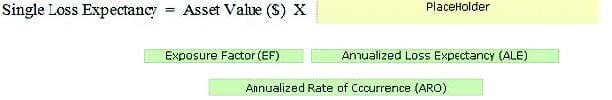
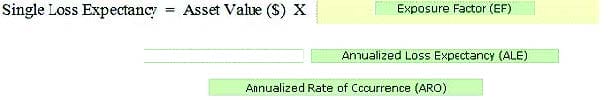
CSSLP Online Practice Questions and Answers
Which of the following organizations assists the President in overseeing the preparation of the federal budget and to supervise its administration in Executive Branch agencies?
A. OMB
B. NIST
C. NSA/CSS
D. DCAA
The Information System Security Officer (ISSO) and Information System Security Engineer (ISSE) play the role of a supporter and advisor, respectively. Which of the following statements are true about ISSO and ISSE? Each correct answer represents a complete solution. Choose all that apply.
A. An ISSE manages the security of the information system that is slated for Certification and Accreditation (CandA).
B. An ISSE provides advice on the continuous monitoring of the information system.
C. An ISSO manages the security of the information system that is slated for Certification and Accreditation (CandA).
D. An ISSE provides advice on the impacts of system changes. E. An ISSO takes part in the development activities that are required to implement system changes.
Which of the following attacks causes software to fail and prevents the intended users from accessing software?
A. Enabling attack
B. Reconnaissance attack
C. Sabotage attack D. Disclosure attack
Which of the following access control models are used in the commercial sector? Each correct answer represents a complete solution. Choose two.
A. Biba model
B. Clark-Biba model
C. Clark-Wilson model
D. Bell-LaPadula model
Which of the following is designed to detect unwanted attempts at accessing, manipulating, and disabling of computer systems through the Internet?
A. DAS
B. IPsec
C. IDS
D. ACL
Which of the following security models characterizes the rights of each subject with respect to every object in the computer system?
A. Clark-Wilson model
B. Bell-LaPadula model
C. Biba model
D. Access matrix
Which of the following are the initial steps required to perform a risk analysis process? Each correct answer represents a part of the solution. Choose three.
A. Valuations of the critical assets in hard costs.
B. Evaluate potential threats to the assets.
C. Estimate the potential losses to assets by determining their value.
D. Establish the threats likelihood and regularity.
In which of the following DIACAP phases is residual risk analyzed?
A. Phase 1
B. Phase 5
C. Phase 2
D. Phase 4
E. Phase 3
Which of the following scanning techniques helps to ensure that the standard software configuration is currently with the latest security patches and software, and helps to locate uncontrolled or unauthorized software?
A. Port Scanning
B. Discovery Scanning
C. Server Scanning
D. Workstation Scanning
Which of the following steps of the LeGrand Vulnerability-Oriented Risk Management method determines the necessary compliance offered by risk management practices and assessment of risk levels?
A. Assessment, monitoring, and assurance
B. Vulnerability management
C. Risk assessment
D. Adherence to security standards and policies for development and deployment
Which of the following are the benefits of information classification for an organization? Each correct answer represents a complete solution. Choose two.
A. It helps reduce the Total Cost of Ownership (TCO).
B. It helps identify which protections apply to which information.
C. It helps identify which information is the most sensitive or vital to an organization.
D. It ensures that modifications are not made to data by unauthorized personnel or processes.
You work as a Network Administrator for uCertify Inc. You need to secure web services of your company in order to have secure transactions. Which of the following will you recommend for providing security?
A. SSL
B. VPN
C. S/MIME
D. HTTP
The mission and business process level is the Tier 2. What are the various Tier 2 activities? Each correct answer represents a complete solution. Choose all that apply.
A. Developing an organization-wide information protection strategy and incorporating high-level information security requirements
B. Defining the types of information that the organization needs, to successfully execute the stated missions and business processes
C. Specifying the degree of autonomy for the subordinate organizations
D. Defining the core missions and business processes for the organization
E. Prioritizing missions and business processes with respect to the goals and objectives of the organization
Certification and Accreditation (CandA or CnA) is a process for implementing information security. Which of the following is the correct order of CandA phases in a DITSCAP assessment?
A. Verification, Definition, Validation, and Post Accreditation
B. Definition, Validation, Verification, and Post Accreditation
C. Definition, Verification, Validation, and Post Accreditation
D. Verification, Validation, Definition, and Post Accreditation