350-501 Online Practice Questions and Answers
Refer to the exhibit

In which way does router R1 operate differently than router R2?
A. R1 sends LSA types 5 and 7, while R2 sends type 1, 2, and 7 LSAs.
B. R1 sends LSA type 2 only, while R2 sends type 1 and type 7 LSAs.
C. R1 sends LSA type 2 only and R2 sends LSA type 1 only.
D. R1 sends LSA types 1 and 2, while R2 sends type 1,2, and 7 LSAs.
Which three OSPF parameters must match before two devices can establish an OSPF adjacency? (Choose three.)
A. IP address
B. subnet mask
C. interface cost
D. process ID
E. area number
F. hello timer setting
Refer to the exhibit.
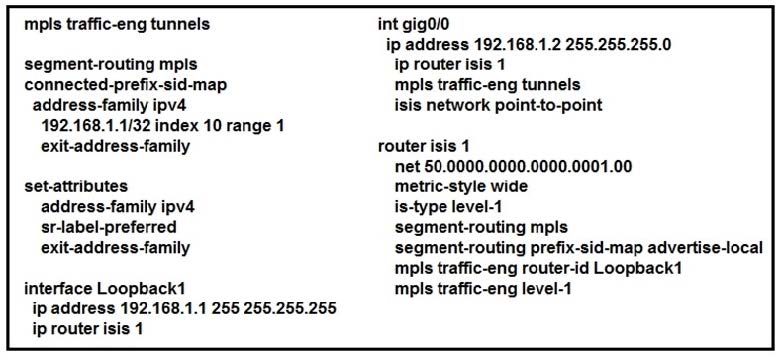
Which statement about this configuration is true?
A. It requires a dynamic Cisco MPLS TE path to be configured for the tunnel to run.
B. It requires OSPF to also be running to have optimized Cisco MPLS TE tunnels.
C. It is the configuration for the head-end router of a Cisco MPLS TE tunnel with segment routing.
D. It requires an explicit Cisco MPLS TE path to be configured for the tunnel to run.
A router RP is configured to perform MPLS LDP graceful restart.
Which three steps are included when the RP sends an LDP initialization message to a neighbor to establish an LDP session? (Choose three.)
A. Learn from Neighbor (N) flag, set to 1
B. Recovery Time field
C. Type-9 LSA
D. Reconnect Timeout field
E. Graceful restart capability in OPEN message
F. Learn from Network (L) flag, set to 1
Why do packet loops occur during the configuration of BIDIR-PIM?
A. The network does not support BIDIR-PIM.
B. The network is partially upgraded to support BIDIR-PIM.
C. The router has not been configured to advertise itself.
D. No interface for carrying traffic for multicast groups has been configured.
Which module refers to the network automation using Ansible?
A. the iosxr_system module to collect facts from remote devices
B. the iosxr_user module to manage banners for users in the local database
C. the losxr_logging module to run debugging for seventy levels 2 to 5
D. the iosxr_command module to issue run commands on remote devices
Refer to the exhibit.
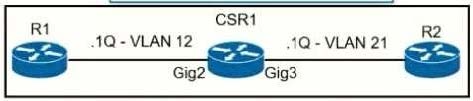
A network operator must configure CSR1 interlaces GigabitEihernet2 and GigabitEthemet to rewrite VLAN tags 12 and 21 for traffic between R1 and R2 respectively. Which configurator accomplishes this task?
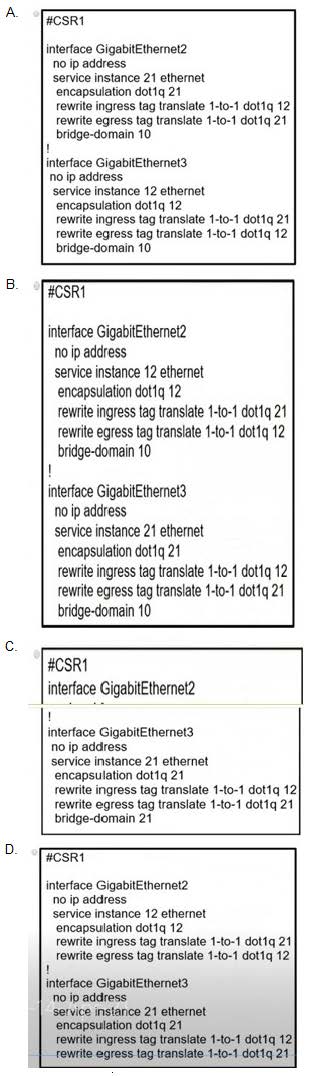
A. Option A
B. Option B
C. Option C
D. Option D
A network engineer has configured TE tunnels in the MPLS provider core. Which two steps ensure traffic traverse? (Choose two.)
A. ECMP between tunnels allows RSVP to function correctly.
B. The IGP metric of a tunnel is configured to prefer a certain path.
C. A tunnel weight is configured in SPF database the same way as a native link.
D. Static route is the only option for directing traffic into a tunnel.
E. Forwarding adjacency feature allows a tunnel to be installed in the IGP table as a link.
A company needs to improve the use of the network resources that is used to deploy internet access service to customers on separate backbone and internet access network. Which two major design models should be used to configure MPLS L3VPNs and internet service in the same MPLS backbone? (Choose two.)
A. Carriage of full internet routes in a VPN, in the case of internet access VPNS
B. Internet routing through global routing on a PE router.
C. Internet access routing as another VPN in the ISP network.
D. Internet access through leaking of internet routed from the global table into the L3VPN VRF
E. Internet access for global routing via a separate interface in a VRF
Which of the following options is true about Satellite nV System network topologies?
A. A satellite can be connected to any number of hosts in the hub-and-spoke topology model.
B. SyncE is only supported on 1 Gigabit Ethernet ICL.
C. A satellite can be connected to only one host in the hub-and-spoke topology model.
D. Delete the default SDR after verifying all nodes are in operational state.
Refer to the exhibit.
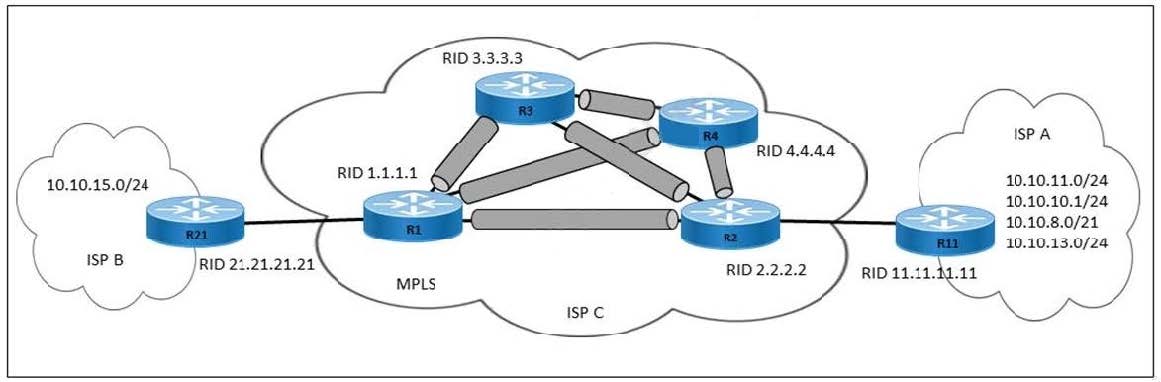
An engineer at ISP C is configuring a new interconnection with ISPs A and B using the BGP protocol. After the initial configuration, the engineer noticed high memory usage and an abnormally large LIB table on router R2. Which two actions must the engineer take on R2 to minimize memory usage? (Choose two.)
A. Configure the mpls ldp neighbor 11.11.11.11 labels accept 1 command.
B. Configure Standard ACL 1 with accepted prefixes.
C. Configure Extended ACL 101 with accepted prefixes.
D. Configure the mpls ldp neighbor 1.1.1.1 labels accept 101 command.
E. Configure the mpls ldp neighbor 21.21.21.21 labels accept 101 command.
Which OS uses a distributed subsystem architecture?
A. IOS XE
B. IOS
C. IOS XR
D. CatOS
A new PE router is configured to run OSPF as an IGP with LDP on all interfaces. The engineer is trying to prevent black holes after convergence when the PERSON device loses an LDP session with other PE routers. Which action must the engineer take to implement LDP session protection on a new PE router?
A. Configure the mpls ldp session protection and mpls label protocol ldp commands on the interfaces on the new PE router that connect to the CENTER routers.
B. Configure the mpls ldp discovery targeted-hello accept and mpls ldp session protection commands on the interfaces on the new PE router that connect to the CE routers.
C. Configure the new PE router with the mpls ldp session protection command and on neighboring routers that connect to this new PE router.
D. Configure the new PE router with the mpls ldp session protection command on interfaces with directly connected neighbors.
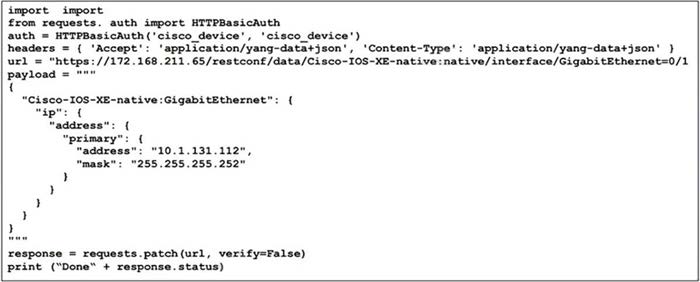
Refer to the exhibit. To optimize network operations, the senior architect created this Python 3.9 script for network automation tasks and to leverage Ansible 4.0 playbooks. Devices in the network support only RFC 2617-based authentication. What does the script do?
A. The script performs a configuration sanity check on the device with IP address 172.168.211.65 via HTTP and returns an alert if the payload field fails to match.
B. The script leverages REST API calls and configures interface GigabitEthernet0/1 with IP address 10.1.131.112/30.
C. The script parses the JSON response from the router at IP address 172.168 211.65 and checks if the interface GigabitEthernet0/1 with IP address 10.1.131.112 exists on the router.
D. The script logs in via SSH and configures interface GigabitEthernet0/1 with IP address 10 1.131.112/30.
According to RFC5305 on IS-IS extensions for traffic engineering, what is the 4-octet sub- TLV type 10 of extended IS-IS reachability TLV type 22?
A. TE default metric
B. maximum reservable link bandwidth
C. administrative group (color)
D. IPv4 neighbor address
