1D0-541 Online Practice Questions and Answers
What is the highest normal form of the relation(s) shown in the exhibit?
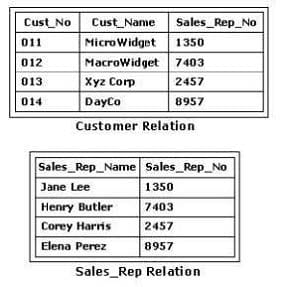
A. No normal form
B. Second normal form
C. First normal form
D. Third normal form
Which security technique limits access by unauthorized users to parts of an enterprise database?
A. Views
B. Concurrency
C. Locking
D. Integrity controls
Which database security technique prevents invalid data from being entered into the database?
A. File locking
B. User authorization
C. Parity checks
D. Integrity controls
What is a virtual table?
A. A virtual table is a relation created as the result of data manipulation, and is not a permanent part of the database.
B. A virtual table is a relation stored in the databases memory; it is used when multiple users access the same relation in a database.
C. A virtual table is a relation created from a defined base table; it contains metadata about the base relation.
D. A virtual table is a relation that consists of primary and foreign keys for a particular set of relations in a database.
What is a data dictionary?
A. A system catalog containing user data
B. An area of the database that is directly accessible by the user
C. Data that is stored in tables and is only accessible by the DBMS
D. Metadata that is stored in tables and is only accessible by the DBMS
Consider the entity-relation (ER) diagram shown in the exhibit. When the logical database design phase is completed, which of the following is a valid DBDL description of the base relations for the ER diagram?
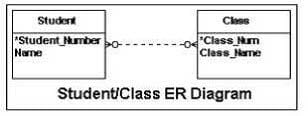
A. STUDENT( Student_Number: integer NOT NULL Name: variable length character string length 20 NOT NULL) Primary Key Student_Number CLASS( Class_Num: integer NOT NULL Class_Name: integer NOT NULL) Primary Key Class_Num
B. STUDENT( Student_Number: integer NOT NULL Name: variable length character string length 20 NOT NULL) Primary Key Student_Number CLASS( Class_Num: integer NOT NULL Class_Name: integer NOT NULL) Primary Key Class_Num Foreign Key Class_Num References STUDENT
C. STUDENT( Student_Number: integer NOT NULL Name: variable length character string length 20 NOT NULL) Primary Key Student_Number STU_CLASS( Student_Number: integer NOT NULL Class_Num: integer NOT NULL) Primary Key Student_Number CLASS( Class_Num: integer NOT NULL Class_Name: integer NOT NULL) Primary Key Class_Num
D. STUDENT( Student_Number: integer NOT NULL Name: variable length character string length 20 NOT NULL) Primary Key Student_Number STU_CLASS( Student_Number: integer NOT NULL Class_Num: integer NOT NULL) Primary Key Student_Number CLASS( Class_Num: integer NOT NULL Class_Name: integer NOT NULL) Primary Key Class_Num
Which subset of Structured Query Language (SQL) is used to create and name database entities?
A. Data Control Language
B. Database Entity Language
C. Data Definition Language
D. Data Manipulation Language
Which mechanism provides database users with controlled access to the database through the use of virtual tables?
A. View
B. Data dictionary
C. Database control language
D. Database management system
The database manager wants to give Rubio and Doe the ability to modify the Project Relation shown in the exhibit. A temporary employee named Temp needs to access the data in the database to generate reports. Which group of SQL statements will perform this task?
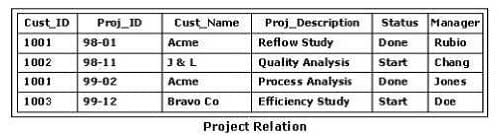
A. GRANT UPDATE ON Project TO Rubio, Doe; GRANT SELECT ON Project TO Temp;
B. GRANT ALL PRIVILEGES ON Project TO Rubio, Doe; GRANT UPDATE ON Project TO Temp;
C. GRANT SELECT ON Project WHERE Manager = 'Rubio'; GRANT SELECT ON Project WHERE Manager = 'Doe';
D. GRANT UPDATE ON Project WHERE Manager = 'Rubio'; GRANT UPDATE ON Project WHERE Manager = 'Doe'; GRANT SELECT ON Project TO Temp;
Consider the Recreation relation in the exhibit. A data operation that changes one of the tuples for Student_ID 1003 must be performed. It is necessary to change one of the activities from swimming to tennis. The Student_ID and Activity attributes make up the primary key for the Recreation relation. All related information must be altered, as well. Which SQL statement or statements would best accomplish this?
