1Y0-440 Online Practice Questions and Answers
A Citrix Architect has deployed NetScaler Management and Analytics System (NMAS) to monitor a high availability pair of NetScaler VPX devices.
The architect needs to deploy automated configuration backup to meet the following requirements:
1.
The configuration backup file must be protected using a password.
2.
The configuration backup must be performed each day at 8:00 AM GMT.
3.
The configuration backup must also be performed if any changes are made in the ns.conf file.
4.
Once the transfer is successful, auto-delete the configuration file from the NMAS.
Which SNMP trap will trigger the configuration file backup?
A. netScalerConfigSave
B. sysTotSaveConfigs
C. netScalerConfigChange
D. sysconfigSave
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites.
The requirements captured during the design discussion held for a NetScaler design project are as follows:
1.
Two (2) pairs of NetScaler MPX appliances deployed in the DMZ and internal network.
2.
High Availability will be accessible for each NetScaler MPX
3.
The external NetScaler MPX appliance will be deployed in multi-arm mode.
4.
The internal NetScaler MPX will be deployed in single-arm mode wherein it will be connected to Cisco ACI Fabric.
5.
All three (3) Workspacelab sites: Dc, NDR and DR, will have similar NetScaler configurations and design.
How many NetScaler MPX appliances should the architect deploy at each site to meet the design requirements above?
A. 4
B. 12
C. 6
D. 2
Scenario: A Citrix Architect needs to assess a NetScaler Gateway deployment that was recently completed by a customer and is currently in pre-production testing. The NetScaler Gateway needs to use ICA proxy to provide access to a XenApp and XenDesktop environment. During the assessment, the customer informs the architect that users are NOT able to launch published resources using the Gateway virtual server.
Click the Exhibit button to view the troubleshooting details collected by the customer.

What is the cause of this issue?
A. The required ports have NOT been opened on the firewall between the NetScaler gateway and the Virtual Delivery Agent (VDA) machines.
B. The StoreFront URL configured in the NetScaler gateway session profile is incorrect.
C. The Citrix License Server is NOT reachable.
D. The Secure Ticket Authority (STA) servers are load balanced on the NetScaler.
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0.
53.13 nc. These are placed behind a Cisco ASA 5505 Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer's security team:
The NetScaler device:
1.
Should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The NetScaler device should be able to stop the HTTP, TCP, and DNS based requests.
2.
Needs to protect backend servers from overloading.
3.
Needs to queue all the incoming requests on the virtual server level instead of the service level.
4.
Should provide access to resources on the basis of priority.
5.
Should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing
proxies.
6.
Should provide flexibility to enforce the desired level of security check inspections for the requests originating from a specific geolocation database.
7.
Should block the traffic based on a pre-determined header length, URL length, and cookie length. The device should ensure that characters such as a single straight quote (*); backslash(\), and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which two security features should the architect configure to meet these requirements? (Choose two.)
A. Pattern sets
B. Rate limiting
C. HTTP DDOS
D. Data sets
E. APPQOE
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion. They have captured the following requirements for NetScaler design project:
1.
The authentication must be deployed for the users from the workspacelab.com and vendorlab.com domains.
2.
The workspacelab users connecting from the internal (workspacelab) network should be authenticated using LDAP.
3.
The workspacelab users connecting from the external network should be authenticated using LDAP and RADIUS.
4.
The vendorlab users should be authenticated using Active Directory Federation Service.
5.
The user credentials must NOT be shared between workspacelab and vendorlab.
6.
Single Sign-on must be performed between StoreFront and NetScaler Gateway.
7.
A domain drop down list must be provided if the used connects to the NetScaler gateway virtual server externally.
Which method must the architect utilize for user management between the two domains?
A. Create shadow accounts for the users of the Workspacelab domain in the Vendorlab domain.
B. Create a global catalog containing the objects of Vendorlab and Workspacelab domains.
C. Create shadow accounts for the Vendorlab domain in the Workspacelab domain.
D. Create a two-way trust between the Vendorlab and Workspacelab domains.
Scenario: A Citrix Architect needs to design a new multi-datacenter NetScaler deployment. The customer wants NetScaler to provide access to various backend resources by using Global Server Load Balancing
(GSLB) in an Active-Active deployment.
Click the Exhibit button to view additional requirements identified by the architect.

Which GSLB algorithm or method should the architect use for the deployment, based on the stated requirements?
