350-401 Online Practice Questions and Answers
SIMULATION
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
1.
Refer to the Tasks tab to view the tasks for this lab item.
2.
Refer to the Topology tab to access the device console(s) and perform the tasks.
3.
Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
4.
All necessary preconfigurations have been applied.
5.
Do not change the enable password or hostname for any device.
6.
Save your configurations to NVRAM before moving to the next item.
7.
Click Next at the bottom of the screen to submit this lab and move to the next question.
8.
When Next is clicked, the lab closes and cannot be reopened.
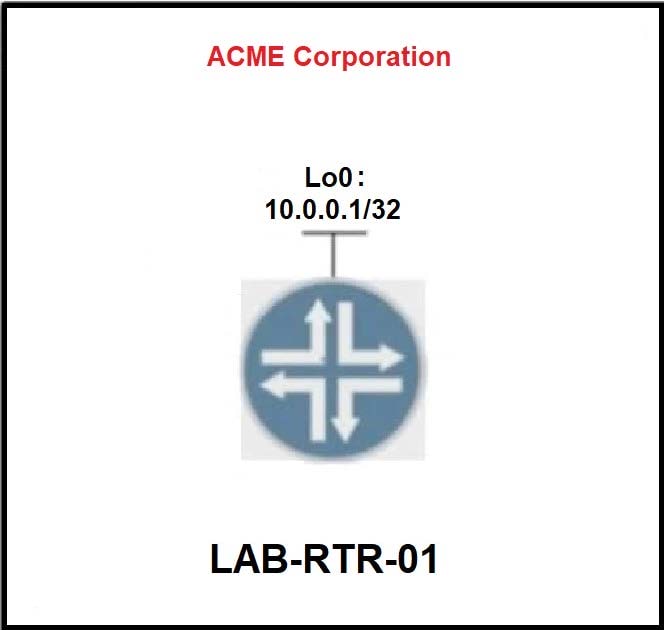
Topology
Tasks
Configure an EEM applet on LAB-RTR-01 that will automatically re-enable interface Loopback0 if it is administratively shut down.
A. See the solution below in Explanation.
B. Place Holder
C. Place Holder
D. Place Holder
DRAG DROP
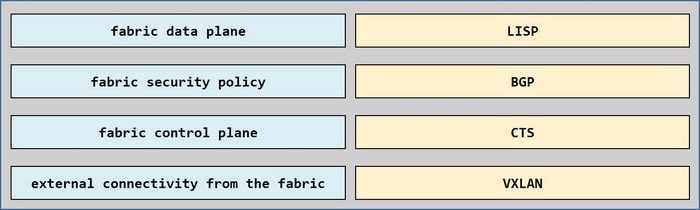
Drag and drop the Cisco SD-Access solution areas from the left onto the protocols they use on the right.
Select and Place:
Refer to the exhibit
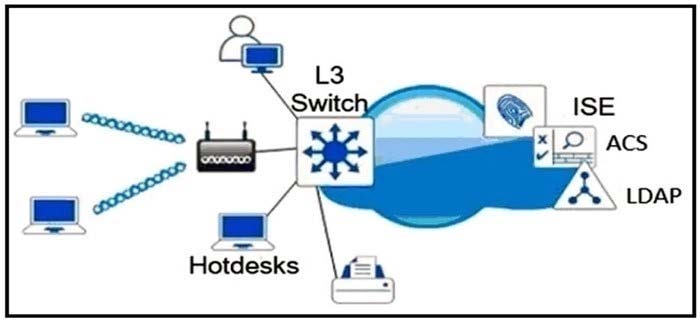
Which single security feature is recommended to provide Network Access Control m the enterprise?
A. MAB
B. 802.1X
C. WebAuth
D. port security sticky MAC
Which data is properly formatted with JSON?
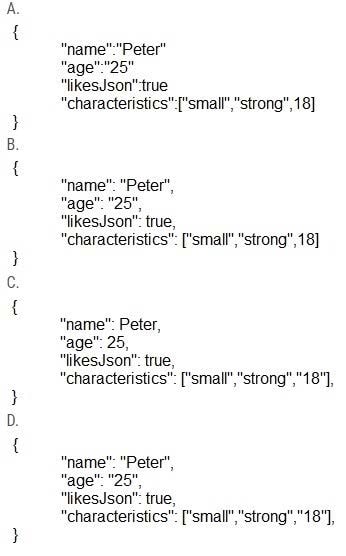
A. Opiton A
B. Opiton B
C. Opiton C
D. Opiton D
Refer to the exhibit.
