EC-COUNCIL 312-50V10 dumps - 100% Pass Guarantee!
Vendor: EC-COUNCIL
Certifications: EC-COUNCIL Certifications
Exam Name: EC-Council Certified Ethical Hacker (C|EH v10)
Exam Code: 312-50V10
Total Questions: 747 Q&As ( View Details)
Last Updated: Mar 18, 2025
Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
EC-COUNCIL 312-50V10 Last Month Results
 98.7% Pass Rate
98.7% Pass Rate 365 Days Free Update
365 Days Free Update Verified By Professional IT Experts
Verified By Professional IT Experts 24/7 Live Support
24/7 Live Support Instant Download PDF&VCE
Instant Download PDF&VCE 3 Days Preparation Before Test
3 Days Preparation Before Test 18 Years Experience
18 Years Experience 6000+ IT Exam Dumps
6000+ IT Exam Dumps 100% Safe Shopping Experience
100% Safe Shopping Experience
312-50V10 Q&A's Detail
| Exam Code: | 312-50V10 |
| Total Questions: | 747 |
| Single & Multiple Choice | 747 |
CertBus Has the Latest 312-50V10 Exam Dumps in Both PDF and VCE Format
- EC-COUNCIL_certbus_312-50V10_by_kazukin_644.pdf
- 222.17 KB
- EC-COUNCIL_certbus_312-50V10_by_AH_633.pdf
- 225.99 KB
- EC-COUNCIL_certbus_312-50V10_by_Pricq_707.pdf
- 253.76 KB
- EC-COUNCIL_certbus_312-50V10_by_greg_690.pdf
- 250.78 KB
- EC-COUNCIL_certbus_312-50V10_by_tuna_692.pdf
- 221.63 KB
- EC-COUNCIL_certbus_312-50V10_by_Jaspreet_715.pdf
- 221.88 KB
312-50V10 Online Practice Questions and Answers
You are looking for SQL injection vulnerability by sending a special character to web applications. Which of the following is the most useful for quick validation?
A. Double quotation
B. Backslash
C. Semicolon
D. Single quotation
What is the least important information when you analyze a public IP address in a security alert?
A. ARP
B. Whois
C. DNS
D. Geolocation
Which of the following items is unique to the N-tier architecture method of designing software applications?
A. Application layers can be separated, allowing each layer to be upgraded independently from other layers.
B. It is compatible with various databases including Access, Oracle, and SQL.
C. Data security is tied into each layer and must be updated for all layers when any upgrade is performed.
D. Application layers can be written in C, ASP.NET, or Delphi without any performance loss.
If there is an Intrusion Detection System (IDS) in intranet, which port scanning technique cannot be used?
A. Spoof Scan
B. TCP Connect scan
C. TCP SYN
D. Idle Scan
While reviewing the result of scanning run against a target network you come across the following:
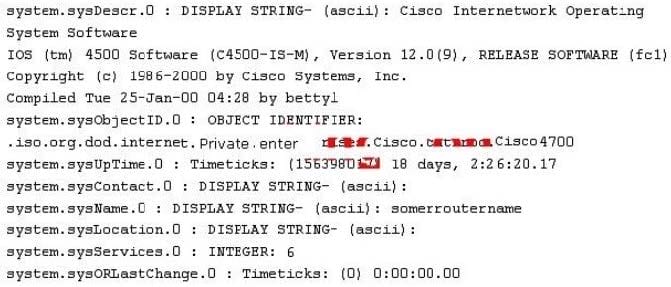
Which among the following can be used to get this output?
A. A Bo2k system query.
B. nmap protocol scan
C. A sniffer
D. An SNMP walk
Add Comments
Success Stories
- Italy
- makarra
- Mar 16, 2025
- Rating: 4.5 / 5.0
![]()
This dump is 100% valid, today I passed my exam. Just some choices were rearranged but n total the exams easy.
- United States
- Ranjani
- Mar 13, 2025
- Rating: 4.9 / 5.0
![]()
This dump is 100% valid. The information is concise and to the point. Everything that you need to know for your exam is contained in these questions. I passed the exam on my first try using this dump and two textbooks as the study guide. Wish you luck.


 Printable PDF
Printable PDF