MS-203 Online Practice Questions and Answers
HOTSPOT
Your company has a Microsoft Exchange Server 2019 hybrid deployment.
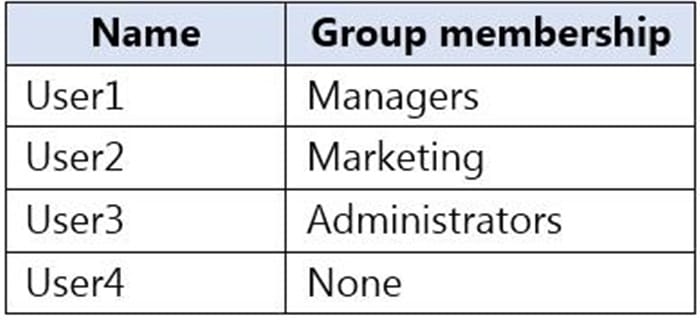
The company has four departments that have the mailboxes shown in the following table.
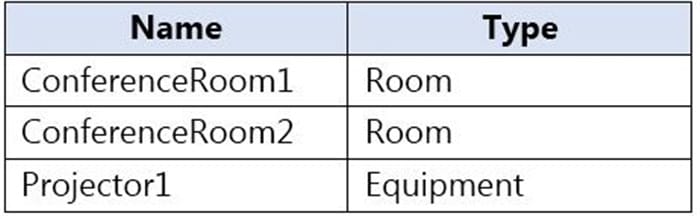
The mailboxes are configured as shown in the following table.
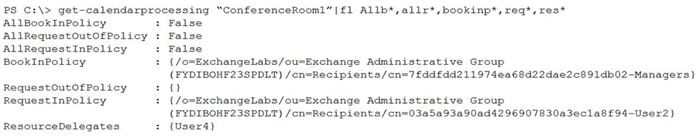
You have two administrators named Admin1 and Admin2 that are assigned the permissions shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
You need to ensure that a user named Lee Gu can view all the Exchange Online configurations of your organization. The solution must use the principle of least privilege.
To complete this task, sign in to the Microsoft 365 admin center.
A. See explanation below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
You need to ensure that a notification email is sent to [email protected] when a user marks an email message as Not Junk in Microsoft Outlook.
A. See explanation below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
You manage a Microsoft Exchange Server 2019 organization that contains several thousand users.
All the users connect to their mailbox by using a mobile device and Exchange ActiveSync.
You need to prevent the users from syncing email messages that are older than 14 days to the mobile devices.
What should you use?
A. an Outlook Web App mailbox policy
B. a mobile device mailbox policy
C. an ActiveSync device access rule
D. a conditional access policy
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Online tenant that uses an email domain named contoso.com.
You need to prevent all users from performing the following tasks:
Sending out-of-office replies to an email domain named fabrikam.com. Sending automatic replies to an email domain named adatum.com.
The solution must ensure that all the users can send out-of-office replies and automatic replies to other email domains on the internet.
Solution: You modify the default remote domain.
Does this meet the goal?
A. Yes
B. No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Online tenant that uses an email domain named contoso.com.
You need to prevent all users from performing the following tasks:
Sending out-of-office replies to an email domain named fabrikam.com. Sending automatic replies to an email domain named adatum.com.
The solution must ensure that all the users can send out-of-office replies and automatic replies to other email domains on the internet.
Solution: You create two sharing policies.
Does this meet the goal?
A. Yes
B. No
You have a Microsoft Exchange Online tenant that has anti-spam policies configured.
You need to identify any anti-spam policy settings that were changed during the last three months and review recommendations for increasing compliance with the Microsoft Standard or Strict configurations for Exchange Online anti-spam
policies.
What should you use?
A. the Insights dashboard in the Exchange admin center
B. Microsoft Defender for Cloud Apps
C. Configuration analyzer in Microsoft 365 Defender
D. Compliance Manager
You need to recommend an Office 365 solution that meets the technical requirements for email from adatum.com.
Which two components should you recommend configuring from the Exchange admin center in Exchange Online? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. a malware filter
B. a connection filter
C. data loss prevention (DLP) policies
D. DKIM signatures
E. a spam filter

