210-255 Online Practice Questions and Answers
Which regular expression matches "color" and "colour"?
A. col[0-9]+our
B. colo?ur
C. colou?r
D. ]a-z]{7}
What information from HTTP logs can be used to find a threat actor?
A. referer
B. IP address
C. user-agent
D. URL
You have run a suspicious file in a sandbox analysis tool to see what the file does. The analysis report shows that outbound callouts were made post infection. Which two pieces of information from the analysis report are needed or required to investigate the callouts? (Choose two.)
A. file size
B. domain names
C. dropped files
D. signatures
E. host IP addresses
At which stage attacking the vulnerability belongs in Cyber kill chain?
A. Exploitation
B. Reconnaissance
C. Weaponization
D. Delivery
E. Installation
F. Command and control (C2)
G. Actions on objectives
Which two potions about deterministic and probabilistic analysis are true? (Choose two.)
A. probabilistic analysis uses data known beforehand and deterministic analysis is based off assumptions.
B. Deterministic analysis uses data known beforehand and probabilistic analysis based off of assumptions.
C. Deterministic analysis is based off of assumptions
D. Probabilistic analysis result in a result that is definitive.
E. probabilistic analysis results in a result that is not definitive.
Refer to exhibit. Which option is the logical source device for these events?
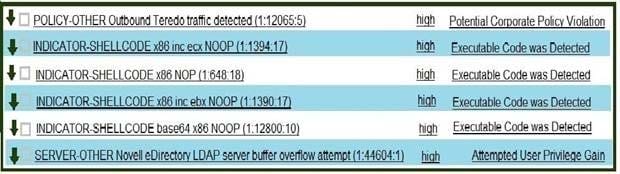
A. web server
B. NetFlow collector
C. proxy server
D. IDS/IPS
Employees are allowed access to internal websites. An employee connects to an internal website and IDS reports it as malicious behavior. What is this example of?
A. true positive
B. false negative
C. false positive
D. true negative
What define the roadmap for implementing the incident response plan?
A. Incident response plan
B. Incident response policy
C. Incident response procedures
Which example of a precursor is true?
A. A notification that a host is infected with malware.
B. An admin finds their password has been changed.
C. A log indicating a port scan was run against a host
D. A device configuration changed from the baseline without an audit log entry.
Which two statements correctly describe the victim demographics section of the VERIS schema? (Choose two.)
A. The victim demographics section describes but does not identify the organization that is affected by the incident.
B. The victim demographics section compares different types of organizations or departments within a single organization.
C. The victim demographics section captures general information about the incident.
D. The victim demographics section uses geolocation data to identify the organization name of the victim and the threat actor.
Which netstat command show ports? (Choose two)
A. netstat a
B. netstat -l
C. netstat -v
D. netstat -g
Which incident handling phase contains evidence gathering and handling?
A. containment, eradication, and recovery
B. identification
C. post incident
D. preparation
Which filter shows only SMTP and ICMP traffic on Wireshark?
A. tcp.eq 25 or icmp
B. tcp.port eq 25 or icmp
C. port eq 25 and icmp
D. tcp.port eq 25 also icmp

Refer to the exhibit. Which event is represented by this configuration?
A. The ext3-test.img is being converted from read-only to read-write for analysis.
B. A drive is being mounted using ext3-test.img file as a source.
C. A /mnt/test directory is being created in the ext3-test.img file.
D. The ext3-test.img file was found on the ext4 filesystem in the /mnt/test directory.
Which command filters a port?
A. tcp.port equals 25
B. tcp.port is 25
C. tcp.port != 25
D. !tcp.port==25
