350-901 Online Practice Questions and Answers
A bot has been created, called "386231131", to respond to alarm messages. A developer is now creating a Webhook to allow the bot to respond to messages. Which format allows the Webhook to respond to messages for the bot within Webex Teams?
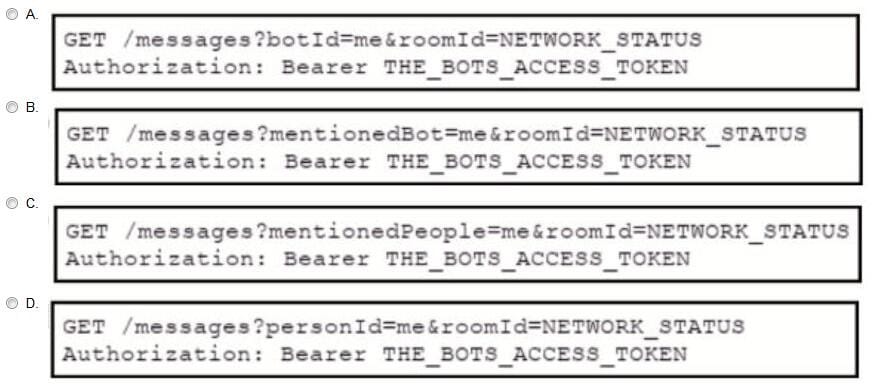
A. Option A
B. Option B
C. Option C
D. Option D
A network operations team is using the cloud to automate some of their managed customer and branch locations. They require that all of their tooling be ephemeral by design and that the entire automation environment can be recreated without manual commands. Automation code and configuration state will be stored in git for change control and versioning. The engineering high-level plan is to use VMs in a cloud- provider environment then configure open source tooling onto these VMs to poll, test, and configure the remote devices, as well as deploy the tooling itself.
Which configuration management and/or automation tooling is needed for this solution?
A. Ansible
B. Ansible and Terraform
C. NSO
D. Terraform
E. Ansible and NSO
An organization manages a large cloud-deployed application that employs a microservices architecture. No notable issues occur with downtime because the services of this application are redundantly deployed over three or more data center regions. However, several times a week reports are received about application slowness. The container orchestration logs show faults in a variety of containers that cause them to fail and then spin up brand new.
Which action must be taken to improve the resiliency design of the application while maintaining current scale?
A. Update the base image of the containers.
B. Test the execution of the application with another cloud services platform.
C. Increase the number of containers running per service.
D. Add consistent "try/catch(exception)" clauses to the code.
Which two data encoding techniques are supported by gRPC? (Choose two.)
A. XML
B. JSON
C. ASCII
D. ProtoBuf
E. YAML
Refer to the exhibit.
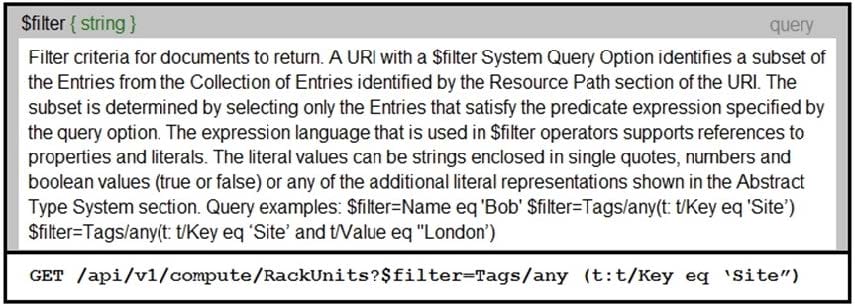
An Intersight API is being used to query RackUnit resources that have a tag keyword set to "Site". What is the expected output of this command?
A. list of all resources that have a tag with the keyword "Site"
B. error message because the Value field was not specified
C. error message because the tag filter should be lowercase
D. list of all sites that contain RackUnit tagged compute resources
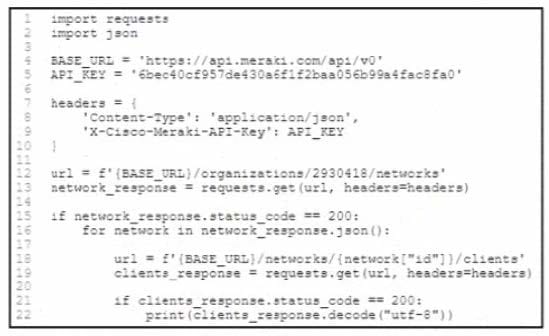
Refer to the exhibit.
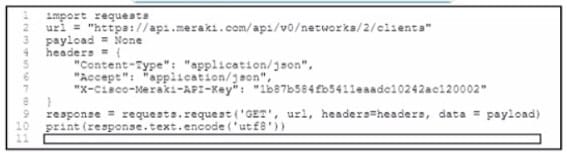
A Python script must list network clients in the Cisco Meraki API that have used a network with an ID of 2 The number of client entries per returned page is restricted to 1.000 according to the API specification Network 2 has 2.500 clients. What must be added where the code is missing to print the content of each response?

A. B. C. D.
Refer to the exhibit.
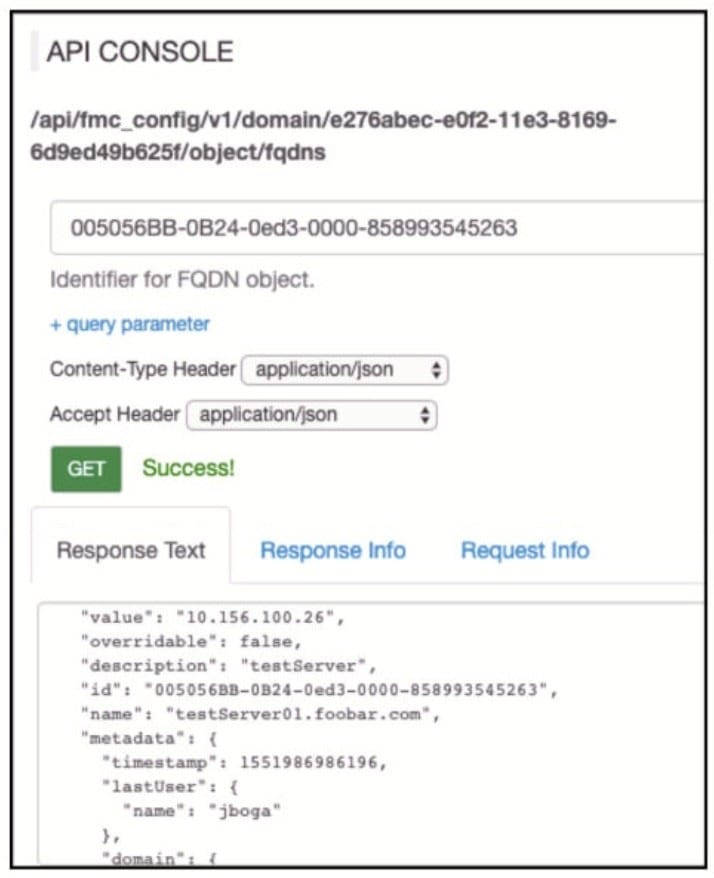
Which AP! call does an engineer use to delete the FQDN object?
A. DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f
B. DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169- 6d9ed49b625f/object/fqdns/005056BB-0B24-0ed3-0000-858993545263
C. DELETE /api/fmc_config/v1/domain?id=e276abec-e0f2-11e3-8169-6d9ed49b625f
D. DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169- 6d9ed49b625f/object/fqdns?id=005056BB-0B24-0ed3-0000-858993545263
Refer to the exhibit.
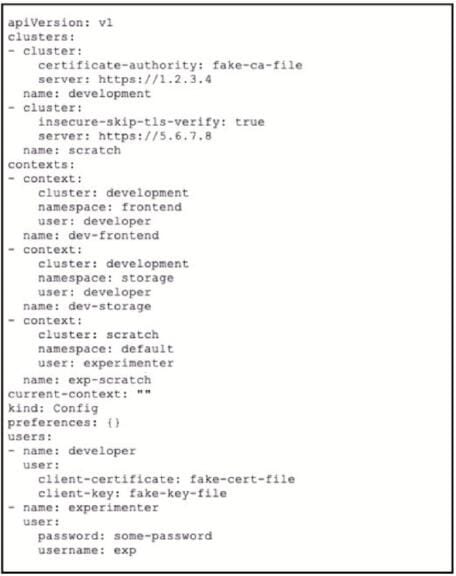
A kubeconfig file to manage access to clusters is provided. How many clusters are defined and which of them are accessed using username/password authentication versus certificate?
