1Z0-052 Online Practice Questions and Answers
Which two are true about consistent database backups? (Choose two.)
A. They can only be taken if the database is in ARCHIVELOG mode.
B. They can only be taken by using RMAN command.
C. They can only be taken when a RECOVERY CATALOG is used.
D. They can only be taken by using RMAIN when the database is in MOUNT state.
E. They can only be taken if a NORMAL, TRANSACTIONAL, OR IMMEDIATE shutdown has been performed and the backup is taken before the database is reopened.
Which two are true about AWR snapshots? (Choose two.)
A. They are always created automatically.
B. They can be modified by using DMLs.
C. They are not generated if STATISTICS_LEVEL is set to TYPICAL.
D. They are stored in the SYSAUX tablespace.
E. They can be retained forever.
You have recently collected statistics on certain objects of a schema in your database. But you observe suboptimal execution plans for the queries on these objects after two days of statistics collection. The optimizer statistics retention period is set to its default value.
Which action would help to use the previous set of statistics on the objects?
A. Restore statistics from statistics history.
B. Reduce the optimizer statistics retention period by 2 days.
C. Set the OPTIMIZER_PENDING_STATISTICS parameter to TRUE.
D. Reduce the Automatic Workload Repository (AWR) retention period by 2 days.
Examine the following steps performed on a database instance:
1.
The DBA grants the CREATE TABLE system privilege to the SKD user with ADMIN OPTION
2.
The SKD user creates a table
3.
The SKD user grants the CREATE TABLE system privilege to the HR user
4.
The HR user creates a table
5.
The DBA revokes the CREATE TABLE system privilege from SKD Which statement is true after step 5 is performed?
A. The table created by SKD is not accessible and SKD cannot create new tables
B. The tables created by SKD and HR remain, but both cannot create new tables
C. The table created by HR remains and HR still has the CREATE TABLE system privilege
D. The table created by HR remains and HR can grant the CREATE TABLE system privilege to other users
In which situation may the UNDO_RETENTION parameter be ignored, even if it is set to a value?
A. When the data file of the undo tablespace is autoextensible
B. When there are more than one undo tablespace available in the database
C. When the undo tablespace is of a fixed size and retention guarantee is not enabled
D. When the undo tablespace is autoextensible and retention guarantee is not enabled
Which two operations can be performed on an external table? (Choose two.)
A. Create a view on the table
B. Create an index on the table
C. Create a synonym on the table
D. Add a virtual column to the table
E. Update the table using the UPDATE statement
F. Delete rows in the table using the DELETE command
You want to create a role to meet these requirements:
1.
The role is to be protected from unauthorized usage.
2.
The password of the role is not to be embedded in the application source code or stored in a table. Which method would you use to restrict enabling of such roles?
A. Create the role with external authentication.
B. Create the role as a secure application role.
C. Create the role as a password-protected role.
D. Create a role and use Fine-Grained Access Control (FGAC) to secure the role.
View the Exhibit to examine the output for the CROSSCHECK BACKUP command.
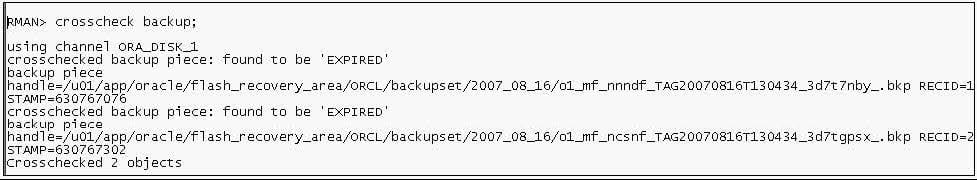
Which statement is true about the output of the command?
A. The backup piece is expired as the new backup is available
B. The backup piece is expired because the operating-system file was not found
C. The backup piece is expired because the retention period for the backup has expired
D. The backup piece is expired because the backup set to which it belongs is not complete
Which is the correct description of a pinned buffer in the database buffer cache?
A. The buffer is currently being accessed
B. The buffer is empty and has not been used
C. The contents of the buffer have changed and must be flushed to the disk by the DBWn process
D. The buffer is a candidate for immediate aging out and its contents are synchronized with the block contents on the disk
In which situation would you use static database registration for a listener?
A. When multiple databases are to be registered with the listener
B. When DBAs need to connect remotely to start up the database instance
C. When users need to connect the database instance using the host naming method
D. When the database instance that is to be registered with the listener is configured in shared server mode
You are working on a new Oracle Database 11g server, where only the software is installed and no database is created. You plan to create a database on this server using the Database Configuration Assistant (DBCA).
Some of the requirements set for your database creation task are:
1.
Configure the database to operate in shared server mode.
2.
Disable automatic maintenance tasks such as optimizer statistics collection.
3.
Configure a naming method to help the remote user connect to the database instance.
4.
Use Automatic Storage Management (ASM) for storing the database files.
5.
Configure daily database backup to flash recovery area.
6.
Configure Enterprise Manager Database Control to manage the database. Which of these requirements can be met while creating the database?
A. 4 and 6
B. 2, 3, 4, and 6
C. 1, 2, 4, 5, and 6
D. 1, 2, 3, 4, 5, and 6
Some non-DBA users in your database have been granted ANY TABLE system privileges and they are able to access data dictionary base tables. You decide to restrict their access to data dictionary objects. Which method would you adopt to achieve this objective?
A. Revoke the RESOURCE role from the users.
B. Set the value of the OS_ROLES parameter to TRUE.
C. Use Database Resource Manager to restrict user access to objects.
D. Grant ANY TABLE system privileges again without ADMIN OPTION.
E. Set the value of the O7_DICTIONARY_ACCESSIBILITY parameter to FALSE.
Your database is functional with a peak load for the last one hour. You want to preserve the performance statistics collected during this period to be used for comparison when you analyze the performance of the database in the future.
What action would you take to achieve this task?
A. Insert finding directives for ADDM tasks in the future.
B. Create a baseline on a pair of snapshots spanning the peak-load period.
C. Decrease the snapshot interval in the AWR to collect more snapshots during the peakload period.
D. Set the snapshot retention period in the Automatic Workload Repository (AWR) to zero to avoid automatic purging of snapshots.
Your database is in shutdown state. What will happend if you issue next command: SQL> startup
A. instance will started
B. instance started and DB is mounted
C. instance started, DB opened and finally mounted
D. instance started, DB mounted and finally opened
The user SCOTT owns the CUST table that is placed in the SALES tablespace. The user SCOTT opens a
session and executes commands as follows:
SQL> INSERT INTO cust VALUES(101, 'JACK');
1 row created.
SQL> INSERT INTO cust VALUES(102, 'SMITH');
1 row created.
As a DBA, you execute the following command from another session:
ALTER TABLESPACE sales READ ONLY;
Which statement is true regarding the effect of this command on the transaction in Scott's session?
A. The command fails as a transaction is still pending.
B. The transaction in Scott's session is rolled back and the tablespace becomes readonly.
C. The command waits and the user SCOTT can execute data manipulation language (DML) statements only as part of the current transaction.
D. The command hangs until all transactions on the objects in the tablespace commit or rollback, and then the tablespace is placed in readonly mode.
