312-50V12 Online Practice Questions and Answers
You are a penetration tester tasked with testing the wireless network of your client Brakeme SA. You are attempting to break into the wireless network with the SSID "Brakeme-lnternal." You realize that this network uses WPA3 encryption, which of the following vulnerabilities is the promising to exploit?
A. Dragonblood
B. Cross-site request forgery
C. Key reinstallation attack
D. AP Myconfiguration
Thomas, a cloud security professional, is performing security assessment on cloud services to identify any loopholes. He detects a vulnerability in a bare-metal cloud server that can enable hackers to implant malicious backdoors in its
firmware. He also identified that an installed backdoor can persist even if the server is reallocated to new clients or businesses that use it as an laaS.
What is the type of cloud attack that can be performed by exploiting the vulnerability discussed in the above scenario?
A. Man-in-the-cloud (MITC) attack
B. Cloud cryptojacking
C. Cloudborne attack
D. Metadata spoofing attack
What tool can crack Windows SMB passwords simply by listening to network traffic?
A. This is not possible
B. Netbus
C. NTFSDOS
D. L0phtcrack
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool "SIDExtractor". Here is the output of the SIDs:

From the above list identify the user account with System Administrator privileges.
A. John
B. Rebecca
C. Sheela
D. Shawn
E. Somia
F. Chang
G. Micah
What is the BEST alternative if you discover that a rootkit has been installed on one of your computers?
A. Copy the system files from a known good system
B. Perform a trap and trace
C. Delete the files and try to determine the source
D. Reload from a previous backup
E. Reload from known good media
Techno Security Inc. recently hired John as a penetration tester. He was tasked with identifying open ports in the target network and determining whether the ports are online and any firewall rule sets are encountered. John decided to perform a TCP SYN ping scan on the target network. Which of the following Nmap commands must John use to perform the TCP SVN ping scan?
A. nmap -sn -pp < target ip address >
B. nmap -sn -PO < target IP address >
C. Anmap -sn -PS < target IP address >
D. nmap -sn -PA < target IP address >
DNS cache snooping is a process of determining if the specified resource address is present in the DNS cache records. It may be useful during the examination of the network to determine what software update resources are used, thus
discovering what software is installed.
What command is used to determine if the entry is present in DNS cache?
A. nslookup -fullrecursive update.antivirus.com
B. dnsnooping -rt update.antivirus.com
C. nslookup -norecursive update.antivirus.com
D. dns --snoop update.antivirus.com
Your company was hired by a small healthcare provider to perform a technical assessment on the network. What is the best approach for discovering vulnerabilities on a Windows-based computer?
A. Use the built-in Windows Update tool
B. Use a scan tool like Nessus
C. Check MITRE.org for the latest list of CVE findings
D. Create a disk image of a clean Windows installation
What does the -oX flag do in an Nmap scan?
A. Perform an eXpress scan
B. Output the results in truncated format to the screen
C. Output the results in XML format to a file
D. Perform an Xmas scan
When conducting a penetration test, it is crucial to use all means to get all available information about the target network. One of the ways to do that is by sniffing the network. Which of the following cannot be performed by the passive network sniffing?
A. Identifying operating systems, services, protocols and devices
B. Modifying and replaying captured network traffic
C. Collecting unencrypted information about usernames and passwords
D. Capturing a network traffic for further analysis
The Payment Card Industry Data Security Standard (PCI DSS) contains six different categories of control objectives. Each objective contains one or more requirements, which must be followed in order to achieve compliance. Which of the following requirements would best fit under the objective, "Implement strong access control measures"?
A. Regularly test security systems and processes.
B. Encrypt transmission of cardholder data across open, public networks.
C. Assign a unique ID to each person with computer access.
D. Use and regularly update anti-virus software on all systems commonly affected by malware.
You are logged in as a local admin on a Windows 7 system and you need to launch the Computer Management Console from command line. Which command would you use?
A. c:\compmgmt.msc
B. c:\services.msc
C. c:\ncpa.cp
D. c:\gpedit
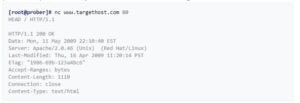
To tailor your tests during a web application scan, you decide to determine which web server version is hosting the application. Upon using the -sV flag with Nmap, you obtain the following response:
80/tcp open http-proxy Apache Server 7.1.6
What information-gathering technique does this best describe?
A. WhOiS lookup
B. Banner grabbing
C. Dictionary attack
D. Brute forcing
Which Nmap option would you use if you were not concerned about being detected and wanted to perform a very fast scan?
A. -T5
B. -O
C. -T0
D. -A
An organization has been experiencing intrusion attempts despite deploying an Intrusion Detection System (IDS) and Firewalls. As a Certified Ethical Hacker, you are asked to reinforce the intrusion detection process and recommend a better rule-based approach. The IDS uses Snort rules and the new recommended tool should be able to complement it. You suggest using YARA rules with an additional tool for rule generation. Which of the following tools would be the best choice for this purpose and why?
A. AutoYara - Because it automates the generation of YARA rules from a set of malicious and benign files
B. yarGen - Because it generates YARA rules from strings identified in malware files while removing strings that also appear in goodware files
C. YaraRET - Because it helps in reverse engineering Trojans to generate YARA rules
D. koodous - Because it combines social networking with antivirus signatures and YARA rules to detect malware