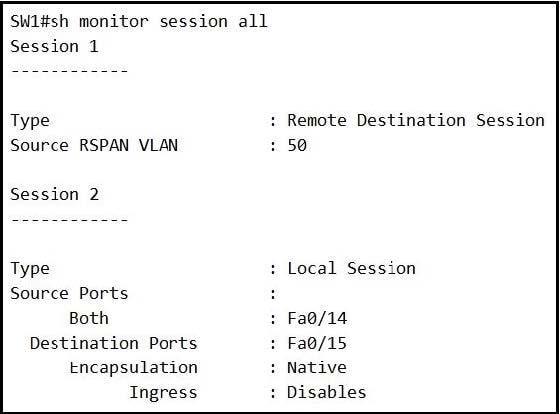
An engineer configures monitoring on SW1 and enters the show command to verify operation. What does the output confirm?
A. SPAN session 1 monitors activity on VLAN 50 of a remote switch
B. SPAN session 2 only monitors egress traffic exiting port FastEthernet 0/14.
C. SPAN session 2 monitors all traffic entering and exiting port FastEthernet 0/15.
D. RSPAN session 1 is incompletely configured for monitoring
Which antenna type should be used for a site-to-site wireless connection?
A. Omnidirectional
B. dipole
C. patch
D. Yagi
An engineer is implementing a Cisco MPLS TE tunnel to improve the streaming experience for the clients of a video-on-demand server.
Which action must the engineer perform to configure extended discovery to support the MPLS LDP session between the headend and tailend routers?
A. Configure the interface bandwidth to handle TCP and UDP traffic between the LDP peers
B. Configure a Cisco MPLS TE tunnel on both ends of the session
C. Configure an access list on the interface to permit TCP and UDP traffic
D. Configure a targeted neighbor session.
Refer to the exhibit.

enable secret CISCO aaa new-model
tacacs server ise-1 address 10.1.1.1 key cisco1231
tacacs server ISE-2 address 10.2.2.1 key cisco1231
aaa group server tacacs+ ISE-Servers server name ise-1 server name ise-2
A network engineer must configure the router to use the ISE-Servers group for authentication. If both ISE servers are unavailable, the local username database must be used. If no usernames are defined in the configuration, then the enable password must be the last resort to log in.
Which configuration must be applied to achieve this result?
A. aaa authentication login default group ISE-Servers local enable
B. aaa authentication login default group enable local ISE-Servers
C. aaa authorization exec default group ISE-Servers local enable
D. aaa authentication login error-enable
E. aaa authentication login default group enable local ISE-Servers
Refer to the exhibit.
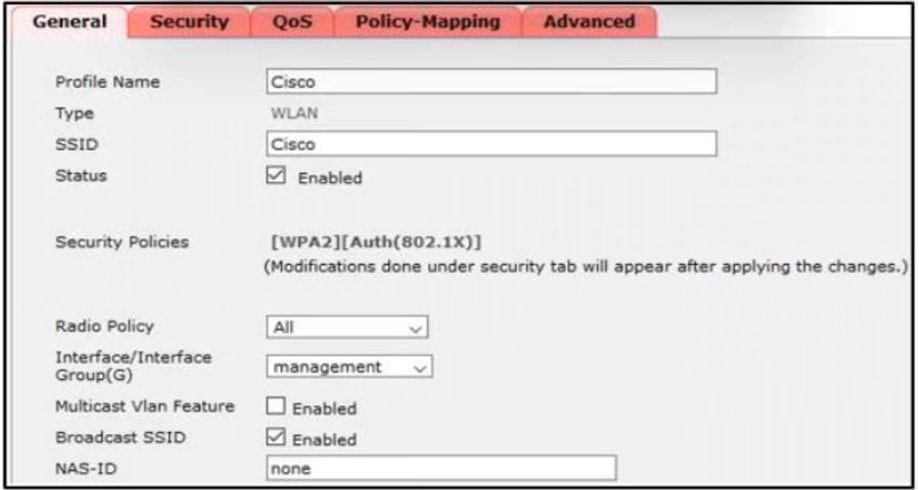
Clients report that they cannot connect to this SSID using the provided PSK. Which action will resolve this issue?
A. Apply the correct interface to this WLAN.
B. Apply the changes this SSID.
C. Select the PSK under authentication key management.
D. Define the correct Radio Policy.
Which security measure mitigates a man-in-the-middle attack of a REST API?
A. SSL certificates
B. biometric authentication
C. password hash
D. non repudiotion feature
Refer to the exhibit.
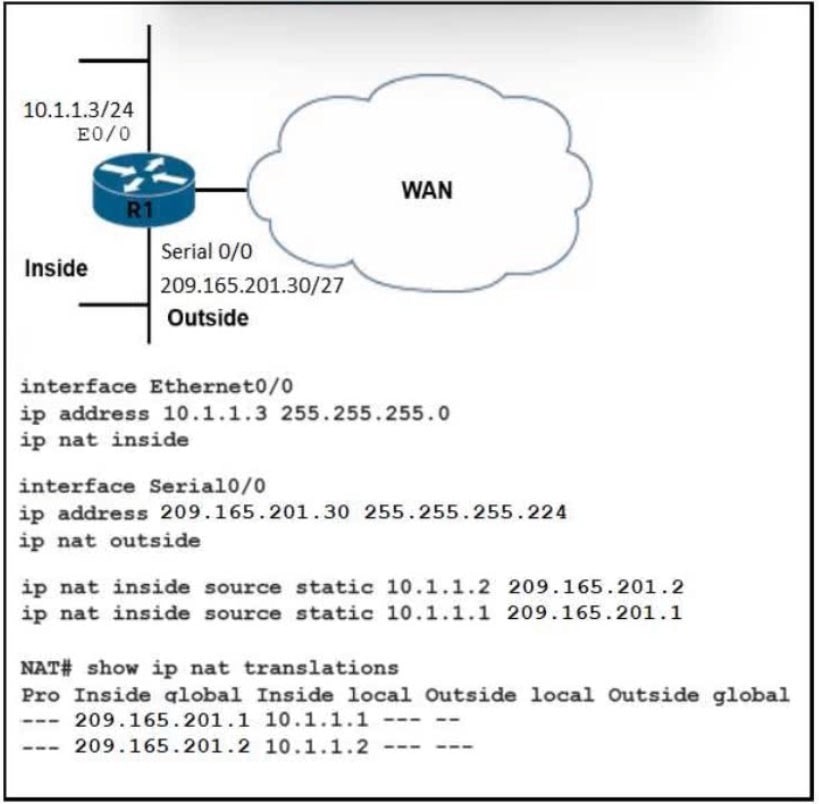
What are two results of the NAT configuration? (Choose two.)
A. Packets with a destination of 200.1.1.1 are translated to 10.1.1.1 or .2. respectively.
B. A packet that is sent to 200.1.1.1 from 10.1.1.1 is translated to 209.165.201.1 on R1.
C. R1 looks at the destination IP address of packets entering S0/0 and destined for inside hosts.
D. R1 processes packets entering E0/0 and S0/0 by examining the source IP address.
E. R1 is performing NAT for inside addresses and outside address.
By default, which virtual MAC address does HSRP group 30 use?
A. 00:05:0c:07:ac:30
B. 00:00:0c:07:ac:1e
C. 05:0c:5e:ac:07:30
D. 00:42:18:14:05:1e
Refer to the exhibit.
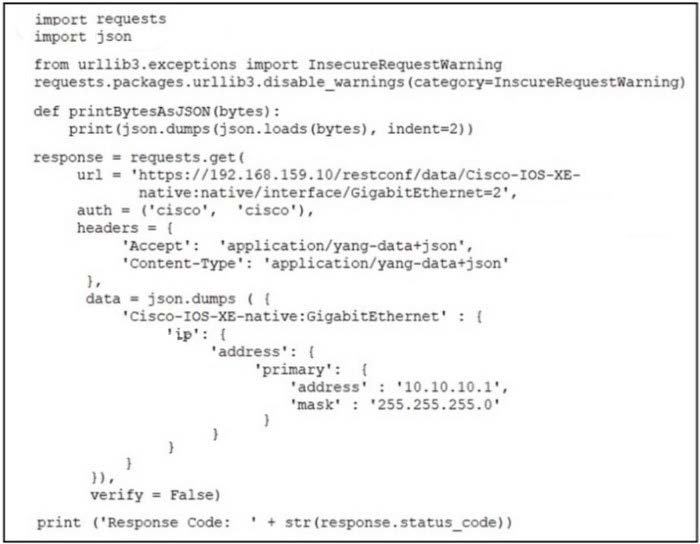
An engineer attempts to use RESTCONF to configure GigabitEthernet2 on a remote router with IP address 192.168.159.10. but the configuration fails. Which configuration is required to complete the action?

A. Option A
B. Option B
C. Option C
D. Option D
In OSPF, which LAS type is responsible for pointing to the ASBR router?
A. type 1
B. type 2
C. type 3
D. type 4
Which deployment option of Cisco NQFW provides scalability?
A. clustering
B. Inline tap
C. high availability
D. tap