A. two clusters; scratch
B. three clusters; scratch
C. three clusters; development
D. two clusters; development
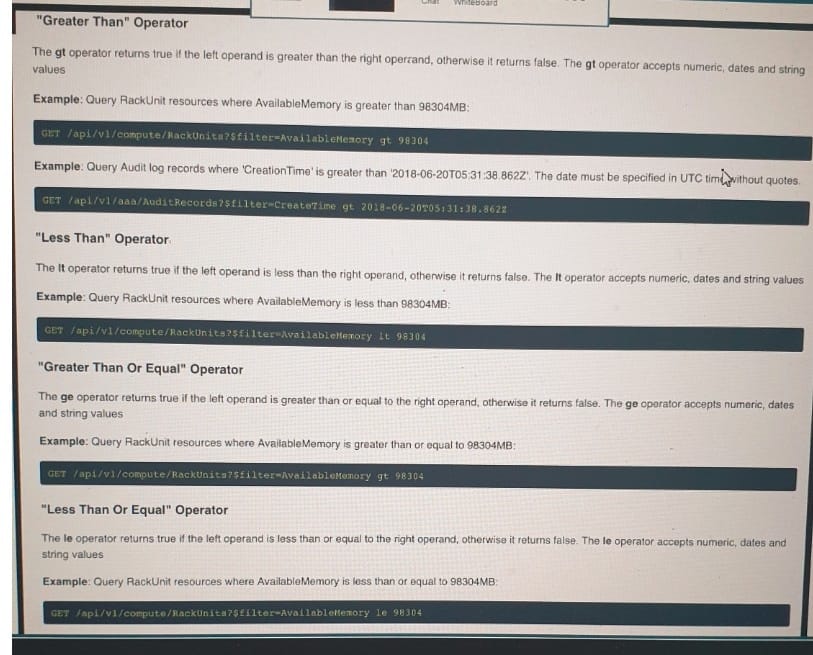
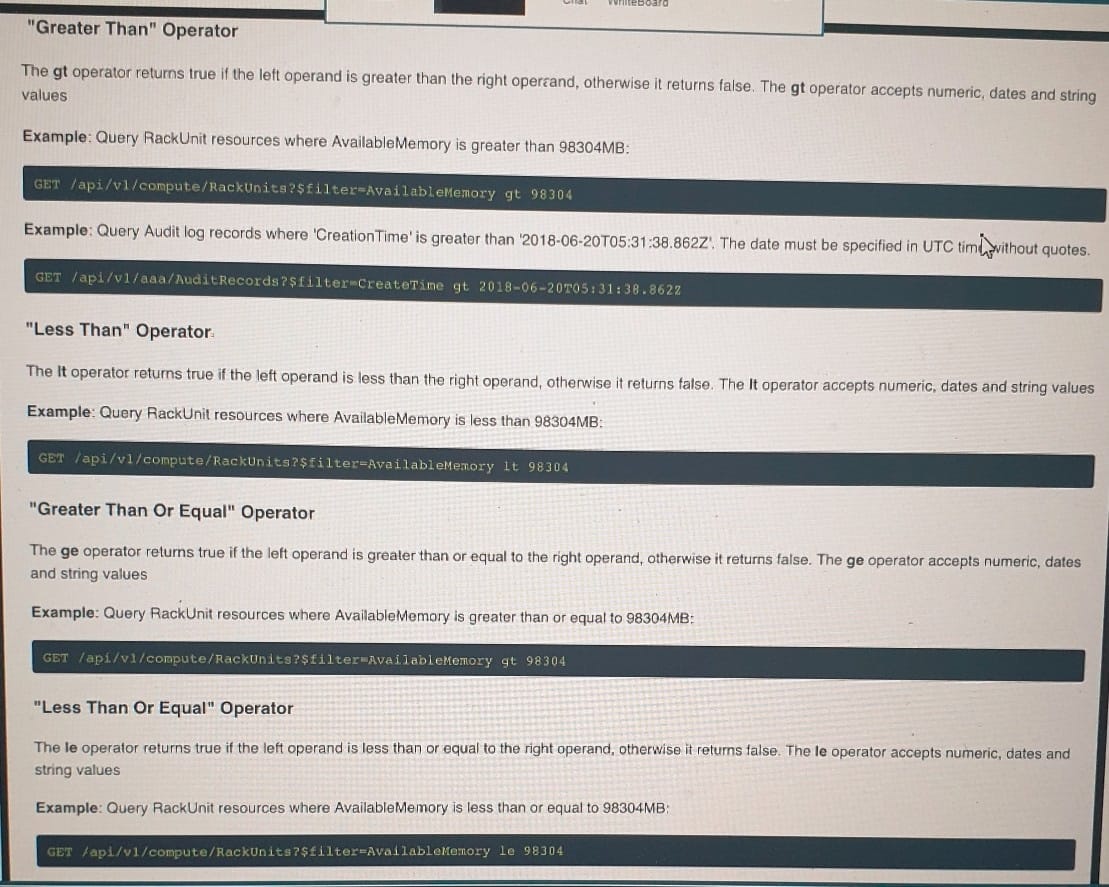
Click on the GET Resource button above to view resources that will help with this question. An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?
A. GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serialand$filter=not(Model eq `UCSC') and AvailableMemory le 5000
B. GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serialand$filter=Model eq `UCSB' and AvailableMemory lt 5000
C. GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serialand$filter=contains(Model, UCSB') and AvailableMemory lt 5000
D. GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serialand$filter=contains(Model, UCSB') and AvailableMemory le 5000
Which Puppet manifest needs to be used to configure an interface GigabitEthernet 0/1 on a Cisco IOS switch?
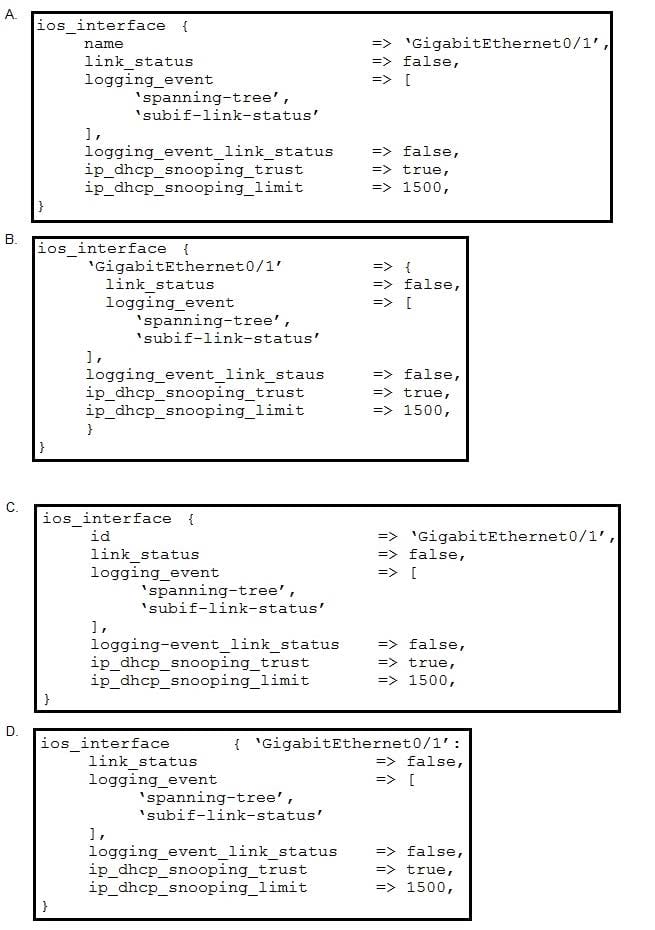
A. Option A
B. Option B
C. Option C
D. Option D
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
A. Write a log to a file in the application directory.
B. Write a log to a file in /var/log.
C. Write the logs buffered to stdout.
D. Write the logs unbuffered to stdout.
In the three-legged OAuth2 process, after the authorization server presents a form to the resource owner to grant access, what is the next step?
