E20-361 Online Practice Questions and Answers
Which Celerra component exports file systems for NFS and CIFS access?
A. Control Station
B. DAE2
C. Data Mover
D. Storage processor
Which information can be displayed with the nbtstat command?
A. NetBEUI over IPX/SPX
B. NetBEUI over TCP/IP
C. NetBIOS over IPX/SPX
D. NetBIOS over TCP/IP
You have just captured a network trace for a customer reporting slow performance on a Data Mover. When you open the trace you see a very large number of TCP retransmissions.
What is the most likely cause for these retransmissions?
A. Duplicate IP addresses
B. Invalid broadcast address
C. Speed and duplex mismatch
D. TCP window size too large
Which protocol is used to access object information from a Windows Active Directory?
A. DHCP
B. LDAP
C. NetBIOS name resolution
D. WIN
Which improvement is made when converting an NS gateway system direct-connect to a fabric- connect?
A. Data Mover availability
B. Logical storage path availability
C. Physical storage path availability
D. Storage processor availability
On a Celerra NS gateway, the system LUNs must be configured on a RAID. 5 group. Which parameters must be supported?
A. Any 6+1 RAID. 5 group
B. Any RAID. 5 group
C. Dedicated 4+1 RAID. 5
D. Dedicated 8+1 RAID. 5 group
In a Celerra environment, where does the Celerra Antivirus Agent run?
A. Control Station
B. Data Mover
C. Data Mover and Control Station
D. Windows Server
A systems administrator requires that Data Movers are highly available over the network. The administrator has multiple switches available with no special configuration.
Which Celerra solution best meets this requirement?
A. FastEtherChannel
B. FSN
C. LACP
D. VLAN tagging
What are the SavVol configuration settings when implementing Replicator V2?
A. If PFS > 20 GB, then SavVol = 20 GB
B. If PFS < 20 GB then SavVol = 20 GB
C. If PFS >= 64 MB, then SavVol >= 64 MB
D. If PFS <= 64 MB, then SavVol >= PFS size
The Celerra backup-to-disk (B2D) feature offers what benefit compared to tape-based backup operations?
A. Quick restores of individual files
B. Scalability to larger numbers of clients
C. Archival backups to comply with regulatory policies
D. Utilizes metadata to the backup server to limit network traffic
Which iSCSI objects require secret passwords for two-way CHAP authentication?
A. Agent and protocol server
B. Client and target
C. Target and initiator
D. Target and source
The SavVol High Water Mark (HWM) is set to 0 when a scheduled checkpoint is created. What action is triggered by SnapSure when SavVol is at 90% capacity and there is available disk space?
A. Data in oldest checkpoint is deleted and the space is recycled.
B. Data in oldest checkpoint is automatically copied to tape.
C. Data in most recent checkpoint is deleted and the space is recycled.
D. SavVol is automatically extended when near-full capacity is reached.
Which NAS backup methodology allows the following transfers?
-Data directly to the storage device through a dedicated IP network -Metadata and flow control to and from the backup server over the public network
A. NDMP
B. NFS over LAN copy
C. MPFS
D. CIFS over LAN copy
Refer to the exhibit:
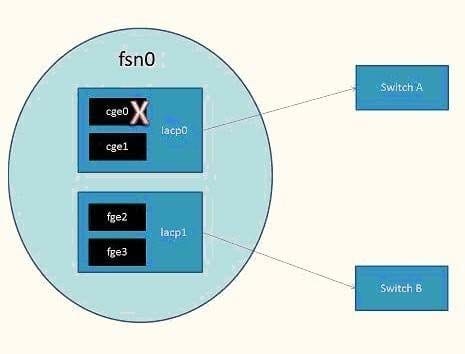
Both virtual devices (lacp0 and lacp1) are used to create another virtual device "fsn0". lacp0 is the primary.
What happens if only cge0 fails?
A. Traffic from cge0 will be redirected toward cge1, but lacp0 will still be the active path.
B. Traffic from lacp0 will be redirected toward lacp1, and manual intervention will be required to make lcap0 the active path again.
C. Traffic from lacp0 will be redirected toward lacp1 only, while cge0 is in a failed state.
D. Traffic normally traversing cge0 on lacp0 is now redirected to fge2 on lacp1.
You are setting up a Celerra unified FC model. Which UltraFlex I/O modules can be used for host connectivity?
A. 1/2/4 Gb/s module, 2/4/8 Gb/s module, iSCSI I/O modules
B. Management modules , 2/4/8 Gb/s module, iSCSI I/O modules
C. 1/2/4 Gb/s module, Management modules, iSCSI I/O modules
D. 1/2/4 Gb/s module, 2/4/8 Gb/s module, management modules
