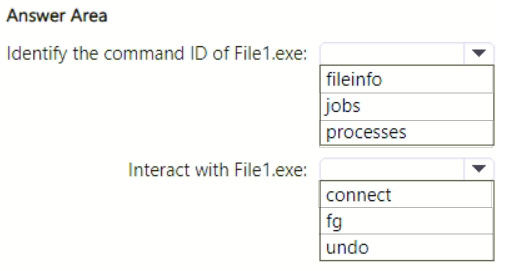
HOTSPOT
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a Windows device named Device1.
You initiate a live response session on Device1 and launch an executable file named File1.exe in the background.
You need to perform the following actions:
1.
Identify the command ID of File1.exe.
2.
Interact with File1.exe.
Which live response command should you run for each action? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
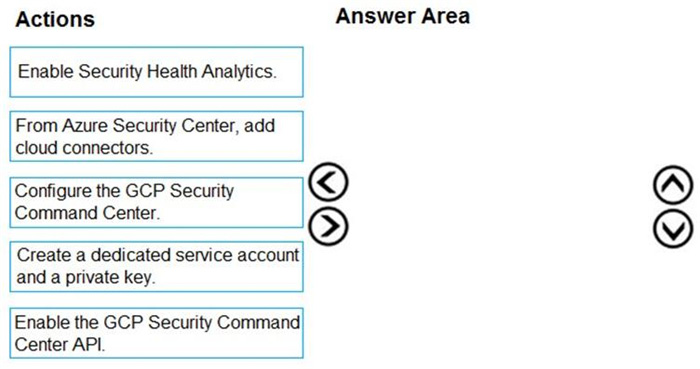
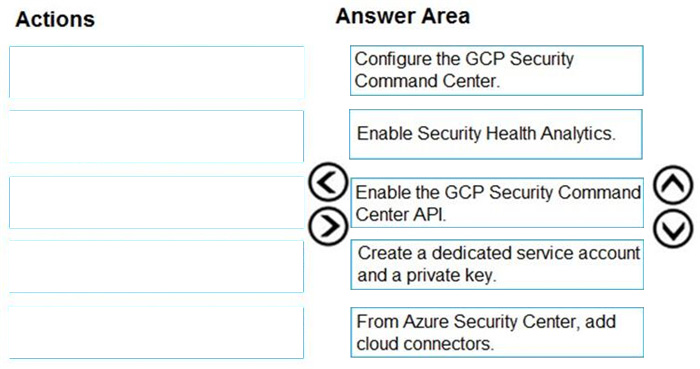
DRAG DROP
You have resources in Azure and Google cloud.
You need to ingest Google Cloud Platform (GCP) data into Azure Defender.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: