2V0-21.23 Online Practice Questions and Answers
An administrator wants to ensure that when virtual machines (VMs) are powered on, Distributed Resource Scheduler (DRS) places them on the best-suited host. When the cluster becomes imbalanced, the administrator wants DRS to display recommendations for manual VM migration.
Which DRS automation level should the administrator select? (Choose the best answer.)
A. Manual
B. Partially automated
C. Fully automated
D. Disabled
An administrator is tasked with upgrading an existing vSphere environment to version 7.0. The current configuration is using an external Platform Services Controller. Which two statements are true regarding this upgrade? (Choose two.)
A. The external Platform Services Controller needs to be converged into an embedded vCenter Server Appliance.
B. The external Platform Services Controller needs to be decommissioned following the deployment of the new vCenter Server Appliance.
C. The external Platform Services Controller backup can be restored to a new embedded vCenter Server Appliance.
D. The external Platform Services Controller needs to be upgraded after the vCenter Server Appliance.
E. The external Platform Services Controller needs to be powered down while a new vCenter Server Appliance is deployed.
An administrator wants to leverage the processor-specific technology that uses a security extension for securing virtual machines (VMs). This will allow user-level code to define private regions of memory called enclaves that are protected from external access.
What does the administrator need to configure to enable VMs to use this technology? (Choose the best answer.)
A. Trusted Platform Module (TPM)
B. Virtual Intel Software Guard Extensions (vSGX)
C. Advanced Encryption Standard-New Instructions (AES-NI)
D. Transparent Page Sharing (TPS)
Refer to the exhibit.
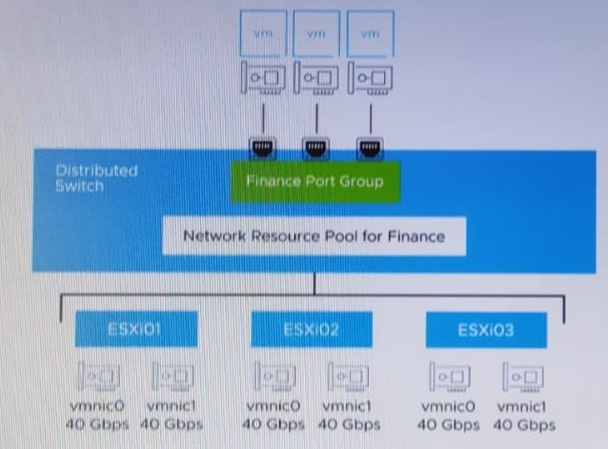
An administrator set up the following configuration:
The distributed switch has three ESXi hosts, and each host has two 40 Gbps NICs. The amount of bandwidth reserved for virtual machine (VM) traffic is 6 Gbps.
The administrator wants to guarantee that VMs in the Finance distributed port group can access 50 percent of the available reserved bandwidth for VM traffic. k
Given this scenario, what should the size (in Gbps) of the Finance network resource pool be?
A. 18
B. 80
C. 36
D. 120
Refer to the exhibit.

An administrator set up the following configuration:
The distributed switch has four ESXi hosts, and each host has two 10 Gbps NICs.
In the Network I/O Control configuration, the amount of bandwidth reserved for virtual machine (VM) traffic if 4 Gbps.
The administrator wants to guarantee that VMs in the Retail distributed port group can access 50 percent of the available reserved bandwidth for VM traffic.
Given this scenario, what should the size (in Gbps) of the Retail network resource pool be?
A. 40
B. 32
C. 8
D. 16
An administrator has a host profile named Standard-Config. The administrator wants to change the other host profiles to use only the storage configuration settings that are defined in the Standard-Config host profile.
What should the administrator do to make this change?
A. Export host customizations and import them to the other host profiles.
B. Copy the storage settings from Standard-Config to all other host profiles.
C. Duplicate the Standard-Config host profile and only modify the storage configuration settings.
D. Export the Standard-Config host profile and attach it to the other hosts.
An administrator creates a new corporate virtual machine (VM) template every month to include all of the latest patches. The administrator needs to ensure that the new VM template is synchronized from the primary data center site (London) to two secondary data center sites (Tokyo and New York). The administrator is aware that datastore space is limited within the secondary data center sites. The administrator needs to ensure that the VM template is available in the secondary sites the first time a new virtual machine is requested.
Which four steps should the administrator take to meet these requirements? (Choose four.)
A. Create a new published content library at the primary site.
B. Add the virtual machine template to the subscribed content library.
C. Create a new published content library in each secondary site.
D. Create a new subscribed content library in each secondary site.
E. Configure the subscribed content library to download content when needed.
F. Configure each subscribed content library to download content immediately.
G. Add the virtual machine template to the published content library.
The vCenter inventory contains a virtual machine (VM) template called Linux-01. The administrator wants to install a software patch into Linux-01 while allowing users to continue to access Linux-01 to deploy VMs. Which series of steps should the administrator take to accomplish this task?
A. 1. Verify that Linux-01 is in a content library
2.
Clone Linux-01
3.
Convert the clone to a VM
4.
Install the software patch.
B. 1. Convert Linux-01 to a VM 2 Install the software patch 3 Convert the VM back to a VM template 4 Add Linux-01 to the content library.
C. 1. Verify that Linux-01 is in a content library
2.
Checkout Linux-01
3.
Install the software patch
4.Check in Linux-01
D. 1. Clone Linux-01.
2.
Convert the clone to a VM
3.
Install the software patch.
4.
Convert the VM back to a template.
An administrator is asked to configure a security policy at the port group level of a standard switch.
The following requirements must be met:
The security policy must apply to all virtual machines on portgroup-1. All traffic must be forwarded, regardless of the destination.
A. Forged transmits set to reject
B. MAC address changes set to accept
C. Promiscuous mode set to reject
D. Promiscuous mode set to accept
An administrator Is looking to deploy a new VMware vCenter Instance. The current environment consists of 75 hosts and is expected to grow up to 100 hosts over the next three years. Which deployment size should the administrator select?
A. Medium
B. Tiny
C. Large
D. Small
An administrator wants to allow a DevOps engineer the ability to delete Tanzu Kubernetes Grid (TKG) cluster objects in a vSphere Namespace. Which role would provide the minimum required permissions to perform this operation?
A. Administrator
B. Can View
C. Owner
D. Can Edit
A combination of which two components of the software-defined data center (SDDC) are responsible for the initial abstraction of CPU, memory, disk, and network resources and their subsequent management? (Choose two.)
A. VMwere ESXi
B. VMware vCenter Cloud Gateway
C. VMware Ana Suite Lifecycle
D. VMware vCenter
E. VMware Ana Operations
A vSphere cluster has the following configuration:
Virtual machines (VMs) are running Production and Test workloads
vSphere Distributed Resource Scheduler (DRS) is enabled
There are no resource pools in the cluster
Performance monitoring data shows that the Production workload VMs are not receiving their fully allocated memory when the vSphere cluster is fully utilized.
A combination of which two steps could the administrator perform to ensure that the Production VMs are always guaranteed the full allocation of memory? (Choose two.)
A. Assign a custom memory share value to the resource pool containing the Production VMs.
B. Assign a memory reservation value to the resource pool containing the Production VMs.
C. Create a parent resource pool for the Production VMs.
D. Create a sibling resource pool for each of the Production and Test VMs.
E. Create a child resource pool for the Test VMs.
Exhibit switch
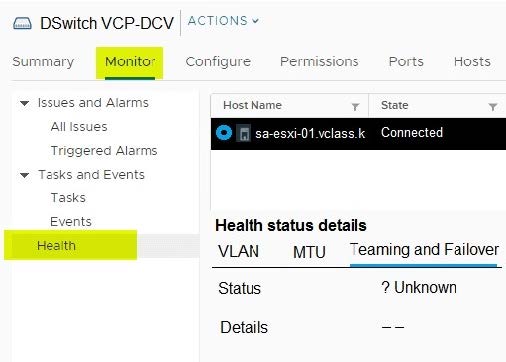
An administrator configures a distributed switch and adds the first VMware ESXi server to it.
The administrator also performs the following activities:
The administrator assigns two uplinks to the distributed switch.
The administrator enables uplink teaming.
When attempting to perform a health check of the teaming policy, the health status of the Teaming and Failover reports as ' Unknown?, as seen in the exhibit.
What can the administrator changes in the distributed switch for the health status to report correctly?
A. Add a minimum of three hosts with two uplinks each
B. Add a minimum of two hosts with two uplinks each
C. Add a minimum of three hosts with four uplinks each
D. Add a minimum of two hosts with one uplink each
If a distributed switch uses the "Route based on physical NIC load" load balancing algorithm, what does the mean send or receive utilization of an uplink need to exceed for the flow of traffic to move to the second uplink?
A. 75 percent of the capacity over a 30 second period
B. 60 percent of the capacity over a 30 second period
C. 60 percent of the capacity over a 40 second period
D. 75 percent of the capacity over a 40 second period
