300-735 Online Practice Questions and Answers
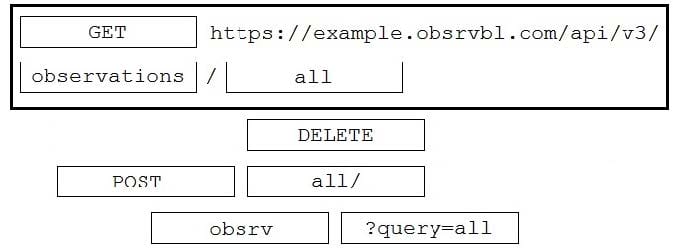
DRAG DROP
Drag and drop the code to complete the API call to query all Cisco Stealthwatch Cloud observations. Not all options are used.
Select and Place:

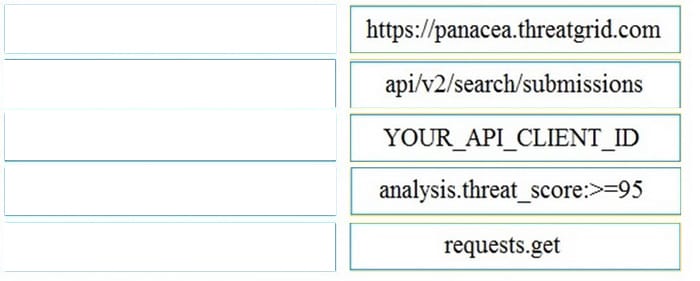
DRAG DROP
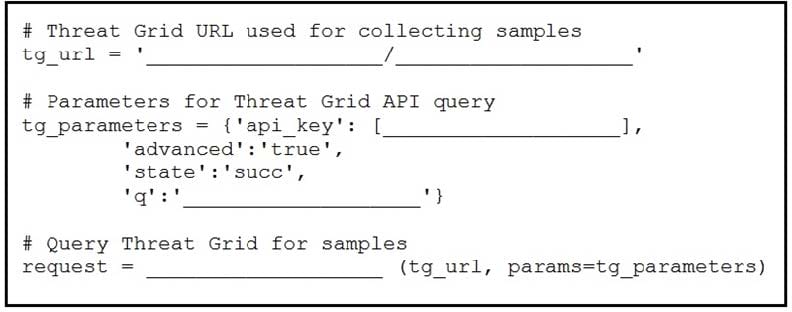
Refer to the exhibit.
Drag and drop the elements from the left onto the script on the right that queries Cisco ThreatGRID for indications of compromise.
Select and Place:

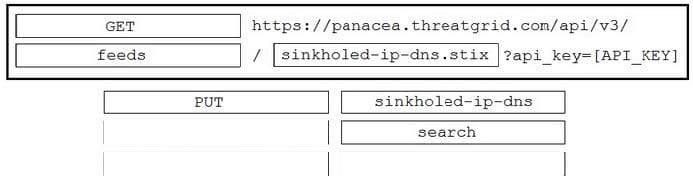
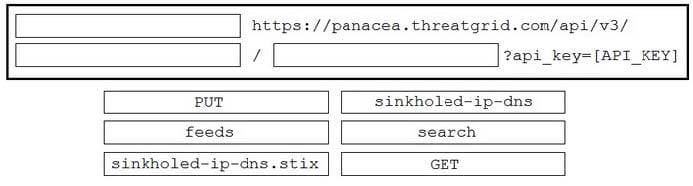
DRAG DROP
Drag and drop the items to complete the ThreatGRID API call to return a curated feed of sinkholed-ip-dns in stix format. Not all options are used.
Select and Place:
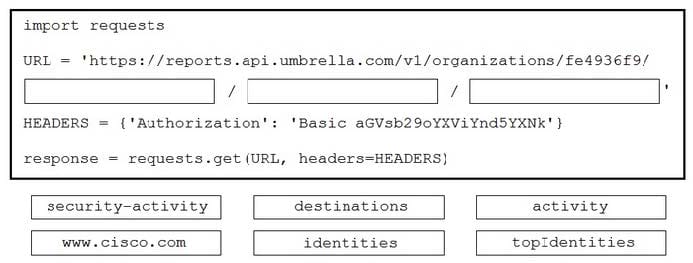
DRAG DROP
A Python script is being developed to return the top 10 identities in an organization that have made a DNS request to "www.cisco.com".
Drag and drop the code to complete the Cisco Umbrella Reporting API query to return the top identities. Not all options are used.
Select and Place:
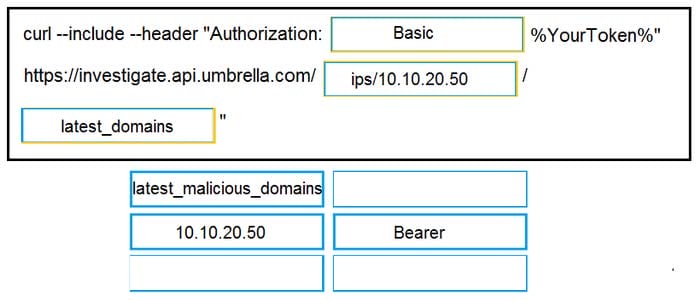
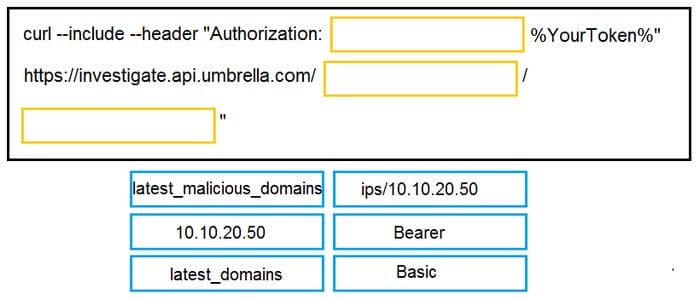
DRAG DROP
Drag and drop the code to complete the curl query to the Cisco Umbrella Investigate API for the Latest Malicious Domains for the IP address 10.10.20.50. Not all options are used.
Select and Place:
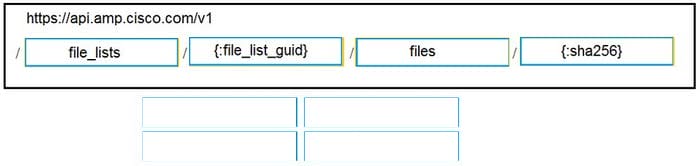
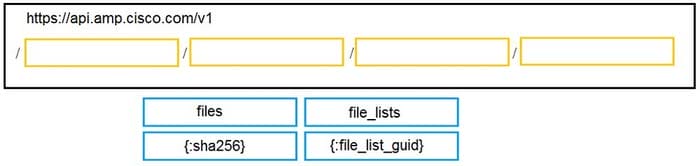
DRAG DROP
Drag and drop the code to complete the URL for the Cisco AMP for Endpoints API POST request so that it will add a sha256 to a given file_list using file_list_guid.
Select and Place:
Refer to the exhibit.
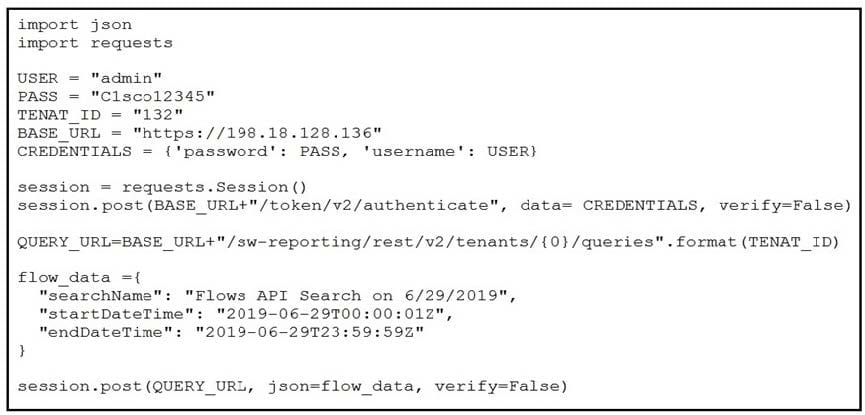
A network operator must generate a daily flow report and learn how to act on or manipulate returned data. When the operator runs the script, it returns an enormous amount of information. Which two actions enable the operator to limit returned data? (Choose two.)
A. Add recordLimit. followed by an integer (key:value) to the flow_data.
B. Add a for loop at the end of the script, and print each key value pair separately.
C. Add flowLimit, followed by an integer (key:value) to the flow_data.
D. Change the startDateTime and endDateTime values to include smaller time intervals.
E. Change the startDate and endDate values to include smaller date intervals.
Which two destinations are supported by the Cisco Security Management Appliance reporting APIs? (Choose two.)
A. email
B. Microsoft Word file
C. FTP
D. web
E. csv file
Refer to the exhibit.
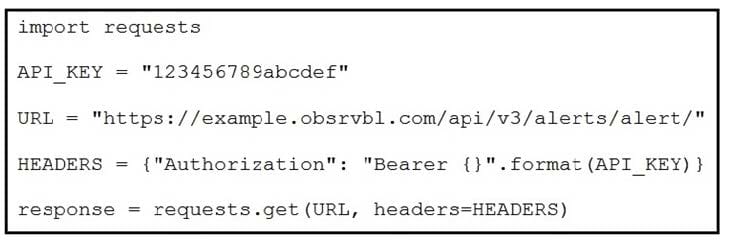
A security engineer created a script and successfully executed it to retrieve all currently open alerts. Which print command shows the first returned alert?
A. print(response[data][0])
B. print(response[results][0])
C. print(response.json()[data][0])
D. print(response.json()[results][0])
Which two statements describe the characteristics of API styles for REST and RPC? (Choose two.)
A. REST-based APIs function in a similar way to procedures.
B. REST-based APIs are used primarily for CRUD operations.
C. REST and RPC API styles are the same.
D. RPC-based APIs function in a similar way to procedures.
E. RPC-based APIs are used primarily for CRUD operations.
Refer to the exhibit.

What must be present in a Cisco Web Security Appliance before the script is run?
A. reporting group with the name web_malware_category_malware_name_user_detail
B. data for specified dates
C. reporting group with the name blocked_malware
D. data in the queried category
Which two APIs are available from Cisco ThreatGRID? (Choose two.)
A. Access
B. User Scope
C. Data
D. Domains
E. Curated Feeds
Which snippet describes the way to create an URL object in Cisco FDM using FDM REST APIs with curl?
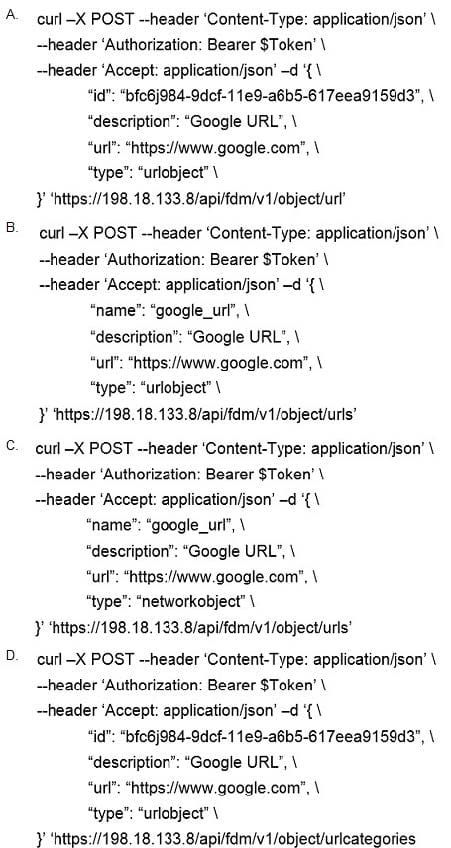
A. Option A
B. Option B
C. Option C
D. Option D
Refer to the exhibit.

What is the purpose of the API represented by this URL?
A. Getting or setting intrusion policies in FMC
B. Creating an intrusion policy in FDM
C. Updating access policies
D. Getting the list of intrusion policies configured in FDM
Which step is required by Cisco pxGrid providers to expose functionality to consumer applications that are written in Python?
A. Look up the existing service using the /pxgrid/control/ServiceLookup endpoint.
B. Register the service using the /pxgrid/control/ServiceRegister endpoint.
C. Configure the service using the /pxgrid/ise/config/profiler endpoint.
D. Expose the service using the /pxgrid/ise/pubsub endpoint.