200-901 Online Practice Questions and Answers
What is the function of an IP address in networking?
A. represents a network connection on specific devices
B. specifies the type of traffic that is allowed to roam on a network
C. specifies resource's location and the mechanism to retrieve it
D. represents the unique ID that is assigned to one host on a network
A local Docker alpine image has been created with an image ID of a391665405fe and tagged as "latest". Which command creates a running container based on the tagged image, with the container port 8080 bound to port 80 on the host?
A. docker build -p 8080:80 alpine:latest
B. docker exec -p 8080:80 alpine:latest
C. docker start -p 8080:80 alpine:latest
D. docker run -p 8080:80 alpine:latest
A company is looking for a cloud deployment which will only use the on-premise infrastructure, is user self- service, and is easy to scale. Which cloud solution should be selected for these requirements?
A. multi
B. private
C. hybrid
D. public
Refer to the exhibit.
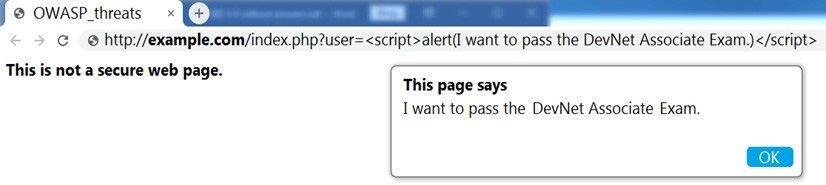
Which OWASP threat does this example demonstrate?
A. broken access control
B. cross-site scripting
C. SQL injection
D. man-in-the-middle
Refer to the exhibit.
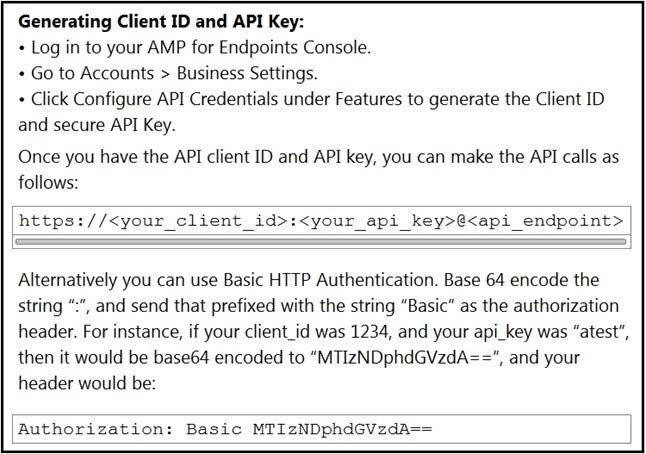
The documentation outlines how to use credentials for the AMP API. Which script successfully performs an API call using basic authentication?
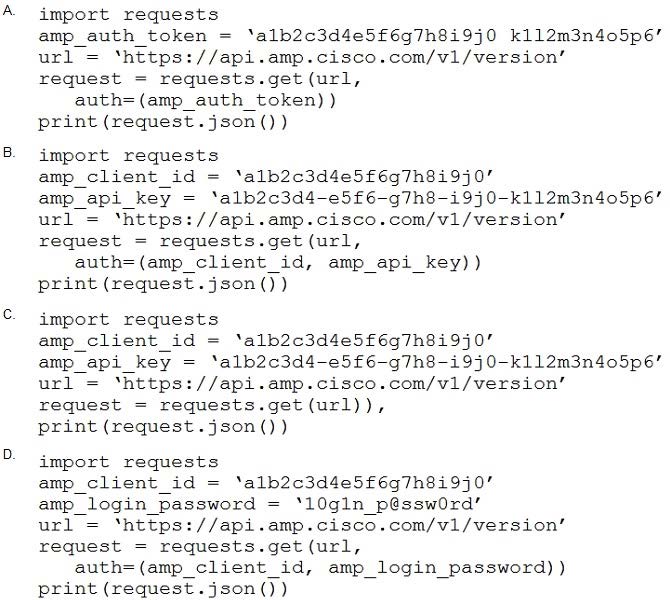
A. Option A
B. Option B
C. Option C
D. Option D
Which Cisco platform provides organization-wide automation, security, policy enforcement, any agility across wired and wireless networks?
