PAM-DEF Online Practice Questions and Answers
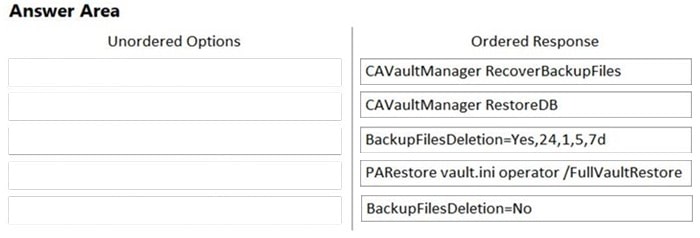
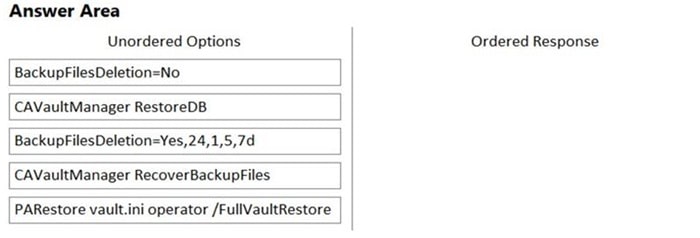
DRAG DROP
Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.
Select and Place:
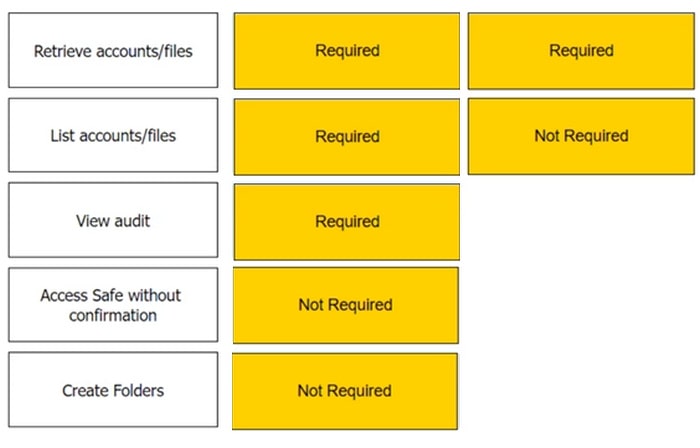
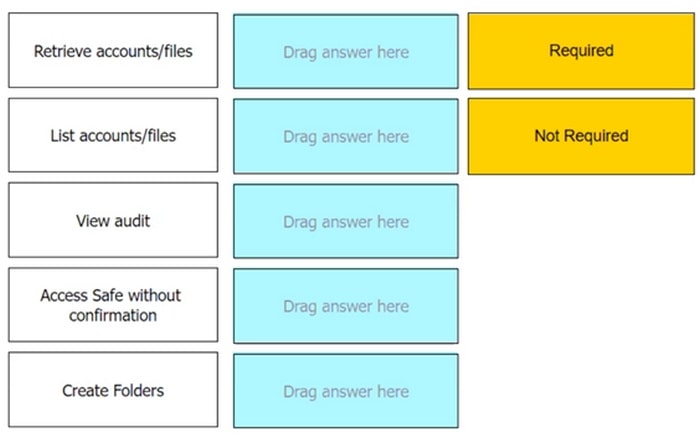
DRAG DROP
Which authorizations are required in a recording safe to allow a group to view recordings?
Select and Place:
Which report shows the accounts that are accessible to each user?
A. Activity report
B. Entitlement report
C. Privileged Accounts Compliance Status report
D. Applications Inventory report
When managing SSH keys, the CPM stores the Public Key
A. In the Vault
B. On the target server
C. A and B
D. Nowhere because the public key can always be generated from the private key.
Within the Vault each password is encrypted by:
A. the server key
B. the recovery public key
C. the recovery private key
D. its own unique key
One can create exceptions to the Master Policy based on ____________________.
A. Safes
B. Platforms
C. Policies
D. Accounts
Platform settings are applied to _________.
A. The entire vault.
B. Network Areas
C. Safes
D. Individual Accounts
How does the Vault administrator apply a new license file?
A. Upload the license.xml file to the system Safe and restart the PrivateArk Server service
B. Upload the license.xml file to the system Safe
C. Upload the license.xml file to the Vault Internal Safe and restart the PrivateArk Server service
D. Upload the license.xml file to the Vault Internal Safe
Which tools can you use to identify the machines and accounts that create the highest risk and are exposed to lateral movement? (Choose two.)
A. Accounts Discovery Feed
B. CyberArk DNA Report
C. REST API Scripts
D. CyberArk DNA Map
E. Get-LocalUser Powershell cmdlet
Where can you check that the LDAP binding is using TCP/636?
A. in Active Directory under "Users OU" => "User Properties" => "External Bindings" => "Port"
B. in PVWA, under "LDAP Integration" => "LDAP" => "Directories" => "" => "Hosts" => "Host"
C. in PrivateArk Client, under "Tools" => "Administrative Tools" => "Directory Mapping" => ""
D. From the PVWA, connect to the domain controller using Test-NetConnection on Port 636.
What are the mandatory fields when onboarding from Pending Accounts? (Choose two.)
A. Address
B. Safe
C. Account Description
D. Platform
E. CPM
When should vault keys be rotated?
A. when it is copied to file systems outside the vault
B. annually
C. whenever a CyberArk user leaves the organization
D. when migrating to a new data center
A password compliance audit found:
1) One-time password access of 20 domain accounts that are members of Domain Admins group in Active Directory are not being enforced.
2) All the sessions of connecting to domain controllers are not being recorded by CyberArk PSM.
What should you do to address these findings?
A. Edit the Master Policy and add two policy exceptions: enable "Enforce one-time password access", enable "Record and save session activity".
B. Edit safe properties and add two policy exceptions: enable "Enforce one-time password access", enable "Record and save session activity".
C. Edit CPM Settings and add two policy exceptions: enable "Enforce one-time password access", enable "Record and save session activity".
D. Contact the Windows Administrators and request them to add two policy exceptions at Active Directory Level: enable "Enforce one-time password access", enable "Record and save session activity".
Which command configures email alerts within PTA if settings need to be changed post install?
A. /opt/tomcat/utility/emailConfiguration.sh
B. /opt/PTA/emailConfiguration.sh
C. /opt/PTA/utility/emailConfig.sh
D. /opt/tomcat/utility/emailSetup.sh
PSM for Windows (previously known as "RDP Proxy") supports connections to the following target systems
A. Windows
B. UNIX
C. Oracle
D. All of the above