300-620 Online Practice Questions and Answers
All workloads in VLAN 1001 have been migrated into EPG-1001. The requirement is to move the gateway address for VLAN 1001 from the core outside the Cisco ACI fabric into the Cisco ACI fabric. The endpoints in EPG-1001 must route traffic to endpoints in other EPGs and minimize flooded traffic in the fabric. Which configuration set is needed on the bridge domain to meet these requirements?
A. Enable Flood Enable Unicast Routing
B. Disable Local IP Learning Limit Disable Unicast Routing
C. Disable ARP Flood Disable Limit Endpoint Learning
D. Enable Hardware Proxy Enable Unicast Routing
Refer to the exhibit.
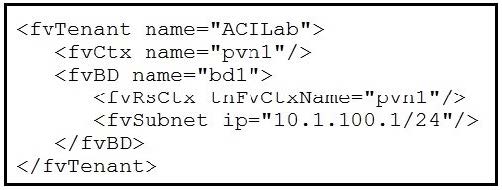
Which two objects are created as a result of the configuration? (Choose two.)
A. application profile
B. attachable AEP
C. bridge domain
D. endpoint group
E. VRF
What happens to the traffic flow when the Cisco ACI fabric has a stale endpoint entry for the destination endpoint?
A. The leaf switch does not learn the source endpoint through data plane learning.
B. The leaf switch drops the traffic that is destined to the endpoint.
C. The leaf switch floods the traffic to the endpoint throughout the fabric.
D. The leaf switch sends the traffic to the wrong destination leaf.
When configuring Cisco ACI VMM domain integration with VMware vCenter, which object is created in vCenter?
A. datacenter
B. VMware vSphere Standard vSwitch
C. VMware vSphere Distributed Switch
D. cluster
An engineer has set the VMM resolution immediacy to pre-provision in a Cisco ACI environment. No Cisco Discovery Protocol neighborship has been formed between the hypervisors and the ACI fabric leaf nodes.
How does this affect the download policies to the leaf switches?
A. No policies are downloaded because LLDP is the only supported discovery protocol.
B. Policies are downloaded when the hypervisor host is connected to the VMM VDS.
C. Policies are downloaded to the ACI leaf switch regardless of Cisco Discovery Protocol neighborship.
D. No policies are downloaded because there is no discovery protocol neighborship.
Which tenant is used when configuring in-band management IP addresses for Cisco APICs, leaf nodes, and spine nodes?
A. default
B. infra
C. common
D. mgmt
Which two IP address types are available for transport over the ISN when they are configured from Cisco ACI Multi-Site Orchestrator? (Choose two.)
A. Management IP of APICs
B. Management IP of the MSO Node
C. Anycast Overlay Multicast TEP
D. MP-BGP EVPN Router-ID
E. Common Pervasive Gateway
Refer to the exhibit.

The 0.0.0.0/0 is configured as a default static route on L3Out-1. Which action should be taken for the 0.0.0.0/0 prefix to advertise out on L3Out-2 OSPF?
A. Enable Export Route Control Subnet.
B. Enable Shared Security Import Subnet.
C. Enable Shared Route Control Subnet.
D. Enable Aggregate Export Subnet.
Refer to the exhibit.
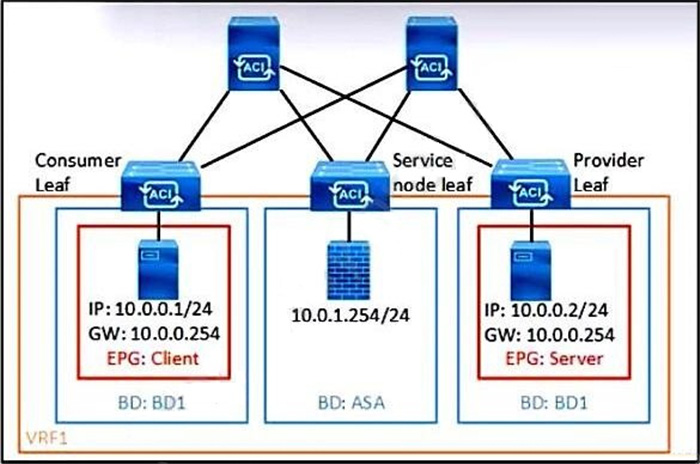
What must be configured in the service graph to redirect HTTP traffic between the EPG client and EPG server to go through the Cisco ASA firewall?
A. precise filter to allow only HTTP traffic
B. permit-all contract filter
C. contract with no filter
D. contract filter to allow ARP and HTTP.
A customer is deploying a new application across two ACI pods that is sensitive to latency and jitter. The application sets the DSCP values of packets to AF31 and CS6, respectively. Which configuration changes must be made on the APIC to support the new application and prevent packets from being delayed or dropped between pods?
A. disable DSCP mapping on the IPN devices
B. disable DSCP translation policy
C. align the ACI QoS levels and IPN QoS policies
D. align the custom QoS policy on the EPG site in the customer tenant
Which protocol is used in a Multi-Pod topology to synchronize reachability information across pods?
A. MP-BGP EVPN
B. OSPF
C. IS-IS
D. COOP
A recent set of changes by a Cisco ACI administrator corrupted the APIC cluster. The ACI engineer must restore the configuration of the previous day. The APIC nodes in the cluster can communicate but fail to connect with other networks. The administrator plans to overwrite the entire existing configuration with the backup configuration. Which set of actions accomplishes this task?
A. Restore using the last configuration on the factory-reset APIC. Use an import policy set to Best-effort.
B. Roll back the configuration using a local snapshot. Use an import policy set to Atomic Replace.
C. Roll back the configuration using a local snapshot. Use an import policy set to Best-effort Merge.
D. Restore the configuration imported from an FTP server. Use an import policy set to Atomic.
An engineer must implement user activity tracking in the Cisco ACI with a solution that meets these requirements:
1.
All user activity that is related to the Cisco ACI infrastructure hardware must be tracked.
2.
All audit logs with severity level 5 and below must be collected and exported.
3.
Logs must be exported to a Security Information and Event Management (SIEM) appliance.
Which set of steps must be taken?
A. Create a Syslog Monitoring Destination Group with a remote destination of the SIEM device. Create a Tenant-level Syslog Source under the Monitoring section of the Tenant Tab. Select Audit Logs and a severity level of Warning,
B. Create a Syslog Monitoring Destination Group with a Local File destination. Create an Access-level Syslog Source under the Monitoring section of the Fabric Tab. Select Fault Logs and a severity level of Notification.
C. Create a Syslog Monitoring Destination Group with a remote destination of the SIEM device. Create a Fabric-level Syslog Source under the Monitoring section of the Fabric Tab. Select Audit Logs and a severity level of Notification.
D. Create a Syslog Monitoring Destination Group with Console Destination. Create a System-level Syslog Source under the Monitoring section of the System Tab. Select Session Logs and a severity level of Warning.
A Cisco APIC is configured to authenticate users by using RADIUS by default. The network administrator must ensure that the users can access the APIC GUI with a local account if the RADIUS server is unreachable. Which action achieves this goal?
A. Enable Fallback Check for Default Authentication.
B. Configure the fallback login domain to reference Local Realm.
C. Set RADIUS Realm to connect with Console Authentication.
D. Create an additional login domain to associate with local accounts.
A Cisco ACI fabric is integrated with a VMware environment. The engineer must back up the current configuration of the fabric and restore the vCenter password when the configuration is imported. Which action accomplishes this goal?
A. Create a Configuration Import Policy.
B. Select SCP protocol for the remote location.
C. Enable the Global AES Encryption setting.
D. Set the Authentication type to Use Password.