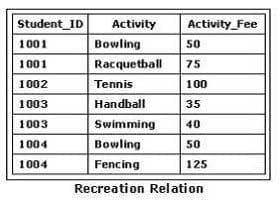
A. UPDATE Recreation SET Activity, Activity_Fee ('Tennis', 100) WHERE Student_ID = 1003;
B. UPDATE TABLE Recreation SET ACTIVITY = 'Tennis', Activity_Fee = 100 WHERE Student_ID = 1003 AND Activity = Swimming;
C. UPDATE Recreation SET Activity = 'Tennis', Activity_Fee = 100 WHERE Student_ID = 1003 AND Activity = 'Swimming';
D. DELETE Activity FROM Recreation WHERE Student_ID = 1003; INSERT INTO Recreation VALUES (1003, 'Tennis', 100);
Consider the following SQL statement and the Orders relation shown in the exhibit:
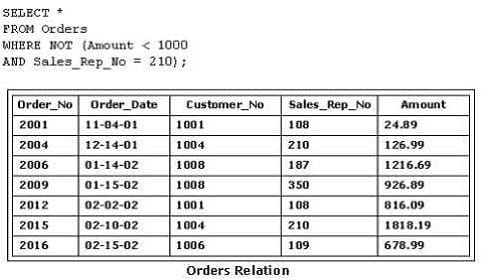
What is the output of this SQL statement?
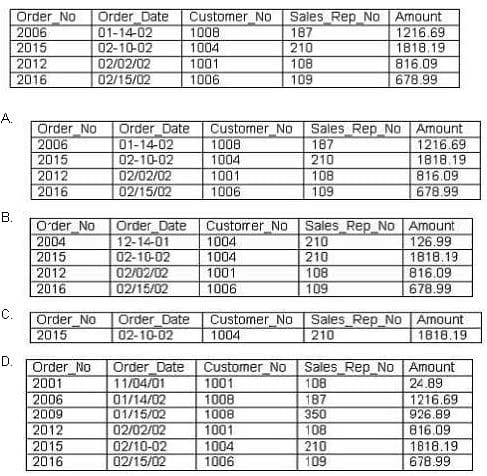
A. B. C. D.
Which process is used to prevent the current database operation from reading or writing a data item while that data item is being accessed by another operation?
A. Lock
B. Deadlock
C. Timestamp
D. Batch
Consider the following SQL statement and the Orders relation shown in the exhibit:
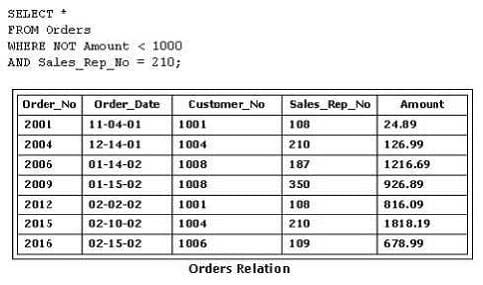
What is the output of this SQL statement?
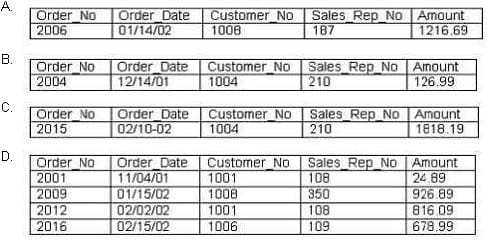
A. B. C. D.
Consider the following relation definitions: STUDENT( Student_Number: integer NOT NULL Name: variable length character string length 20 ) Primary Key Student_Number HOUSING( Housing_ID: integer NOT NULL Student_Number: integer NOT NULL Building: variable length character string length 25 ) Primary Key Housing_ID Foreign Key Student_Number References STUDENT(Student_Number) ON DELETE NO ACTION ON UPDATE CASCADE
What are the referential constraints for the relations defined in these relation definitions?
A. There is no relationship between changes in STUDENT(Student_Number) and HOUSING (Student_Number).
B. When STUDENT(Student_Number) is changed or deleted, this modification or deletion will automatically be reflected in HOUSING(Student_Number).
C. Modifications to HOUSING(Student_Number) are automatically reflected in changes to STUDENT (Student_Number), but deletions are not permitted.
D. Modifications to STUDENT(Student_Number) are automatically reflected in changes to HOUSING (Student_Number). For a deletion to occur from STUDENT(Student_Number), it must first occur in HOUSING(Student_Number).
A large enterprise uses a two-tier database architecture and runs complex database processing on the client. Which term best describes the client in this system?
A. Fat client
B. Thin client
C. Terminal client
D. Enterprise client
