PCNSA Online Practice Questions and Answers
In which stage of the Cyber-Attack Lifecycle would the attacker inject a PDF file within an email?
A. Weaponization
B. Reconnaissance
C. Installation
D. Command and Control
E. Exploitation
Given the screenshot what two types of route is the administrator configuring? (Choose two )
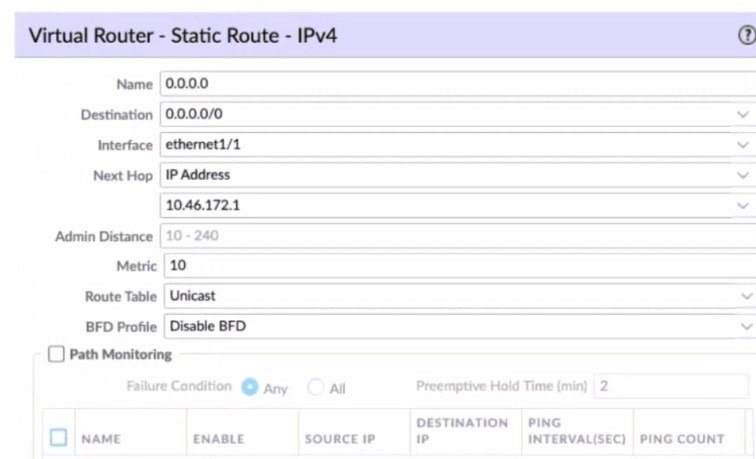
A. default route
B. OSPF
C. BGP
D. static route
Which file is used to save the running configuration with a Palo Alto Networks firewall?
A. running-config.xml
B. run-config.xml
C. running-configuration.xml
D. run-configuratin.xml
What is the function of an application group object?
A. It contains applications that you want to treat similarly in policy
B. It groups applications dynamically based on application attributes that you define
C. It represents specific ports and protocols for an application
D. It identifies the purpose of a rule or configuration object and helps you better organize your rulebase
A network administrator is required to use a dynamic routing protocol for network connectivity.
Which three dynamic routing protocols are supported by the NGFW Virtual Router for this purpose? (Choose three.)
A. RIP
B. OSPF
C. IS-IS
D. EIGRP
E. BGP
Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
A. outbound
B. north south
C. inbound
D. east west
You receive notification about new malware that is being used to attack hosts The malware exploits a software bug in a common application. Which Security Profile detects and blocks access to this threat after you update the firewall's threat signature database?
A. Data Filtering Profile applied to outbound Security policy rules
B. Antivirus Profile applied to outbound Security policy rules
C. Data Filtering Profile applied to inbound Security policy rules
D. Vulnerability Profile applied to inbound Security policy rules
What does an application filter help you to do?
A. It dynamically provides application statistics based on network, threat, and blocked activity,
B. It dynamically filters applications based on critical, high, medium, low. or informational severity.
C. It dynamically groups applications based on application attributes such as category and subcategory.
D. It dynamically shapes defined application traffic based on active sessions and bandwidth usage.
Which path is used to save and load a configuration with a Palo Alto Networks firewall?
A. Device>Setup>Services
B. Device>Setup>Management
C. Device>Setup>Operations
D. Device>Setup>Interfaces
An administrator needs to allow users to use their own office applications.
How should the administrator configure the firewall to allow multiple applications in a dynamic environment?
A. Create an Application Filter and name it Office Programs, the filter it on the business- systems category, office-programs subcategory
B. Create an Application Group and add business-systems to it
C. Create an Application Filter and name it Office Programs, then filter it on the business- systems category
D. Create an Application Group and add Office 365, Evernote, Google Docs, and Libre Office
Which dataplane layer of the graphic shown provides pattern protection for spyware and vulnerability exploits on a Palo Alto Networks Firewall?
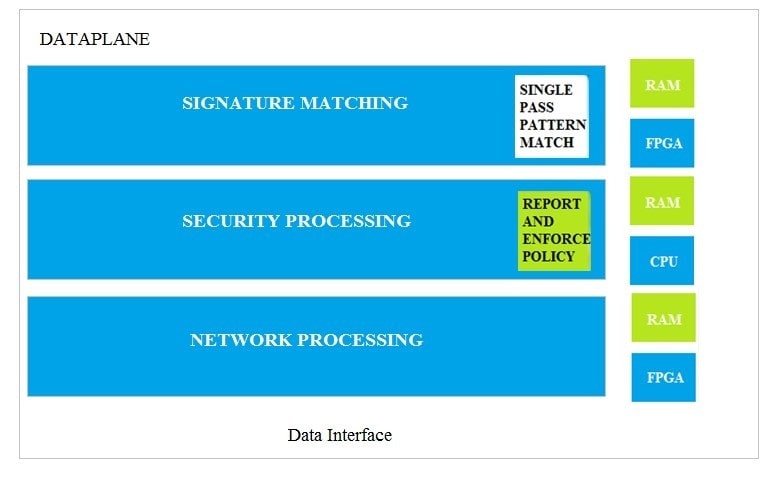
A. Signature Matching
B. Network Processing
C. Security Processing
D. Security Matching
How many zones can an interface be assigned with a Palo Alto Networks firewall?
A. two
B. three
C. four
D. one
When creating an address object, which option is available to select from the Type drop-down menu?
A. IPv6 Address
B. IP Netmask
C. IPv4 Address
D. IP Address Class
Which two statements correctly describe how pre-rules and local device rules are viewed and modified? (Choose two.)
A. Pre-rules can be modified by the local administrator or by a Panorama administrator who has switched to a local firewall.
B. Pre-rules and local device rules can be modified in Panorama.
C. Pre-rules can be viewed on managed firewalls.
D. Pre-rules are modified in Panorama only, and local device rules are modified on local firewalls only.
Which two features implement one-to-one translation of a source IP address while allowing the source port to change? (Choose two.)
A. Dynamic IP
B. Dynamic IP and Port (DIPP)
C. Static IP
D. Dynamic IP / Port Fallback
