EN0-001 Online Practice Questions and Answers
When setting the initial location of the stack pointer and the base address of the heap, the ARM EABI requires that the:
A. Base address of the heap must be the same as the initial stack pointer.
B. Stack pointer must be 8-byte aligned.
C. Heap must be in external RAM.
D. Initial stack pointer must be the lowest addressable memory location.
Which of the following processors includes a Generic Interrupt Controller as a standard component?
A. Cortex-A8
B. Cortex-M3
C. Cortex-R4F
D. Cortex-A9 MPCore
The following function is declared: float func(float fl, float f2);
The file file1 .c contains a call to func, and is compiled with hard floating point linkage. The file file2.c contains the definition of func, and is compiled with AACPS soft floating point linkage.
Assume that the two files are successfully linked using the ARM linker and an executable is generated. The generated executable:
A. Exhibits correct behavior, but suffers a performance penalty because the linker has to generate extra code.
B. Exhibits correct behavior, and suffers no performance penalty.
C. Will not execute.
D. Exhibits incorrect behavior.
In an ARMv7-A processor with Security Extensions, which of the following mechanisms best describes the way Secure memory is protected from access by software running in a Non-secure privileged mode?
A. The memory system has visibility of the security status of all accesses, and will reject all Non- secure accesses to Secure memory
B. Secure memory contents are encrypted, and cannot be decrypted by Non-secure software
C. The level 2 cache controller blocks all accesses to Secure memory when the SCR.NS bit of the processor is set
D. The MMU generates an abort on accesses to Secure memory performed by Non-secure software
Processors which implement the ARMv7-A architecture can be configured to allow unaligned memory access. Unaligned accesses have a number of advantages, disadvantages, and limitations.
Which TWO of the following statements are true? (Choose two)
A. Unaligned accesses may take more cycles to execute than aligned accesses
B. Unaligned loads and stores are necessary for accessing fields in packed structures
C. A program compiled using unaligned accesses can be safely executed on all ARMv7-A devices
D. If the relevant control register setting is enabled all loads and stores can function from unaligned addresses
E. Unaligned accesses can only be made to Normal memory
The Cortex-A9 MPCore processor contains a hardware block whose function is to maintain data cache coherency between cores. What is the name of this block?
A. Shareable Memory
B. Snoop Control Unit
C. Private Memory Region
D. Level 2 Cache Controller
The following pair of functions implement a simple mutex spinlock which might be used to protect a critical code section in a multi-threaded application. The address of the lock variable is in r0.
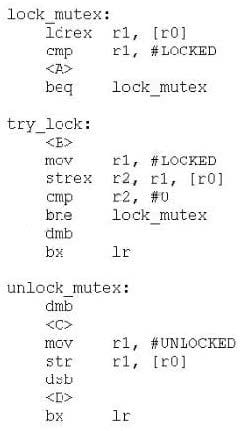
In order to minimize power while waiting for the lock to be available. SEV and WFE instructions can be used to place the processor in a low power state while waiting for the lock to become available. At which points should these instructions be placed?
A. WFENE at , SEV at
B. WFEEQ at SEV at
C. WFE at SEV at
D. SEV at
When using an Operating System, which instruction is used by user code to request a service from the kernel?
A. BLX
B. RFEFD
C. SRSFD
D. SVC
An Advanced SIMD intrinsic has the prototype:
uint8xl6x2_t vld2q_u8 (uint8_t const * ptr);
How many bytes does this intrinsic load from memory?
A. 2
B. 16
C. 32
D. 256
What type of instruction is used for cache maintenance operations?
A. Dedicated ARM instructions
B. Dedicated Thumb instructions
C. CP14 instructions
D. CP15 instructions
As part of the ABI specification, the AAPCS defines which of the following?
A. How many levels of nested function calls are permitted on ARM systems
B. How to measure the maximum amount of stack required by an application
C. On which mode's stack you need to save the return address in a non-leaf function
D. Which registers need to be preserved by a function
Assume a Big-Endian (BE) memory system with the following memory contents. Byte Address Contents 0x100 0x11 0x101 0x22 0x102 0x33 0x103 0x44 If R5 = 0x100, what are the contents of R4 after performing the following operation? LDR R4, [R5]
A. 0x11223344
B. 0x44332211
C. 0x22114433
D. 0x33441122
Assuming a 4-core Cortex-A9 SMP system which does not use the Accelerator Coherency Port (ACP). and operates the L1 caches in writeback mode, in which of the following situations is a cache clean operation required?
A. An external DMA engine modifies data in a region of data memory which is already cached by the processor
B. An external agent needs to read data which has been modified by the processor in a cacheable memory region
C. Debugger reads data from a shared, cacheable memory location
D. One core modifies data in a shared cacheable memory region
Which of the following is TRUE for dynamically linked executables?
A. They can contain unresolved relocations
B. They contain the code and data for all libraries they use
C. They are larger than an equivalent statically linked application
D. They are designed to be run standalone with no other supporting software
Which of the following pairs of statements about the difference between a Memory Management Unit (MMU) and a Memory Protection Unit (MPU) is correct?
A. The MMU uses translation tables. The MPU does not use translation tables.
B. The MMU uses only physical addresses. The MPU translates virtual addresses to physical addresses.
C. The MMU defines cacheability attributes for memory. The MPU does not define cacheability attributes for memory.
D. The MMU defines access permissions for memory. The MPU does not define access permissions for regions of memory.
