C2090-611 Online Practice Questions and Answers
You have an High Availability and Disaster Recovery (HADR) environment set up and you want to read from the standby database. What must you do?
A. Assign the value ON to the DB2_HADR_ROS registry variable.
B. Assign the value ON to the DB2_HADR_SNAP registry variable.
C. Execute the STOP HADR command to temporarily break the HADR connection to the standby.
D. Execute the TAKEOVER HADR command to instruct the standby database to takeover as the new primary database.
If the current value for self-tuning memory is: Self Tuning Memory (SELF_TUNING_MEM) = ON (Inactive) Which statement is true?
A. Self-tuning is occurring only on the instance memory area.
B. The memory tuner is actively tuning the memory on the system.
C. Self-tuning is not occurring because it is waiting for the database to be recycled.
D. Self-tuning is not occurring because there are less than two memory consumers enabled.
What are two types of security label components that can be used with Label-Based Access Control (LBAC)? (Choose two).
A. Set
B. Tree
C. Group
D. Range
E. Hierarchy
The following commands are executed against a database named MY_DB, which has been configured to use archival logging:
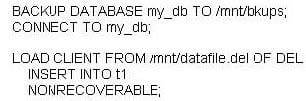
Which statement is true?
A. Upon completion of the Load, the table T1 is placed into "Backup Pending" state.
B. Upon completion of the Load, a backup image of table T1 is automatically generated.
C. After a Restore and Rollforward operation, table T1 would be marked unavailable and can only be dropped.
D. After a Restore and Rollforward operation, the loaded data is stored into a copy-image file and table T1 is fully available.
Which statement about updating index statistics with the RUNSTATS command is true?
A. It requires a full index scan.
B. It can be accomplished by sampling the index.
C. It must be executed against all indexes for the table.
D. It cannot be accomplished without scanning the associated table.
If the following command is executed:

Which statement is true?
A. Rejected records will be inserted into the table SCHEMA2.E1
B. Any indexes defined on table SCHEMA6.T1 will be marked invalid upon completion of the Load.
C. While the Load is executing, other transactions can both read and write into table SCHEMA6.T1
D. If using a remote database connection, the file "/mnt/datafile.del" must be accessible to the database server host.
If the following statement is executed:

What indexes will be created for table TAB1?
A. 1 dimension-block index and 1 composite-block index
B. 1 dimension-block index and 3 composite-block indexes
C. 3 dimension-block indexes and 1 composite-block index
D. 3 dimension-block indexes and 3 composite-block indexes
Which statement about BEFORE triggers is FALSE?
A. A BEFORE trigger's action is executed for each row in the set of affected rows before the trigger event executes.
B. A BEFORE trigger's action is executed for each row in the set of affected rows instead of executing the trigger event.
C. A BEFORE trigger is used to perform validation of input data and to automatically generate values for newly inserted rows.
D. A BEFORE trigger cannot be used to modify data in a database because they are activated before the trigger event is applied to the database.
Which command is used to export connectivity configuration information from a file known as a configuration profile?
A. db2ca
B. db2cfexp
C. db2cfimp
D. db2cfgexp
Which user-managed file system is required for DB2 pureScale deployments?
A. JFS2
B. NTFS
C. HPFS
D. GPFS
Which statement is true regarding the workload management dispatcher?
A. The workload management dispatcher monitors work performed by entities executing in the DB2 system service class.
B. The workload management dispatcher monitors the allocation of CPU resources between service classes on a system.
C. The workload management dispatcher monitors non-DB2 work performed in fenced mode processes such as fenced stored procedures.
D. The workload management dispatcher monitors work performed by applications or middleware products that perform a portion of their workoutside of the DB2 database manager.
Which command is used to import connectivity configuration information from a file known as a configuration profile?
A. db2ca
B. db2cfexp
C. db2cfimp
D. db2cfgimp
What authorization is needed to use the AUDIT statement to create an audit policy?
A. DBADM
B. SYSADM
C. SECADM
D. SYSMAINT
Given the following command: LOAD FROM newrows.del OF DEL INSERT INTO mytab ALLOW READ ACCESS Which statement(s) must be executed before applications can query the newly loaded data?
A. SET INTEGRITY FOR mytab IMMEDIATE CHECKED
B. ALTER TABLE mytab CHECK (COL IS VALIDATED)
C. ALTER TABLE mytab ALLOW READ ACCESS IMMEDIATE CHECKED
D. ALTER TABLE mytab ALLOW READ ACCESS;SET INTEGRITY FOR mytab IMMEDIATE UNCHECKED;
What must a user possess if they want to run a DB2 Command Line Processor (CLP) script against a database using the Job Manager in IBM Data Studio?
A. Permission to log in to the database client using telnet.
B. Permission to log in to the database server using telnet.
C. Permission to log in to the database client using secure shell (SSH).
D. Permission to log in to the database server using secure shell (SSH).
