CAS-004 Online Practice Questions and Answers
SIMULATION
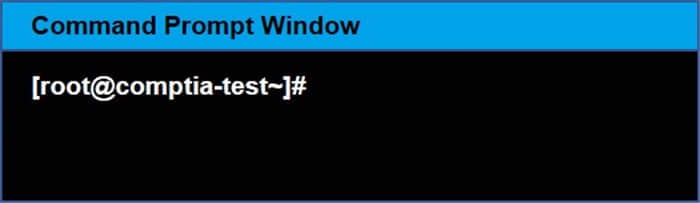
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
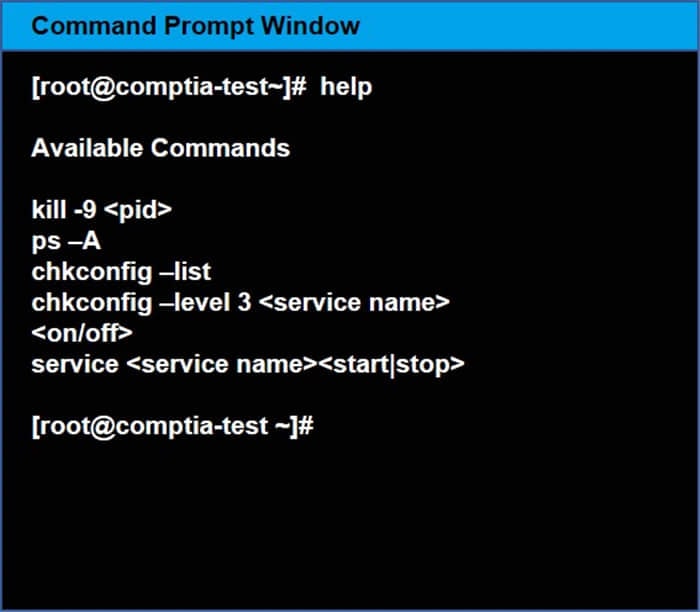
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A. Check the answer in explanation.
B. PlaceHoder
C. PlaceHoder
D. PlaceHoder
During a remodel, a company's computer equipment was moved to a secure storage room with cameras positioned on both sides of the door. The door is locked using a card reader issued by the security team, and only the security team and department managers have access to the room. The company wants to be able to identify any unauthorized individuals who enter the storage room by following an authorized employee.
Which of the following processes would BEST satisfy this requirement?
A. Monitor camera footage corresponding to a valid access request.
B. Require both security and management to open the door.
C. Require department managers to review denied-access requests.
D. Issue new entry badges on a weekly basis.
A small business requires a low-cost approach to theft detection for the audio recordings it produces and sells. Which of the following techniques will MOST likely meet the business's needs?
A. Performing deep-packet inspection of all digital audio files
B. Adding identifying filesystem metadata to the digital audio files
C. Implementing steganography
D. Purchasing and installing a DRM suite
An organization decided to begin issuing corporate mobile device users microSD HSMs that must be installed in the mobile devices in order to access corporate resources remotely
Which of the following features of these devices MOST likely led to this decision? (Select TWO.)
A. Software-backed keystore
B. Embedded cryptoprocessor
C. Hardware-backed public key storage
D. Support for stream ciphers
E. Decentralized key management
F. TPM 2.0 attestation services
A network engineer is concerned about hosting web, SFTP. and email services in a single DMZ that is hosted in the same security zone This could potentially allow lateral movement within the environment. Which of the following should the engineer implement to mitigate the risk?
A. Put all the services on a single host to reduce the number of servers.
B. Create separate security zones for each service and use ACLs for segmentation.
C. Keep the web server in the DMZ and move the other server services to the internal network.
D. Deploy a switch and create VLANs for each service.
A cybersecunty analyst receives a ticket that indicates a potential incident is occurring. There has been a large increase in log files generated by a website containing a `Contact Us' form. The analyst must determine if the increase in website traffic is due to a recent marketing campaign or if this is a potential incident.
Which of the following would BEST assist the analyst?
