JN0-682 Online Practice Questions and Answers
Which two statements describe a VXLAN network identifier (VNI)? (Choose Two)
A. A VNI identifies the inner MAC frame.
B. A VNI identifies a VXLAN segment ID.
C. A VNI allows only 512 VLANs.
D. A VNI validates the remote VTEP.
You have deployed a VXLAN as shown in the exhibit Leaf1, leaf3, spine1, and spine2 have been configured as VTEPs. Host1 cannot communicate with host2.
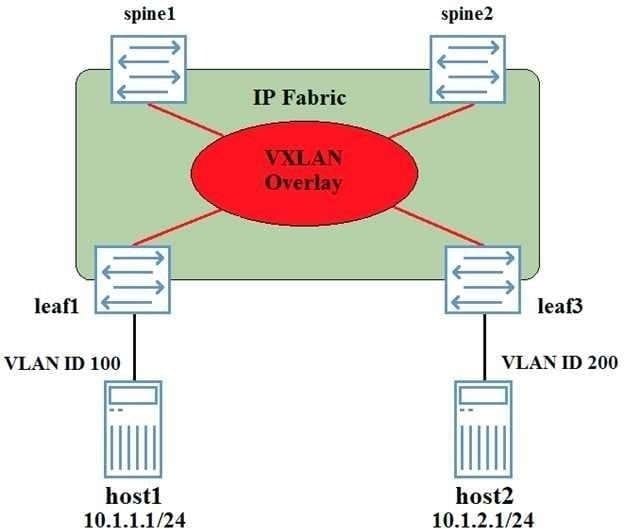
Referring to the exhibit, how would you solve this problem?
A. The VLAN ID on the connected to host2 must be changed to VLAN 100
B. A DCI connected must be created between the VLANs
C. Host1 and host2 must be placed in the same VRF
D. A layer 3 VXLAN gateway must be configured on at least on at least one of the devices
In the exhibit, VM1 is part of the same VXLAN segment as VM3.
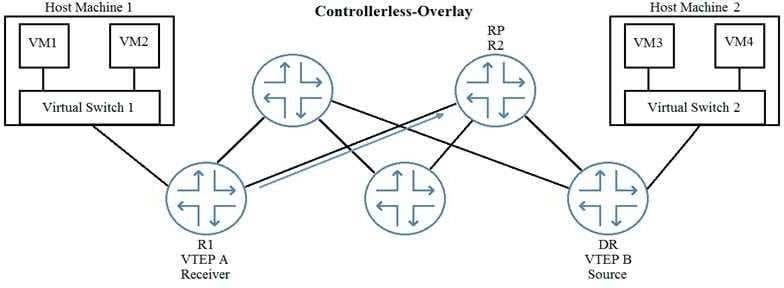
Which type of message will R1 initially send to R2 so that VM1 receives BUM traffic from VM3?
A. PIM Join
B. PIM Register message
C. IGMP Join (S, G)
D. IGMP Join (*.G)
You are troubleshooting an L3VPN that is part of an EVPN/MPLS DCI. You notice that the EVPN overlay BGP session toward 10.29.50.4 is unable to establish.
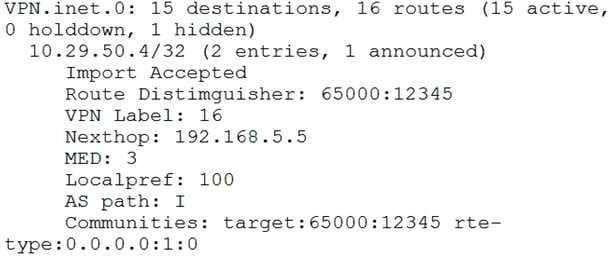
Why is the BGP session failing to establish?
A. The route-distinguisher value on the local PE is incorrect
B. There is no route for 192.168.5.5 an VPN net 0.
C. There is no route for 192.168.5.5. in inet 3.
D. The vrf-table abel value is not configured in the remote PE.
You host a multitenant data center that runs VMware. You must perform deep packet inspection on all inter-tenant traffic that is flowing between the VMs within the same hypervisor. Your solution must provide the security services without needing to leave the physical device. In this scenario, what should you do to solve this problem?
A. Use separate vswitches to isolate each-tenant's network and use and use a vSRX device to evaluate inter-tenant traffic.
B. Use VLANs to isolate each tenant's networks and use an SRX Series device to evaluate inter-tenant traffic.
C. Use a VLANs to isolate each tenant's network and use IP tables to evaluates inter- tenant traffic.
D. Use a vMX device to isolate each tenant's network and use firewall filters to evaluate inter-tenant traffic.
You need to add perimeter security to the network shown in the exhibit. All traffic must be inspected for attacks. The edge routers are using all available ports. Your solution must maintain both port and device resiliency.
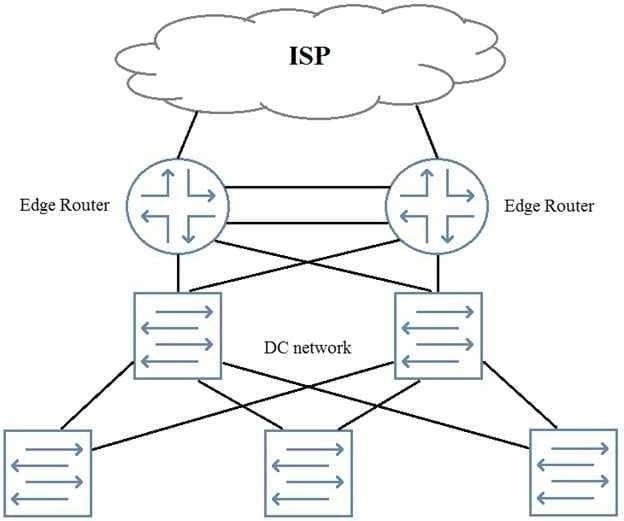
In this scenario, which design would satisfy these requirements?
A. one-arm SRX Series chassis cluster
B. one-arm SRX Series device using LAG
C. inline SRX Series chassis cluster
D. inline SRX Series device using LAG
Which two statements are correct about VXLANs? (Choose two.)
A. VXLANs have smaller broadcast domains than VLANs.
B. VXLANs have a smaller logical network identifier than VLANs.
C. VXLANs can have a theoretical maximum of 16 million unique networks.
D. VXLANs are an overlay technology.
Referring to the exhibit, you have a data center in which only the spine devices are using EVPN and VXLAN. The leaf nodes are multihomed in active-active mode to the spine nodes through ESI LAG interfaces. In this design, a link failure on the interface connecting the spine nodes would also cause all traffic from the spine to the leaf nodes to drop.
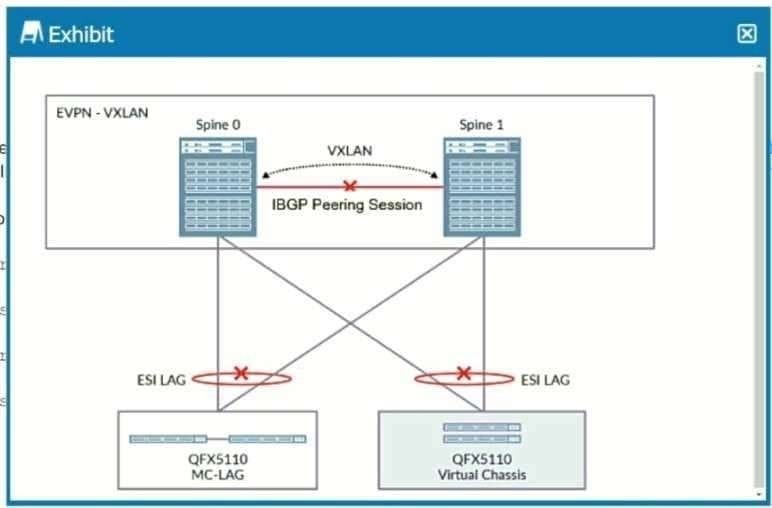
In this scenario, which command configured on which nodes would solve this problem?
A. the disable protocols evpn no-core-isolation command on the spine nodes
B. the set protocols evpn no-core-isolation command on the spine nodes
C. the disable protocols evpn no-core-isolation command on the leaf nodes
D. the set protocols evpn no-core-isolation command on the leaf nodes
