312-49V10 Online Practice Questions and Answers
Computer forensics report provides detailed information on complete computer forensics investigation process. It should explain how the incident occurred, provide technical details of the incident and should be clear to understand. Which of the following attributes of a forensics report can render it inadmissible in a court of law?
A. It includes metadata about the incident
B. It includes relevant extracts referred to In the report that support analysis or conclusions
C. It is based on logical assumptions about the incident timeline
D. It maintains a single document style throughout the text
Microsoft Security IDs are available in Windows Registry Editor. The path to locate IDs in Windows 7 is:
A. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion \ProfileList
B. HKEY_LOCAL_MACHlNE\SOFTWARE\Microsoft\Windows NT\CurrentVersion \NetworkList
C. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentsVersion \setup
D. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule
Jason, a renowned forensic investigator, is investigating a network attack that resulted in the compromise of several systems in a reputed multinational's network. He started Wireshark to capture the network traffic. Upon investigation, he found that the DNS packets travelling across the network belonged to a non-company configured IP. Which of the following attack Jason can infer from his findings?
A. DNS Poisoning
B. Cookie Poisoning Attack
C. DNS Redirection
D. Session poisoning
When a file or folder is deleted, the complete path, including the original file name, is stored in a special hidden file called "INF02" in the Recycled folder. If the INF02 file is deleted, it is re-created when you___________.
A. Restart Windows
B. Kill the running processes in Windows task manager
C. Run the antivirus tool on the system
D. Run the anti-spyware tool on the system
You are the network administrator for a small bank in Dallas, Texas. To ensure network security, you enact a security policy that requires all users to have 14 character passwords. After giving your users 2 weeks notice, you change the Group Policy to force 14 character passwords. A week later you dump the SAM database from the standalone server and run a password-cracking tool against it. Over 99% of the passwords are broken within an hour. Why were these passwords cracked so Quickly?
A. Passwords of 14 characters or less are broken up into two 7-character hashes
B. A password Group Policy change takes at least 3 weeks to completely replicate throughout a network
C. Networks using Active Directory never use SAM databases so the SAM database pulled was empty
D. The passwords that were cracked are local accounts on the Domain Controller
To make sure the evidence you recover and analyze with computer forensics software can be admitted in court, you must test and validate the software. What group is actively providing tools and creating procedures for testing and validating computer forensics software ?
A. Computer Forensics Tools and Validation Committee (CFTVC)
B. Association of Computer Forensics Software Manufactures (ACFSM)
C. National Institute of Standards and Technology (NIST)
D. Society for Valid Forensics Tools and Testing (SVFTT)
Which federal computer crime law specifically refers to fraud and related activity in connection with access devices like routers?
A. 18 U.S.C. 1029
B. 18 U.S.C. 1362
C. 18 U.S.C. 2511
D. 18 U.S.C. 2703
What is considered a grant of a property right given to an individual who discovers or invents a new machine, process, useful composition of matter or manufacture?
A. Copyright
B. Design patent
C. Trademark
D. Utility patent
A forensics investigator needs to copy data from a computer to some type of removable media so he can examine the information at another location. The problem is that the data is around 42GB in size. What type of removable media could the investigator use?
A. Blu-Ray single-layer
B. HD-DVD
C. Blu-Ray dual-layer
D. DVD-18
Which code does the FAT file system use to mark the file as deleted?
A. ESH
B. 5EH
C. H5E
D. E5H
Which of the following commands shows you all of the network services running on Windows-based servers?
A. Netstart
B. Net Session
C. Net use
D. Net config
When marking evidence that has been collected with the “aaa/ddmmyy/nnnn/zz” format, what does the “nnnn” denote?
A. The initials of the forensics analyst
B. The sequence number for the parts of the same exhibit
C. The year he evidence was taken
D. The sequential number of the exhibits seized by the analyst
What does 254 represent in ICCID 89254021520014515744?
A. Industry Identifier Prefix
B. Country Code
C. Individual Account Identification Number
D. Issuer Identifier Number
Buffer overflow vulnerability of a web application occurs when it fails to guard its buffer properly and allows writing beyond its maximum size. Thus, it overwrites the_________. There are multiple forms of buffer overflow, including a Heap Buffer Overflow and a Format String Attack.
A. Adjacent memory locations
B. Adjacent bit blocks
C. Adjacent buffer locations
D. Adjacent string locations
What is the investigator trying to view by issuing the command displayed in the following screenshot?
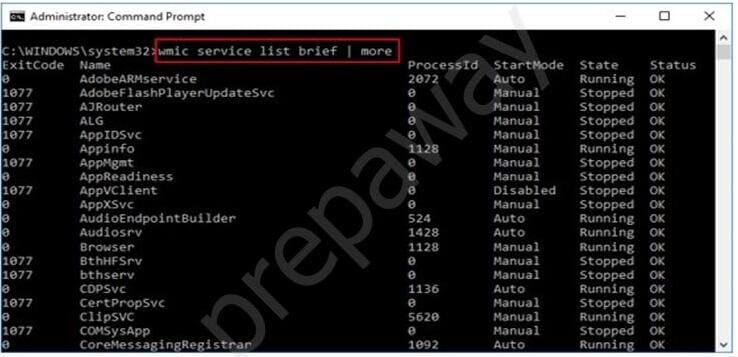
A. List of services stopped
B. List of services closed recently
C. List of services recently started
D. List of services installed
