JN0-348 Online Practice Questions and Answers
Which two port security features use the DHCP snooping database for additional port security? (Choose two.)
A. dynamic ARP inspection
B. MACsec
C. IP Source Guard
D. MAC learning
Which two statements are correct regarding the root bridge election process when using STP? (Choose two.)
A. A lower system MAC address is preferred.
B. A higher bridge priority is preferred.
C. A lower bridge priority is preferred.
D. A higher system MAC address is preferred.
When configuring firewall filters, which function does the interface-specific parameter enable on an EX Series switch?
A. The interface-specific parameter is required to configure port-specific counters.
B. The interface-specific parameter is required to configure VLAN-specific counters.
C. The interface-specific parameter is required to configure VLAN-based filters.
D. The interface-specific parameter is required to configure port-based firewall filters.
Which static route next-hop value indicates that the packet will be silently dropped?
A. resolve
B. discard
C. reject
D. next-table
Which area is reserved for the OSPF backbone?
A. Area 0.0.0.0
B. Area 1.1.1.1
C. Area 2.2.2.2
D. Area 3.3.3.3
Your network connections to the Internet through two different ISPs using EBGP. You must ensure that ISP1 is the primary path used for all traffic entering your network while using ISP2 as a backup path.
In this scenario, which statement is correct?
A. You should use a lower MED value on routes sent to ISP1.
B. You should assign a higher local preference on routes that you are sending to ISP1.
C. You should change the next hop for all routers sent to ISP2.
D. You should prepend your local AS number three times on routes that you are sending to ISP2.
Which device is used to separate collision domains?
A. switch
B. router
C. hub
D. firewall
You are adding a new EX4300 member switch to your existing EX4300 Virtual Chassis. However, the new member is not running the same Junos version as the other members.
By default, what is the expected behavior in this scenario?
A. the Virtual Chassis will transition into a split brain situation between the existing master Routing Engine and the switch running the different version.
B. The new switch will automatically pull the correct version from the master Routing Engine and perform the necessary upgrade.
C. The new switch will be assigned a member ID and then placed in an inactive state.
D. The new switch is not recognized by the Virtual Chassis.
Click the Exhibit button.
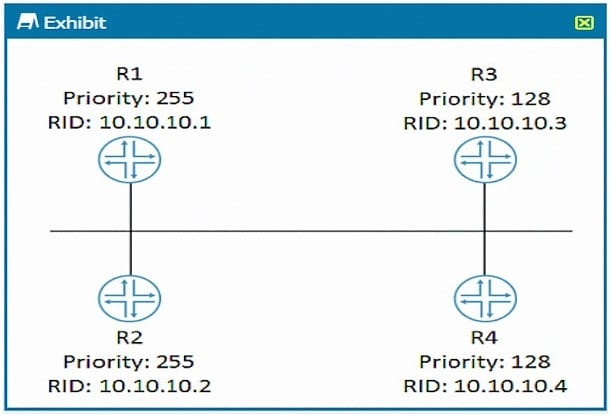
Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?
A. R3
B. R4
C. R1
D. R2
Click the Exhibit button.

Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)
A. 172.12.31.0/24
B. 172.12.33.0/24
C. 172.12.30.0/24
D. 172.12.32.0/24
Click the Exhibit button.
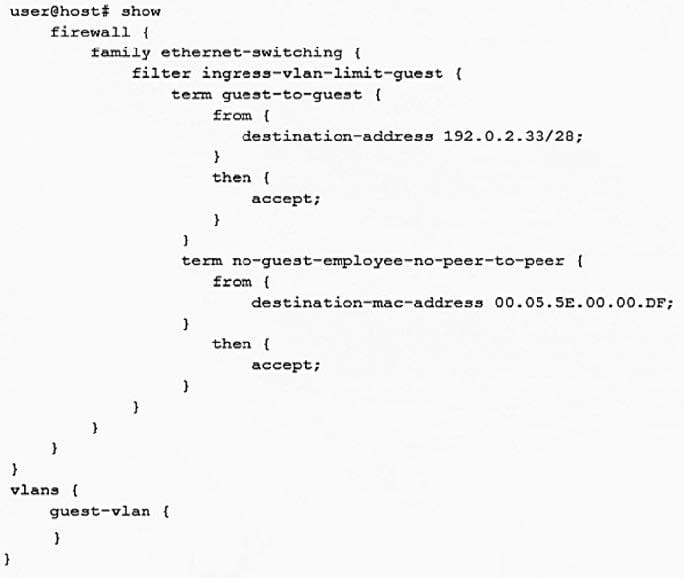
A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic.
In this scenario, what must you do to implement the security policy?
A. Implement 802.1X on the guest VLAN
B. Attach the filter to the VLAN
C. Deploy storm control to block unknown unicast traffic
D. Use persistent MAC learning
Which OSPF packet type is sent when an OSPF router detects its database is stale?
A. database description
B. link-state acknowledgment
C. link-state request
D. hello
Which statement is true about IP-IP tunnels?
A. The time-to-live value of the original packet is decremented.
B. IP-IP tunnels are protocol agnostic.
C. The packet is encapsulated unchanged before entering the tunnel.
D. The packet header is replaced before entering the tunnel.
How many bytes of overhead forms an IP-IP tunnel add to a packet?
A. 20 bytes
B. 24 bytes
C. 28 bytes
D. 14 bytes
Click the Exhibit button.
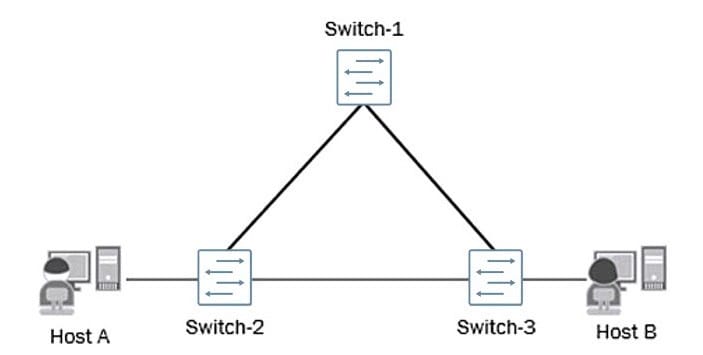
A number of reports from end users indicate that internal and external communications are intermittent and not reliable. You verified the status of the switch ports and have determined that they are up and operational. You also noticed a very high level of link bandwidth utilization on those same ports. The current topology of the affected environment is shown in the exhibit.
What would be the cause of the reported issues?
A. A misconfigured interior gateway protocol (IGP).
B. A lack of a loop-prevention mechanism or protocol.
C. A lack of port-based ACLs filtering the traffic flows.
D. A malformed route-based ACL improperly filtering traffic flows.