A. Cisco ACI
B. Cisco DNA Center
C. Cisco Umbrella
D. Cisco SD-WAN
Refer to the exhibit.
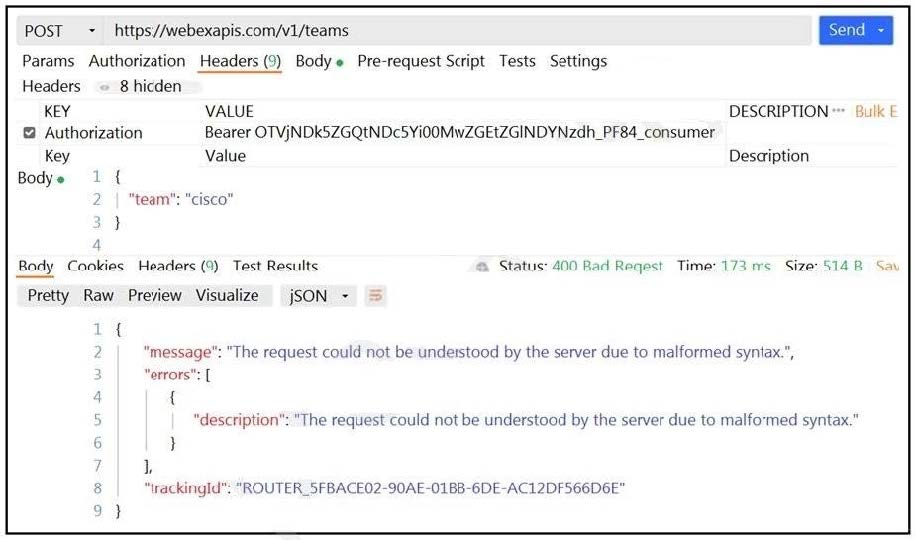
A developer wants to create a room named cisco through Webex API. The developer prepares the request by putting an API token inside the authorization header; however, the given HTTP call returns error code 400. How must the call parameters be changed to ensure a valid response?
A. Replace the team body parameter with the name body parameter.
B. Replace cisco with a valid name for a team.
C. Change the token in the header with the authorization token.
D. Change the HTTP method of the call to PUT.
Which type of HTTP method is used by the Meraki and Webex Teams APIs to send webhook notifications?
A. HTTP POST
B. HTTP GET
C. HTTP HEAD
D. HTTP PUT
What are two considerations when selecting the "best route" for a network device to reach its destination? (Choose two.)
A. MAC address
B. IP address
C. metrics
D. administrative distance
E. subnet mask
Refer to the exhibit.
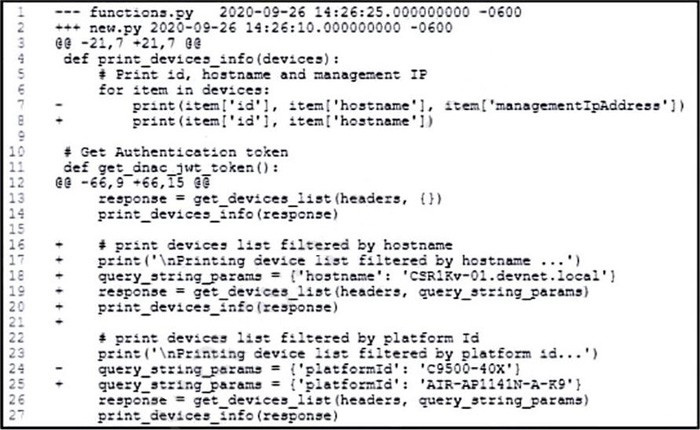
An engineer is comparing two files by using the unified diff format. Which cade snippet belongs to the new.py file?