A. Dynamic round trip time (RTT)
B. Least response time
C. Static proximity
D. least connection
E. Least packets
F. Source IP hash
Which three methods can a Citrix Architect use to assess the capabilities of a network infrastructure? (Choose three.)
A. Review existing monitoring solutions for periods of latency, lost packets, and insufficient bandwidth.
B. Map the location of the users against the existing network topology.
C. Alter firewall rules of existing network to fit into the new NetScaler Deployment.
D. Examine the topology for single points of failure and potential bottlenecks.
E. Ensure that users and computers are in the correct organizational units (OUs).
Scenario: A Citrix Architect and a team of Workspacelab members have met for a design discussion about the NetScaler Design Project. They captured the following requirements:
1.
Two pairs of NetScaler MPX appliances will be deployed in the DMZ network and the internal network.
2.
High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
3.
Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
4.
The NetScaler Gateway virtual server is integrated with XenApp/XenDesktop environment.
5.
Load balancing must be deployed for the users from the workspacelab.com and vendorlab.com
domains.
6.
The logon page must show the workspacelab logo.
7.
Certificate verification must be performed to identify and extract the username.
8.
The client certificate must have UserPrincipalName as a subject.
9.
All the managed workstations for the workspace users must have a client identifications certificate
installed on it.
10.The workspacelab users connecting from a managed workstation with a client certificate on it should be
authenticated using LDAP. 11.The workspacelab users connecting from a workstation without a client
certificate should be authenticated using LDAP and RADIUS.
12.The vendorlab users should be authenticated using Active Directory Federation Service.
13.The user credentials must NOT be shared between workspacelab and vendorlab.
14.Single Sign-on must be performed between StoreFront and NetScaler Gateway.
15.A domain drop down list must be provided if the user connects to the NetScaler Gateway virtual server
externally.
16.The domain of the user connecting externally must be identified using the domain selected from the
domain drop down list.
On performing the deployment, the architect observes that users are always prompted with two-factor authentication when trying to assess externally from an unmanaged workstation.
Click the exhibit button to view the configuration.
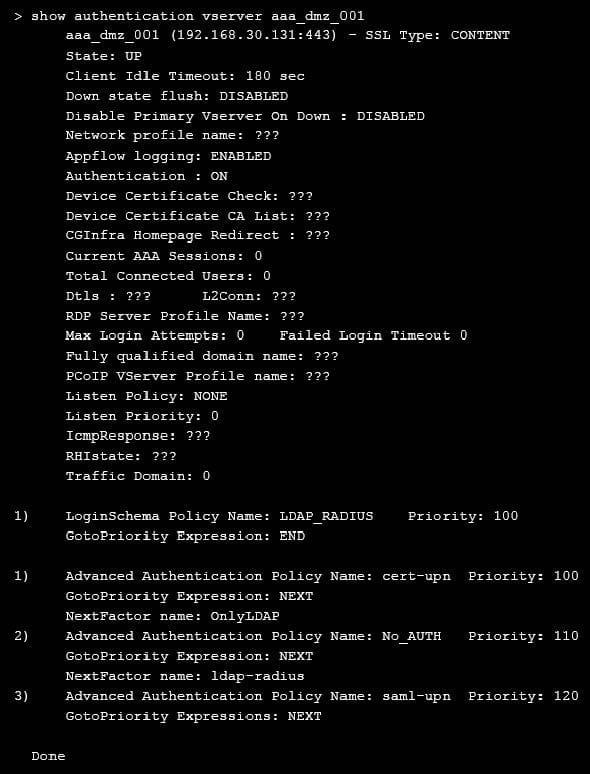
What should the architect do to correct this configuration?
A. Unbind LoginSchema Policy LDAP_RADIUS from the virtual server.
B. Bind the Portal theme as Domaindropdown.
C. Bind the LoginSchema Policy Domaindropdown to priority 90.
D. Bind the Default LoginSchema Policy as Domaindropdown.
Which NetScaler Management and Analytics System (NMAS) utility can a Citrix Architect utilize to verify the configuration template created by the NMAS StyleBook, before actually executing it on the NetScaler?
A. Dry Run
B. configpack
C. NITRO API
D. configcheck
Scenario: A Citrix Architect needs to design a new NetScaler Gateway deployment for a customer. During the design discussions, the architect learns that the customer would like to allow external RDP connections to internal Windows machines but does NOT want client drive redirection enabled on these connections.
Where should the architect enable the options to allow the customer to complete their requirement?