A. Ensuring proper input validation is configured on the `Contact Us' form
B. Deploying a WAF in front of the public website
C. Checking for new rules from the inbound network IPS vendor
D. Running the website log files through a log reduction and analysis tool
A systems administrator was given the following IOC to detect the presence of a malicious piece of software communicating with its command-and-control server:
1.
POST /malicious.php
2.
User-Agent: Malicious Tool V 1.0
3.
Host: www.malicious.com
The IOC documentation suggests the URL is the only part that could change. Which of the following regular expressions would allow the systems administrator to determine if any of the company hosts are compromised, while reducing false positives?
A. User-Agent: Malicious Tool.*
B. www\.malicious\.com\/malicious.php
C. Post /malicious\.php
D. Host: [a-z]*\.malicious\.com
E. malicious.*
A recent security audit identified multiple endpoints have the following vulnerabilities:
1.
Various unsecured open ports
2.
Active accounts for terminated personnel
3.
Endpoint protection software with legacy versions
4.
Overly permissive access rules
Which of the following would BEST mitigate these risks? (Choose three).
A. Local drive encryption
B. Secure boot
C. Address space layout randomization
D. Unneeded services disabled
E. Patching
F. Logging
G. Removal of unused accounts
H. Enabling BIOS password
In a shared responsibility model for PaaS, which of the following is a customer's responsibility?
A. Network security
B. Physical security
C. OS security
D. Host infrastructure
A software assurance analyst reviews an SSH daemon's source code and sees the following:
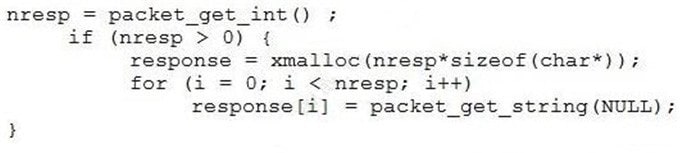
Based on this code snippet, which of the following attacks is MOST likely to succeed?
A. Race condition
B. Cross-site scripting
C. Integer overflow
D. Driver shimming
An organization's senior security architect would like to develop cyberdefensive strategies based on standardized adversary techniques, tactics, and procedures commonly observed. Which of the following would BEST support this objective?
A. OSINT analysis
B. The Diamond Model of Intrusion Analysis
C. MITRE ATTandCK
D. Deepfake generation
E. Closed-source intelligence reporting
The Chief Information Security Officer (CISO) has outlined a five-year plan for the company that includes the following:
1.
Implement an application security program.
2.
Reduce the click rate on phishing simulations from 73% to 8%.
3.
Deploy EDR to all workstations and servers.
4.
Ensure all systems are sending logs to the SIEM.
5.
Reduce the percentage of systems with vulnerabilities from 89% to 5%.
Which of the following would BEST aid the CISO in determining whether these goals are obtainable?
A. An asset inventory
B. A third-party audit
C. A risk assessment
D. An organizational CMMI
When implementing serverless computing an organization must still account for:
A. the underlying computing network infrastructure
B. hardware compatibility
C. the security of its data
D. patching the service
A company recently migrated its critical web application to a cloud provider's environment. As part of the company's risk management program, the company intends to conduct an external penetration test. According to the scope of work and the rules of engagement, the penetration tester will validate the web application's security and check for opportunities to expose sensitive company information in the newly migrated cloud environment. Which of the following should be the first consideration prior to engaging in the test?
A. Prepare a redundant server to ensure the critical web application's availability during the test.
B. Obtain agreement between the company and the cloud provider to conduct penetration testing.
C. Ensure the latest patches and signatures are deployed on the web server.
D. Create an NDA between the external penetration tester and the company.
A software developer has been tasked with creating a unique threat detection mechanism that is based on machine learning. The information system for which the tool is being developed is on a rapid CI/CD pipeline, and the tool developer is considered a supplier to the process. Which of the following presents the most risk to the development life cycle and to the ability to deliver the security tool on time?
A. Deep learning language barriers
B. Big Data processing required for maturity
C. Secure, multiparty computation requirements
D. Computing capabilities available to the developer