A. Option A
B. Option B
C. Option C
D. Option D
A developer is working on a new feature in a branch named 'newfeat123456789' and the current working primary branch is named 'prim987654321'. The developer requires a merge commit during a fast forward merge for record-keeping purposes. Which Git command must be used?
A. git merge --no-ff newfeat123456789
B. git commit --no-ff newfeat123456789
C. git add --commit-ff newfeat123456789
D. git reset --commit-ff newfeat123456789
What is the benefit of organizing data into functions?
A. supports using same variable in different modules
B. supports altering the state of an object
C. organize code in a reusable way
D. stores data values of different types
A company plans to develop an application by using Cisco APIs. The application must use code repositories approved by Cisco. The development team wants to make use of community-supported, open-source code. Which resource should be used?
A. Cisco DevNet Code Exchange
B. Cisco TAC
C. Cisco DevNet Sandbox
D. Cisco DevNet Learning Labs
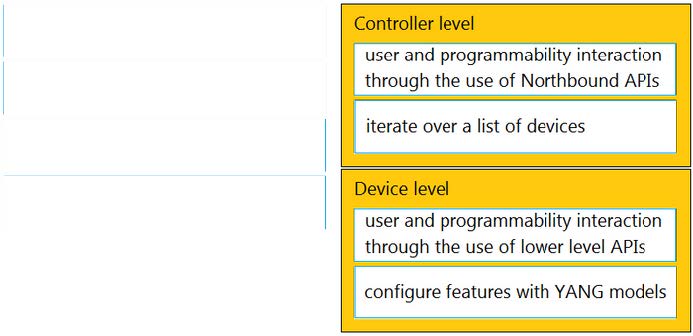
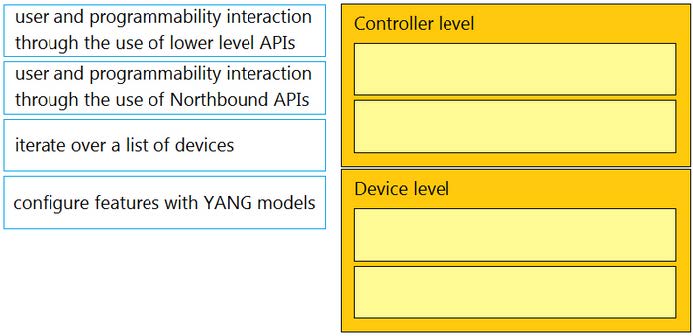
DRAG DROP
Drag and drop the types of management from the left onto the levels at which they are performed on the right.
Select and Place:
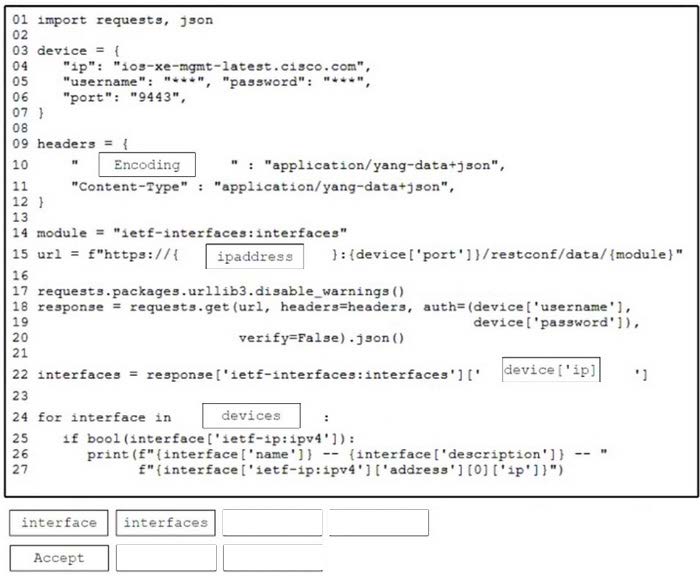
DRAG DROP
Refer to the exhibit.
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that allows an engineer to retrieve interface data. Not all options are used.
Select and Place: