C2090-610 Online Practice Questions and Answers
Which isolation level offers the greatest protection of data but provides the least amount of concurrency?
A. Read Stability (RS)
B. Cursor Stability (CS)
C. Repeatable Read (RR)
D. Uncommitted Read (UR)
What isolation level prevents dirty reads, nonrepeatable reads, and phantoms?
A. Read stability (RS)
B. Cursor stability (CS)
C. Repeatable read (RR)
D. Uncommitted read (UR)
When a COMMIT statement is executed, what happens?
A. All locks held on the database are automatically released.
B. Data stored in global temporary tables is automatically deleted.
C. Open cursors defined WITH HOLD are closed, but their data is retained.
D. The current transaction is terminated and a new transaction boundary is started.
Which is NOT a valid reason for creating an index?
A. To allow queries to run more efficiently.
B. To enforce constraints such as uniqueness on index keys.
C. To order the columns of a table in ascending or descending sequence according to values in a row.
D. To order the rows of a table in ascending or descending sequence according to the values in a column.
Which statement is true regarding constraints?
A. A table can only have one unique key constraint.
B. A table can have multiple primary key constraints.
C. Informational constraints tell DB2 what rules the data conforms to, but the rules are not enforced.
D. Foreign key constraints are enforced on the values within the rows of a table, or between the rows of two tables, by a unique index on a foreignkey.
What is used in conjunction with a foreign key to define a relationship between two tables?
A. Primary key
B. Partitioning key
C. Check constraint
D. Unique constraint
Which case will require a sequence to be dropped and recreated instead of being modified by the ALTER SEQUENCE statement?
A. Change the data type of the sequence.
B. Reset the sequence to its starting value.
C. Establish new minimum or maximum values.
D. Change the increment between future values.
In a trusted context environment, if a switch request is made with an authorization ID that is not allowed on a trusted connection, what state is the connection placed in?
A. Locked
B. Waiting
C. Pending
D. Unconnected
What privilege is required to create a view on a table that you are not the owner of?
A. INSERT
B. SELECT
C. CREATE
D. TRIGGER
What type of large object (LOB) is used to store LOB data together with the formatted rows on data pages, instead of in a separate LOB storage object?
A. inline
B. binary
C. internal
D. partitioned
Which statement about system-period temporal tables is true?
A. They store user-based period information.
B. They do not have a separate history table.
C. They can be queried without a time period specification.
D. They manage data based on time criteria specified by users or applications.
A table named DEPARTMENT contains the following data:
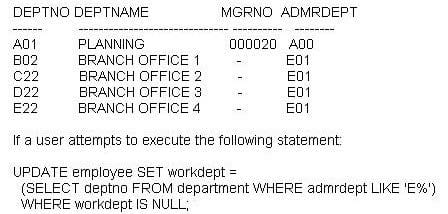
What will happen?
A. The statement will fail because a subquery cannot be used in an UPDATE statement.
B. The statement will fail because the result set produced by the subquery will contain more than one row.
C. The statement will succeed; the last record retrieved by the subquery will be used to provide a WORKDEPT value for the update operation.
D. The statement will succeed; the first record retrieved by the subquery will be used to provide a WORKDEPT value for the update operation.
Which statement regarding referential integrity constraints is true?
A. Multiple primary keys can be defined for a table.
B. A foreign key can reference multiple primary keys.
C. A primary key can be referenced by only one foreign key.
D. Primary keys and foreign keys are used to define relationships.
Which data type should be used to store data in a column that represents money and accurately returns a two position scale?
A. BIGINT
B. BINARY
C. DOUBLE
D. DECIMAL
The EXCLUSIVE MODE option of the LOCK TABLE statement is used to prevent which of the following?
A. Concurrent application processes from performing any operations on the table.
B. Concurrent application processes from performing any read-only operations on the table.
C. Concurrent applications processes that are running under the cursor stability (CS) isolation level from performing read-only operations on thetable.
D. Concurrent applications processes that are running under the uncommitted read (UR) isolation level from performing read-only operations onthe table.
