NSE4_FGT-5.6 Online Practice Questions and Answers
Which of the following statements about the FortiGate application control database are true?
(Choose two.)
Response:
A. The application control database uses TCP port 53 for downloads.
B. The application control database uses a hierarchical structure to organize application signatures.
C. The application control database is part of the IPS signatures database.
D. The application control database updates are included in the free FortiGuard service.
Which of the following statements about application control profile mode are true?
(Choose two.)
Response:
A. It can be configured in either flow-based profile-based or proxy-based FortiOS inspection mode.
B. It cannot be used in conjunction with IPS scanning.
C. It uses flow-based scanning techniques, regardless of the inspection mode used.
D. It can scan only unsecure protocols.
View the exhibit.
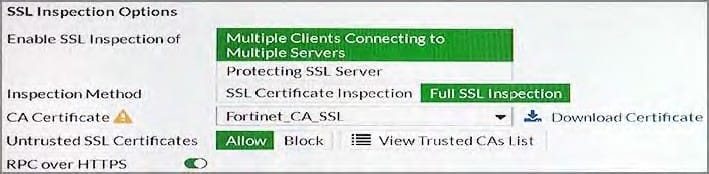
When a user attempts to connect to an HTTPS site, what is the expected result with this configuration? Response:
A. The user is required to authenticate before accessing sites with untrusted SSL certificates.
B. The user is presented with certificate warnings when connecting to sites that have untrusted SSL certificates.
C. The user is allowed access all sites with untrusted SSL certificates, without certificate warnings.
D. The user is blocked from connecting to sites that have untrusted SSL certificates (no exception provided).
Which statements about the firmware upgrade process on an active-active high availability (HA) cluster are
true?
(Choose two.)
Response:
A. The firmware image must be manually uploaded to each FortiGate.
B. Only secondary FortiGate devices are rebooted.
C. Uninterruptable upgrade is enabled by default.
D. Traffic load balancing is temporally disabled while upgrading the firmware.
What is eXtended Authentication (XAuth)? Response:
A. It is an IPsec extension that forces remote VPN users to authenticate using their credentials (user name and password).
B. It is an IPsec extension that authenticates remote VPN peers using digital certificates.
C. It is an IPsec extension that forces remote VPN users to authenticate using their local ID.
D. It is an IPsec extension that authenticates remote VPN peers using a preshared key.
Which file names will match the *.tiff file name pattern configured in a DLP filter?
(Choose two.)
Response:
A. tiff.jpeg
B. tiff.tiff
C. gif.tiff
D. tiff.png
View the Exhibit.

The administrator needs to confirm that FortiGate 2 is properly routing that traffic to the 10.0.1.0/24 subnet.
The administrator needs to confirm it by sending ICMP pings to FortiGate 2 from the CLI of FortiGate 1.
What ping option needs to be enabled before running the ping?
Response:
A. Execute ping-options source port1
B. Execute ping-options source 10.200.1.1.
C. Execute ping-options source 10.200.1.2
D. Execute ping-options source 10.0.1.254
An administrator needs to be able to view logs for application usage on your network. What configurations
are required to ensure that FortiGate generates logs for application usage activity?
(Choose two.)
Response:
A. Enable a web filtering profile on the firewall policy.
B. Create an application control policy.
C. Enable logging on the firewall policy.
D. Enable an application control security profile on the firewall policy.