A. NetScaler Gateway global settings
B. RDP bookmark
C. Session policy
D. RDP server profile
E. Session profile
F. RDP client profile
Under which two circumstances will a service be taken out of the slow start phase with automated slow start? (Choose two.)
A. The service does NOT receive traffic for three successive increment intervals.
B. The server request rate parameters are set above 25 requests per second.
C. The actual request rate is slower than the new service request rate.
D. The percentage of traffic that the new service must receive is greater or equal to 50.
E. The request rate has been incremented 100 times.
Scenario: A Citrix Architect has deployed an authentication setup with a ShareFile load-balancing virtual
server. The NetScaler is configured as the Service Provider and Portalguard server is utilized as the SAML
Identity Provider. While performing the functional testing, the architect finds that after the users enter their
credentials on the logon page provided by Portalguard, they get redirected back to the Netscaler Gateway
page at uri /cgi/samlauth/ and receive the following error.
"SAML Assertion verification failed; Please contact your administrator."
The events in the /var/log/ns.log at the time of this issue are as follows:
Feb 23 20:35:21
Message 3225369 0 : "SAML : ParseAssertion:
parsed attribute NameID, value is nameid"
Feb 23 20:35:21
Message 3225370 0 : "SAML verify digest:
algorithms differ, expected SHA1 found SHA256"
Feb 23 20:35:44
Message 3225373 0 : "SAML : ParseAssertion:
parsed attribute NameID, value is named
Feb 23 20:35:44
Message 3225374 0 : "SAML verify digest:
algorithms differ, expected SHA1 found SHA256"
Feb 23 20:37:55
Message 3225378 0 : "SAML : ParseAssertion:
parsed attribute NameID, value is nameid"
Feb 23 20:37:55
Message 3225379 0 : "SAML verify digest:
algorithms differ, expected SHA1 found SHA256"
What should the architect change in the SAML action to resolve this issue?
A. Signature Algorithm to SHA 256
B. The Digest Method to SHA 256
C. The Digest Method to SHA 1
D. Signature Algorithm to SHA 1
Scenario: A Citrix Architect needs to assess an existing NetScaler configuration. The customer recently found that certain user groups were receiving access to an internal web server with an authorization configuration that does NOT align with the designed security requirements.
Click the Exhibit button view the configured authorization settings for the web server.
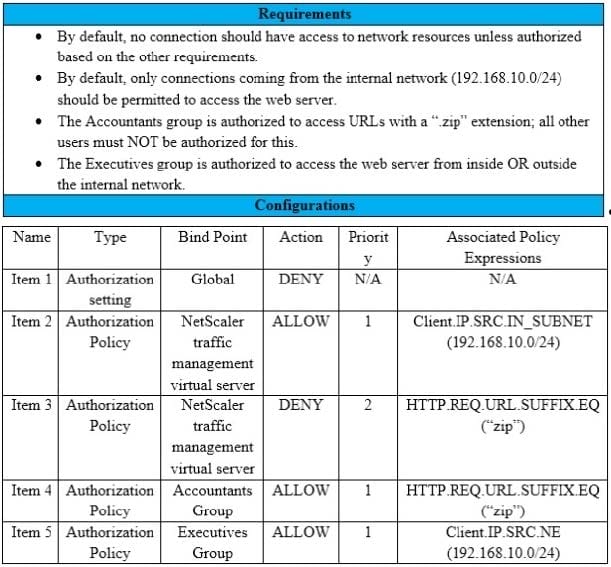
Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?
A. Item 1
B. Item 3
C. Item 4
D. Item 5
E. Item 2
Which step does a Citrix Architect need to ensure during the Define phase when following the Citrix Methodology?
A. Testing steps were integrated.
B. The project manager agrees with road map timelines.
C. A phased roll out was completed.
D. Existing networking infrastructure is ready.
E. The redundancy deployment decision was made.
Scenario: A Citrix Architect has sent the following request to the NetScaler: Which response would indicate the successful execution of the NITRO command?
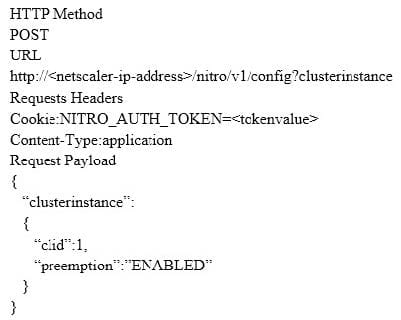
A. 302
B. 201
C. 202
D. 200
