300-415 Online Practice Questions and Answers
What is a default protocol for control plane connection?
A. HTTPS
B. TLS
C. IPsec
D. DTLS
On which device is a service FW address configured to insert firewall service at the hub?
A. vSmart at the branch
B. vEdge at the branch
C. vEdge at the hub
D. vSmart at the hub
In which VPN is the NAT operation on an outgoing interface configured for direct Internet access?
A. 0
B. 512
C. 10
D. 1
At which layer does the application-aware firewall block applications on a WAN Edge?
A. 3
B. 5
C. 2
D. 7
Refer to the exhibit. Which QoS treatment results from this configuration after the access list acl-guest is applied inbound on the vpn1 interface?
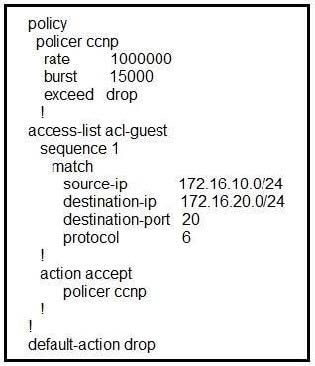
A. A TCP packet sourcing from 172.16.10.1 and destined to 172.16.20.1 is dropped
B. A UDP packet sourcing from 172.16.20.1 and destined to 172.16.10.1 is accepted
C. A UDP packet sourcing from 172.16.10.1 and destined to 172.16.20.1 is dropped
D. A TCP packet sourcing from 172.16.20.1 and destined to 172.16.10.1 is accepted
What is a benefit of the application aware firewall feature in the Cisco SD-WAN solution?
A. application monitoring
B. application malware protection
C. application visibility
D. control policy enforcement
What is the purpose of “vpn 0” in the configuration template when onboarding a WAN Edge node?
A. It carries control traffic over secure IPsec connections between vSmart controllers and vEdge routers, and between vSmart and vManager
B. It carries control out-of-bond network management traffic among the Viptela devices in the overlay network.
C. It carries control traffic over secure IPsec connections between vSmart controllers and vEdge routers, and between vSmart and vManager
D. It carries control traffic over secure DTLS or TLS connections between vSmart controllers and vEdge routers, and between vSmart and vBond
If Smart Account Sync is not used, which Cisco SD-WAN component Is used to upload an authorized serial number file?
A. WAN Edge
B. vManage
C. vSmart
D. vBond
An engineer must use data prefixes to configure centralized data policies using the vManage policy configuration wizard. What is the first step to accomplish this task?
A. Configure network topology.
B. Apply policies to sites and VPNs.
C. Configure traffic rules.
D. Create groups of interest.
Which vBond system configuration under VPN 0 allows for a routable public IP address even if the DNS name, hostname, or IP address of the vBond orchestrator are omitted?
A. WAN
B. local
C. dns-name
D. vbond-only
An administrator modifies an application-aware routing policy to support newly deployed file servers. File transfers must be sent over the Internet-bound transports first and only use MPLS-bound transports as a backup. This policy is configured:
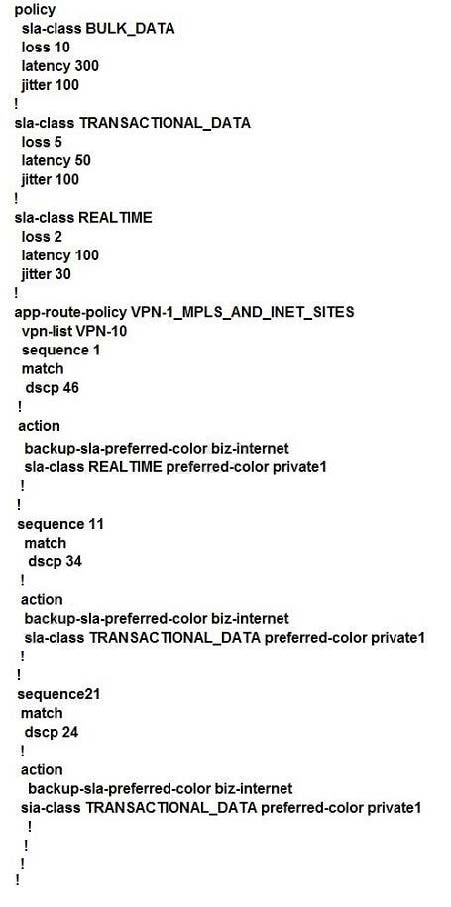
Which configuration sequence meets the requirements?

A. Option A
B. Option B
C. Option C
D. Option D
Refer to the exhibit.
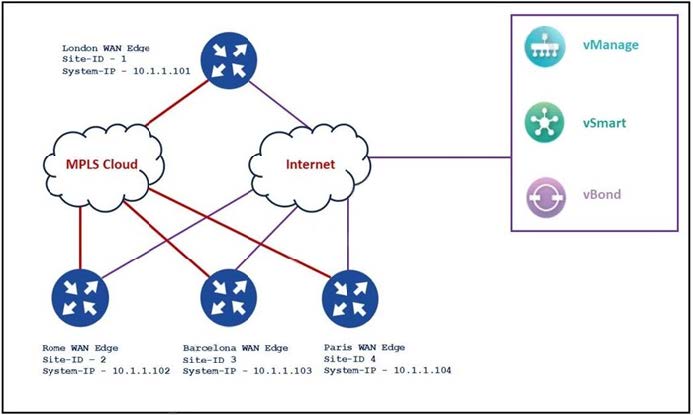
An engineer configures Rome WAN Edge to use MPLS cloud as the preferred link to reach Paris WAN Edge and use biz-internet as a backup. Which policy configuration must be applied in the outbound direction toward Rome to accomplish the task?

A. Option A
B. Option B
C. Option C
D. Option D
Which VManage dashboard is used to monitor the next-hop reachability between two devices traversing through OMP for a service VPN'
A. Troubleshooting > App Route Visualization
B. Troubleshooting > Tunnel Health
C. Troubleshooting > Simulate Flows
D. Troubleshooting > Packet Capture
How do WAN Edge devices operate when vSmart is inaccessible or fails to be reached by the WAN Edge?
A. They cease to forward traffic in the data plane.
B. They continue operation normally.
C. They continue to receive reachability updates.
D. They continue operating normally for a configurable time.
Which protocol runs between the vSmart controllers and WAN Edge routers when the vSmart controller acts like a route reflector?
A. IPsec inside the DTLS/TLS control connection
B. BGP inside the DTLS/TLS
C. OMP outside the DTLS/TLS control connection
D. OMP inside the DTLS/TLS control connection
