JN0-230 Online Practice Questions and Answers
You want to automatically generate the encryption and authentication keys during IPsec VPN
establishment.
What would be used to accomplish this task?
A. IPsec
B. Diffie_Hellman
C. Main mode
D. Aggregate mode
On an SRX device, you want to regulate traffic base on network segments. In this scenario, what do you configure to accomplish this task?
A. Screens
B. Zones
C. ALGs
D. NAT
Which two match conditions would be used in both static NAT and destination NAT rule sets? (Choose two.)
A. Destination zone
B. Destination interface
C. Source interface
D. Source zone
Which two statements are true about the null zone? (Choose two.)
A. All interface belong to the bull zone by default.
B. All traffic to the null zone is dropped.
C. All traffic to the null zone is allowed
D. The null zone is a user-defined zone
You are concerned that unauthorized traffic is using non-standardized ports on your network. In this scenario, which type of security feature should you implement?
A. Application firewall
B. Sky ATP
C. Firewall filters
D. Zone-based policies
Which two statements are true about security policy actions? (Choose two.)
A. The reject action drops the traffic and sends a message to the source device.
B. The deny action silently drop the traffic.
C. The deny action drops the traffic and sends a message to the source device.
D. The reject action silently drops the traffic.
Which two elements are needed on an SRX Series device to set up a remote syslog server? (Choose two.)
A. Data type
B. Data throughput
C. IP address
D. Data size
Which security object defines a source or destination IP address that is used for an employee Workstation?
A. Zone
B. Screen
C. Address book entry
D. scheduler
Which two statements are true regarding zone-based security policies? (Choose two.)
A. Zone-based policies must reference a source address in the match criteria.
B. Zone-based policies must reference a URL category in the match criteria.
C. Zone-based policies must reference a destination address in the match criteria
D. Zone-based policies must reference a dynamic application in the match criteria.
Exhibit.
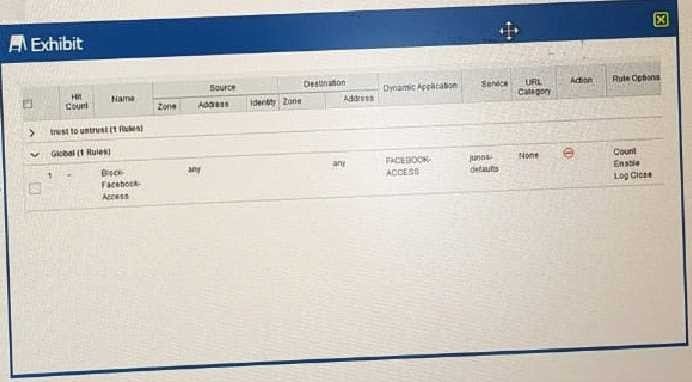
Which two statements are true? (Choose two.)
A. Logs for this security policy are generated.
B. Logs for this security policy are not generated.
C. Traffic static for this security policy are not generated.
D. Traffic statistics for this security policy are generated.
You have configured a Web filtering UTM policy?
Which action must be performed before the Web filtering UTM policy takes effect?
A. The UTM policy must be linked to an egress interface
B. The UTM policy be configured as a routing next hop.
C. The UTM policy must be linked to an ingress interface.
D. The UTM policy must be linked to a security policy
Which source NAT rule set would be used when a packet matches the conditions in multiple rule sets?.
A. The most specific rule set will be used
B. The least specific rule set will be used
C. The first rule set matched will be used
D. The last rule set matched will be used
What does IPsec use to negotiate encryption algorithms?
A. TLS
B. AH
C. ESP
D. IKE
What is a type of security feed that Sky ATP provides to a vSRX series device by default?
A. CandC feeds
B. Malware feeds
C. RSS feeds
D. ACL feeds
Which statements describes stateless firewalls on SRX series devices?
A. Each packet is analyzed by firewall filters
B. Each packet is analyzed based on application layer security
C. Each packet is analyzed based on source zone
D. Each packet is analyzed as part of a session.
