JPR-934 Online Practice Questions and Answers
You are working as the administrator at ABC.com. Part of you job description includes the deployment of applications on the ABC.com network. To this end you operate by testing new application deployment in a test environment prior to deployment on the production network.
The new application that should be tested requires 2 processors and 3 GB of RAM to run successfully. Further requirements of this application also include shared folders and installation of software on client computers. You install the application on a Windows Server Web Edition computer and install the application on 30 test client computers.
During routine monitoring you discover that only a small amount of client computers are able to connect and run the application. You decide to turn off the computers that are able to make a connection and discover that the computers that failed to open the application can now run the application.
How would you ensure that all client computers can connect to the server and run the application?
A. By running a second instance of the application on the server.
B. By increasing the Request Queue Limit on the Default Application Pool.
C. By modifying the test server operating system to Window Server Standard Edition.
D. By increasing the amount of RAM in the server to 4GB.
You are working for an administrator for ABC.com. The ABC.com network consists of a single Active Directory domain named ABC.com. All the servers on the network run Windows Server servers.
You have configured four servers in a network load balancing cluster. You need to enable the cluster in unicast mode although each server only has one network card. After your configuration, the NLB cluster has successfully converged.
You discover that you can optimize the use of the cluster by moving a specific application to each node of the cluster. However for this application to execute, all the nodes of the cluster must be configured by a Network Load Balancing Port
Rule.
When you open Network Load Balancing Manager on one of the NLB nodes, you receive a message saying that Network Load Balancing Manager is unable to see the other nodes in the cluster.
How can you add a port rule to the cluster nodes?
A. By opening Network Load Balancing Manager on a different host.
B. By creating an additional virtual IP address on the cluster.
C. By modifying the Network Connection Properties on every host.
D. By removing each host from the cluster before creating the port rule.
The ABC.com network consists of a single Active Directory domain named ABC.com.
You deploy an enterprise certification authority (CA) on a Windows Server computer named ABC-CA1. The primary purpose of the CA is issue company users with digital certificates to enable them to authenticate with the new company Intranet website. You create a new certificate template named Web Authentication. You enable the Web Authentication certificate template on ABC-CA1 and configure the default domain group policy so that users who log on to the domain receive a Web
Authentication certificate.
The following morning users complain that they do not have certificates which can be used to authenticate to the Intranet Web site.
How can you ensure the users are issued with a certificate?
A. By configuring ABC-CA1 to be an Enterprise Subordinate CA of a public CA such as Verisign.
B. By modifying the permissions of the Web Authentication certificate template to give the Domain Users group the Allow – Autoenroll permission.
C. By adding your Domain Admin user account to the Cert Managers group in Active Directory.
D. By configuring the Default Domain Controllers GPO to assign the certificates to users when they log on.
The ABC.com network consists of a single Active Directory domain named ABC.com. All servers on the ABC.com network run Windows Server.
The ABC.com domain contains two Active Directory sites named ABC-Site1 and ABC-Site2. ABC-Site1 contains a domain controller named ABC-DC1. ABC-Site2 contains a domain controller named ABC-DC2. Each domain controller is
configured as a DNS server and hosts the ABC.com Active Directory Integrated Zone.
Users in ABC-Site2 report that they are unable to log on to the domain.
On a client computer in ABC-Site2, you run the “nslookup ABC-DC2” command. The command returns the IP address of ABC-DC2.
You open Active Directory Users and Computers on the client computer but you are unable to connect to ABC-DC2.
How can you resolve this problem?
A. Run the ipconfig /registerdns command on ABC-DC2.
B. Configure a secondary zone on ABC-DC2 for the ABC.com domain and force replication from ABC-DC1.
C. Use Active Directory Sites and Services to force Active Directory replication.
D. Use the Services console to restart the Net Logon service on ABC-DC2.
The ABC.com network consists of a single Active Directory domain named ABC.com. All the servers on the network run Windows Server servers.
The network contains a file server named ABC-SR24. ABC-SR24 hosts shared folders for users in the Sales department.
All shared folders are backed up using a Normal backup on a weekly basis over the weekend. An incremental backup of the shared folders is taken every night.
A Copy backup of the shared folders is taken every Thursday night after the incremental backup. On Friday morning, the Sales manager reports that he has accidentally deleted an important file. He asks you to restore the file as quickly as
possible. He doesn't know when the file was last modified.
From which backup tape or tapes should you restore the file?
A. The last normal backup and the last incremental backup.
B. The last normal backup and the incremental backups from Monday, Tuesday, Wednesday and Thursday.
C. The last incremental backup.
D. The last normal backup.
E. The last Copy backup.
You are the server administrator for SRV05 which is a Windows Server Standard Edition file server in your domain. Your backup strategy utilizes one full backup and then daily differential backups. SRV05 has eight 72GB SCSI3 10,000RPM
drives in an external drive array for data and are set up using hardware RAID 5. SRV05 also has two additional 72GB SCSI3 10,000RPM drives internal to the system and they are configured in a RAID 1 arrangement. This volume holds the
system and boot partitions for the server's operating systems and a small amount of local application data.
The full back up is performed each Saturday at 9:00PM EST. The full back up takes 2 hours. The daily differential backups are performed each day at 9:00PM, Monday through Friday. There is no full backup nor differential backup performed
on Sunday. The amount of time needed for the differential backups varies but it is never less than 20 minutes and the maximum time never exceeds 75 minutes.
DNS07 has a hard disk failure in the external array at approximately 6:00PM on a Saturday. At 7:20PM a second drive in the external array also fails. What needs to be done to bring the server back to working order so that users can access
the data on the server?
Select the best answer.
A. The failed drives need to be replaced and the data needs to be restored from the full backup.
B. The failed drives need to be replaced and the data needs to be restored from the full backup and all of the differential backups.
C. The failed drives need to be replaced. Nothing additional needs to be done because the RAID configuration allows the system to continue to run.
D. The failed drives need to be replaced and the data needs to be restored from the full backup and the last differential backup.
You work as a Network Administrator for ABC.com. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server. An application named Accounts is installed on
the network. The Accounts application uses a shared folder named AccFolder to keep all its data. The AccFolder folder is placed on a file server named uCFileServer. All users in the network use the application to update the accounts
information of various clients of the company. The application opens various data files to work upon.
You are required to accomplish the following tasks:
All files in the AccFolder folder should be backed up automatically twice daily.
The backup process should take a backup of all the open files in the folder.
In order to accomplish the tasks, you take the following steps:
Configure the Backup and Restore Wizard to take a backup of AccFolder.
Unselect the Disable volume shadow copy check box in the Backup and Restore Wizard.
Set the schedule of the Backup and Restore Wizard to take a backup every 12 hours through the Advanced Schedule Options.
What will happen after taking the required steps?
A. The backup process will take a backup of all the open files in the folder.
B. Both tasks will be accomplished.
C. All the files in the AccFolder folder will be backed up automatically twice daily.
D. None of the tasks will be accomplished.
You administer your company's network. The network consists of a single Active Directory domain. All servers run Windows Server. The network contains a two-node server cluster. The company's security expert informs you that the
password on the domain user account that is used for the Cluster service has been compromised and must be changed immediately. Your actions should cause minimal or no disruption of the services provided by the cluster because the
cluster is running a mission-critical application.
Which of the following should you do?
A. Use Active Directory Users and Computers to reset the password.
B. Use the Services console to change the password on any one of the cluster nodes.
C. Use the Cluster command with the appropriate options.
D. Use the dsmod user command with the appropriate options.
E. Use the dsmod computer command with the appropriate options.
You administer your company's Web site, which contains executable programs. You want to provide the highest level of trust to Internet users who download your programs, and you want to ensure that users' browsers will allow them to
download the programs. Your company's network includes an enterprise root Certification Authority (CA) and an issuing enterprise subordinate CA.
Which of the following actions should you take?
A. Request a Code Signing certificate from your company's enterprise subordinate CA.
B. Request a Code Signing certificate from a commercial CA.
C. Request a User Signature Only certificate from your company's enterprise subordinate CA.
D. Request a User Signature Only certificate from a commercial CA.
You are the backup administrator for your company. You are responsible for ensuring that all data on ten files servers are protected against data loss. Normal business hours from 8 A.M. to 5 P.M., Monday through Friday, are observed.
Network access is prohibited outside normal business hours.
A member server named File1 contains shared folder accessed by users in the sales department. The disk structure of File1 is shown in the following exhibit:
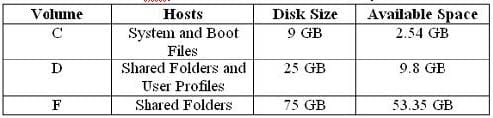
You have scheduled a daily backup of File1 as shown in the exhibit. (Click the Exhibit(s) button.) Users in the Sales department frequently leave documents open on their desktops when they leave work. These users occasionally request that
you restore a previous version of a file from backup. However, some of these files are not included in recent backup sets. You must modify the backup procedures for File1 so that all files, including open documents, will be included in the daily
backup. You also want to provide users with the ability to restore their files.
What should you do? (Choose all that apply. Each correct answer presents part of the solution.)
A. Move all shared user data folders from drive D to drive F.
B. Move all shared folders user data from drive F to drive D.
C. Enable Shadow Copies of Shared Folders on drive F.
D. Enable Volume shadow copy for the scheduled backup job.
E. Select the Disable volume shadow copy option for the scheduled backup job.
F. Install the Previous Versions Client software on all Sales department computers.
G. Create a new daily backup job by using the same settings, but clear the Disable volume shadow copy option.
The only protocol used by your network is TCP/IP, despite the fact that workstations in the organization do not have access to the Internet. A user has been accessing files on server on your network and now wants to connect to a Web server
that is used as part of the company's intranet. The user enters the URL of the Web site into Internet Explorer.
Which of the following servers will be used to provide information needed to connect to the Web server?
A. DHCP server
B. DNS server
C. WINS server
D. File server
You have a number of users who need to be able to roam through the building with their laptop computers and still stay connected to the network. Because of the nature of their work, it is important that they have relatively fast access for transferring a lot of very large data files over the network. You need to implement a wireless network that can connect devices up to 54 Mbps and a minimum of 24 Mbps. Which IEEE standard should you choose?
A. 802.15
B. 802.11a
C. 802.11b
D. 802.1x
You are a network administrator for your Windows Server domain and you are updating the network configuration for your company. You have used part of the 191.99.74.0/16 IP address range that your company owns and segmented the
networks in this new location in such a way to allow for 60 hosts per subnet currently and also allow for an anticipated growth of 15% for the client systems.
Your design also calls for adding a routing configuration that will allow you to forward IP multicast traffic and the use of the Internet Group Management Protocol (IGMP). You have decided to use the Routing and Remote Access Service on
your Windows Server system to handle this requirement in your environment. You also need to define the standards for your network nodes with regard to multicasting on your network.
What is a specific characteristic that is required of a host or network node that is multicast-capable?
Select the best answer.
A. The network node must be able to use a multicast routing protocol to propagate multicast group listening information to other multicast-capable nodes.
B. The network node must be able to listen for all multicast traffic on all attached networks. Upon receiving multicast traffic the node would have to forward the multicast packet to attached networks where other nodes are listening or where downstream routers have nodes that are listening.
C. The network node must be able to listen for IGMP membership report messages and update the TCP/IP multicast forwarding table.
D. The network node must be able to register the multicast addresses being listened to by the node with local routers so that multicast packets can be forwarded to the network of the node.
You work as the network administrator at ABC.com. The ABC.com network has a domain named ABC.com. The servers at the ABC.com network run Windows Server. ABC.com has a subsidiary named Test Labs, Inc. that has a domain
named testlabs.com.
The ABC.com network has a DNS server named ABC-SR05. ABC-SR05 acts as a secondary zone for testlabs.com
What actions must you take to track when the DNS server at Test Labs, Inc. sends notifications of modifications in the zone of testlabs.com to ABC-SR05?
A. You must run the gpresult command in verbose mode.
B. You must select debug logging and set the log to store Notification events on ABC- SR05.
C. You must run the secedit command in analysis mode.
D. You must configure a two-way initiated demand-dial connection.
You work as the network administrator at ABC.com. The ABC.com network consists of a domain named ABC.com.
ABC.com has several subsidiary companies whose Web sites and DNS zones are hosted on servers at ABC.com.
What actions must you take to allow the DNS server at ABC.com to generate a report of the listed zones on a weekly basis?
A. You need to utilize the ipconfig/registerdns.
B. You need to NetMon utility on the DNS server.
C. You need to utilize the dnscmd utility on the DNS server.
D. You need to utilize the ADSIEdit utility on the DNS server.
