PT0-001 Online Practice Questions and Answers
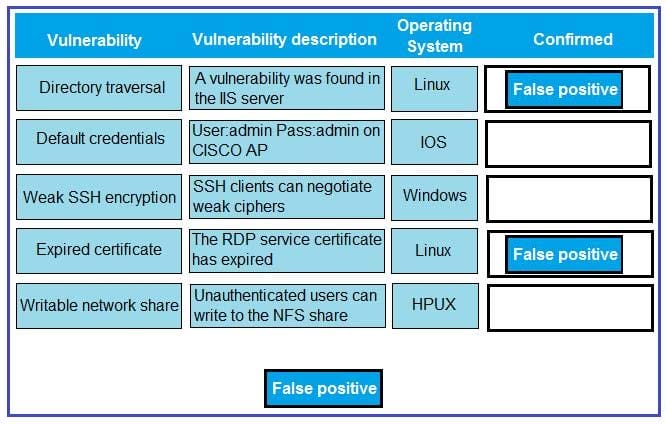
DRAG DROP
A technician is reviewing the following report. Given this information, identify which vulnerability can be definitively confirmed to be a false positive by dragging the “false positive” token to the “Confirmed” column for each vulnerability that is a false positive.
Select and Place:
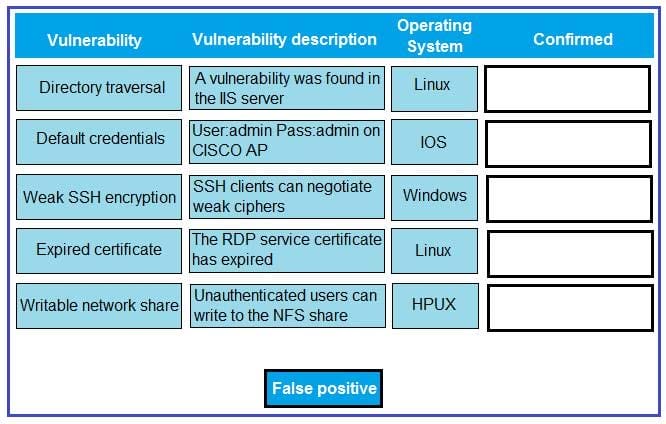
A penetration tester reviews the scan results of a web application. Which of the following vulnerabilities is MOST critical and should be prioritized for exploitation?
A. Stored XSS
B. Fill path disclosure
C. Expired certificate
D. Clickjacking
Given the following Python script:
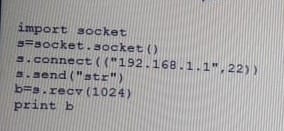
Which of the following actions will it perform?
A. ARP spoofing
B. Port scanner
C. Reverse shell
D. Banner grabbing
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
Code review Updates to firewall setting
A. Scope creep
B. Post-mortem review
C. Risk acceptance
D. Threat prevention
A security guard observes an individual entering the building after scanning a badge. The facility has a strict badge-in and badge-out requirement with a turnstile. The security guard then audits the badge system and finds two log entries for the badge.
A. The badge was cloned.
B. The physical access control server is malfunctioning
C. The system reached the crossover error rate.
D. The employee lost the badge.
Which of the following can be used to perform online password attacks against RDP?
A. Hashcat
B. John the Rippef
C. Aircrack-ng
D. Ncrack
Which of the following BEST describes the difference between a red team engagement and a penetration test?
A. A penetration test has a broad scope and emulates advanced persistent threats while a red team engagement has a limited scope and focuses more on vulnerability identification
B. A red team engagement has a broad scope and emulates advanced persistent threats, while a penetration test has a limited scope and focuses more on vulnerability identification
C. A red team engagement has a broad scope and focuses more on vulnerability identification, while a penetration test has a limited scope and emulates advanced persistent threats
D. A penetration test has a broad scope and focuses more on vulnerability identification while a red team engagement has a limited scope and emulates advanced persistent threats
A penetration tester is exploiting the use of default public and private community strings Which of the following protocols is being exploited?
A. SMTP
B. DNS
C. SNMP
D. HTTP
A penetration tester has been assigned to perform an external penetration assessment of a company. Which of the following steps would BEST help with the passive-information-gathering process? (Choose two.)
A. Wait outside of the company's building and attempt to tailgate behind an employee.
B. Perform a vulnerability scan against the company's external netblock, identify exploitable vulnerabilities, and attempt to gain access.
C. Use domain and IP registry websites to identify the company's external netblocks and external facing applications.
D. Search social media for information technology employees who post information about the technologies they work with.
E. Identify the company's external facing webmail application, enumerate user accounts and attempt password guessing to gain access.
A penetration tester has performed a vulnerability scan of a specific host that contains a valuable database and has identified the following vulnerabilities:
1.
XSS
2.
HTTP DELETE method allowed
3.
SQL injection
4.
Vulnerable to CSRF
To which of the following should the tester give the HIGHEST priority?
A. SQL injection
B. HTTP DELETE method allowed
C. Vulnerable to CSRF
D. XSS
During a penetration test, a tester identifies traditional antivirus running on the exploited server. Which of the following techniques would BEST ensure persistence in a post-exploitation phase?
A. Shell binary placed in C:\windows\temp
B. Modified daemons
C. New user creation
D. Backdoored executables
A tester was able to retrieve domain users' hashes. Which of the following tools can be used to uncover the users' passwords? (Choose two.)
A. Hydra
B. Mimikatz
C. Hashcat
D. John the Ripper
E. PSExec
F. Nessus
A penetration tester has successfully exploited a Windows host with low privileges and found directories with the following permissions:
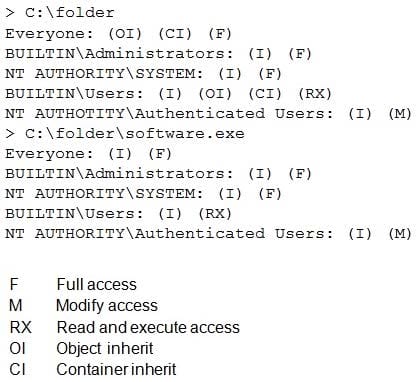
Which of the following should be performed to escalate the privileges?
A. Kerberoasting
B. Retrieval of the SAM database
C. Migration of the shell to another process
D. Writable services
Which of the following is the BEST way to deploy vulnerability scanners with many networks segmented by firewalls with active IPS rules?
A. Deploy a single scanner inside each network segment.
B. Deploy many scanners inside one segment and allow any rules.
C. Deploy one internal scanner and one external scanner.
D. Deploy one internal scanner with heavy server resources.
A penetration tester reported the following vulnerabilities:

Which of the following is the correct order to rate the vulnerabilities from critical to low considering the MOST immediate impact?
A. Unrestricted file upload, stored XSS, SQL injection, verbose server headers
B. SQL injection, unrestricted file upload, stored XSS, verbose server headers
C. Verbose server headers, unrestricted file upload, stored XSS, SQL injection
D. Stored XSS, SQL injection, unrestricted file upload, verbose server headers