A. The resource owner authenticates and optionally authorizes with the authorization server.
B. The user who owns the resource initiates a request to the OAuth client.
C. If the resource owner allows access, the authorization server sends the OAuth client a redirection.
D. A form to allow or restrict access is submitted by the owner of the resource.
Refer to the exhibit.
One part of an application routinely uses the Cisco Meraki API to collate data about all clients Other parts of the application also use the Meraki API, but a single API key is used within the application The organization has approximately 4.000 clients across 30 networks Some of the application users report poor performance and missing data.
Which two changes improve the performance of the application? (Choose two.)
A. Check for HTTP code 429 and wait until Retry-After time before further calls are made
B. Configure multiple API keys in the application and rotate usage of each one.
C. Use random values in the User-Agent header when HTTP calls are made.
D. Use fewer API calls to create a more efficient endpoint.
E. Check API response payloads for later reuse in real time during code execution.
Cisco sensorBase gathers threat information from a variety of cisco products and services and performs analytics on threats. Which term describes this process?
A. consumption
B. deployment
C. sharing
D. authoring
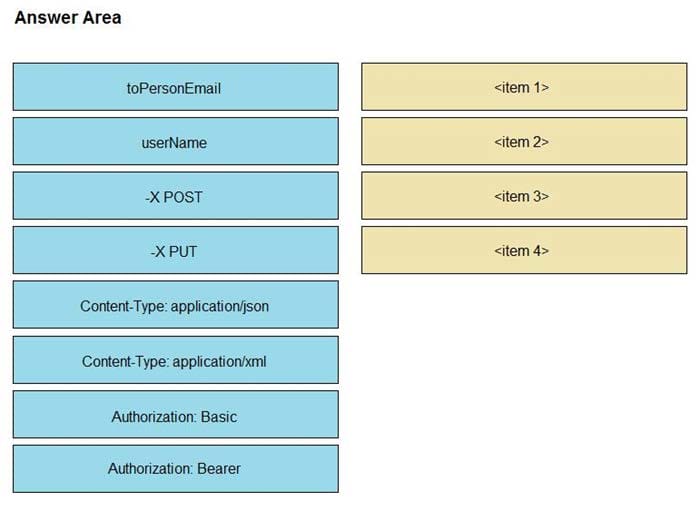
DRAG DROP
Refer to the exhibit. A system administrator has installed a Linux-based alarm system in their home that can execute a Bash shell script when an intruder is detected. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a chat-ops script that will notify of alarms via the Webex Teams REST API. Not all code snippets are used.
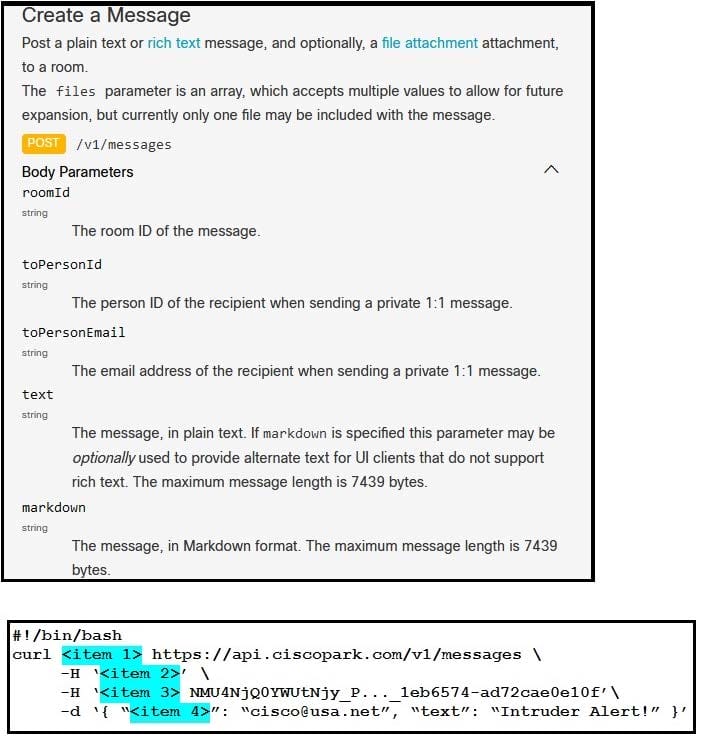
Select and Place: