CISSP Online Practice Questions and Answers
Which of the following is used to detect steganography?
A. Audio analysis
B. Statistical analysis
C. Reverse engineering
D. Cryptanalysis
Which of the following can be used to calculate the loss event probability?
A. Total number of possible outcomes divided by frequency of outcomes
B. Number of outcomes divided by total number of possible outcomes
C. Number of outcomes multiplied by total number of possible outcomes
D. Total number of possible outcomes multiplied by frequency of outcomes
Which of the following MUST system and database administrators be aware of and apply when configuring systems used for storing personal employee data?
A. Secondary use of the data by business users
B. The organization's security policies and standards
C. The business purpose for which the data is to be used
D. The overall protection of corporate resources and data
The configuration management and control task of the certification and accreditation process is incorporated in which phase of the System Development Life Cycle (SDLC)?
A. System acquisition and development
B. System operations and maintenance
C. System initiation
D. System implementation
Which of the following provides the BEST method to verify that security baseline configurations are maintained?
A. Perform regular system security testing
B. Design security early in the development cycle
C. Analyze logs to determine user activities
D. Perform quarterly risk assessments
When dealing with shared, privileged accounts, especially those for emergencies, what is the BEST way to assure non-repudiation of logs?
A. Implement a password vaulting solution
B. Lock passwords in tamperproof envelopes in a safe
C. Regularly change the passwords
D. Implement a strict access control policy
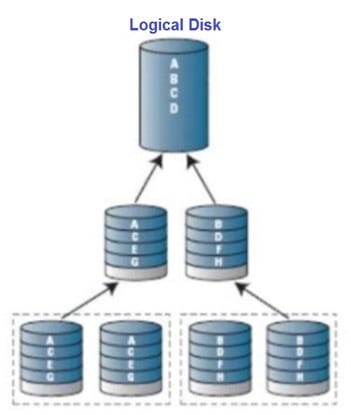
Which Redundant Array of Independent Disks (RAID) Level does the following diagram represent?
A. RAID 0
B. RAID 1
C. RAID 5
D. RAID 10
Which of the following is an advantage of Secure Shell (SSH)?
A. It operates at the network layer
B. It encrypts transmitted User ID and passwords
C. It uses challenge-response to authenticate each party
D. It uses the International Data Encryption Algorithm (IDEA) for data privacy
An Intrusion Detection System (IDS) is based on the general hypothesis that a security violation is associated with a pattern of system usage, which can be
A. differentiated from a normal usage pattern
B. used to detect known violations
C. used to detect a masquerader
D. differentiated to detect all security violations
What is the FIRST step for an organization to take before allowing personnel to access social media from a corporate device or user account?
A. Publish a social media guidelines document.
B. Publish an acceptable usage policy.
C. Document a procedure for accessing social media sites.
D. Deliver security awareness training.
In a multi-tenant cloud environment, what approach will secure logical access to assets?
A. Hybrid cloud
B. Transparency/Auditability of administrative access
C. Controlled configuration management (CM)
D. Virtual private cloud (VPC)
When resolving ethical conflicts, the information security professional MUST consider many factors. In what order should these considerations be prioritized?
A. Public safety, duties to individuals, duties to the profession, and duties to principals
B. Public safety, duties to principals, duties to individuals, and duties to the profession
C. Public safety, duties to the profession, duties to principals, and duties to individuals
D. Public safety, duties to principals, duties to the profession, and duties to individuals
Which of the following is considered the FIRST step when designing an internal security control assessment?
A. Create a plan based on recent vulnerability scans of the systems in question.
B. Create a plan based on comprehensive knowledge of known breaches.
C. Create a plan based on a recognized framework of known controls.
D. Create a plan based on reconnaissance of the organization's infrastructure.
Which of the following is the PRIMARY purpose of installing a mantrap within a facility?
A. Control traffic
B. Prevent rapid movement
C. Prevent plggybacking
D. Control air flow
The quality assurance (QA) department is short-staffed and is unable to test all modules before the anticipated release date of an application. What security control is MOST likely to be violated?
A. Separation of environments
B. Program management
C. Mobile code controls
D. Change management
