156-727.77 Online Practice Questions and Answers
Which of these statements describes the Check Point ThreatCloud?
A. A worldwide collaborative security network
B. Prevents vulnerability exploits
C. Controls access to web sites based on category
D. Blocks or limits usage of web applications
Which software blades are characteristic to a Threat Prevention Appliance?
A. Anti-Virus, Anti-Bot, IPS, Identity Awareness
B. Anti-Virus, Anti-Bot, IPS, URL Filtering, Identity Awareness
C. Anti-Virus, Anti-Bot, IPS, Application Control, URL Filtering, Identity Awareness
D. Anti-Virus, Anti-Bot, IPS, URL Filtering, Identity Awareness, SmartEvent
Can the Anti-Bot software blade be enabled on a Secure Web Gateway as well?
A. Yes, this is an optional blade for the Secure Web Gateway.
B. No, Anti-Bot needs to be part of the Threat Prevention Appliance.
C. Yes, it can be enabled if IPS is enabled as well.
D. Yes, Anti-Bot is always enabled together with Identity Awareness.
Which of the following is information uploaded to ThreatCloud?
A. Compromised Machine IP Addresses
B. Malware Site IP Addresses
C. Anticipated Attack Methods
D. Sensitive Corporate Data
What is the name of the Check Point cloud-driven Knowledgebase?
A. ThreatSpect
B. ThreatCloud
C. ThreatWiki
D. ThreatEmulator
Which of the following is a searchable database of all known threats detected by sensors around the world?
A. ThreatCloud
B. ThreatWiki
C. ThreatSpect
D. SmartLog
What advantage does the Recommended_Profile provide over the Default_Protection profile?
A. Reduced server load
B. Accelerated throughput
C. Advanced reporting options
D. Higher security posture
Looking at these logs, what happened at 10:55?
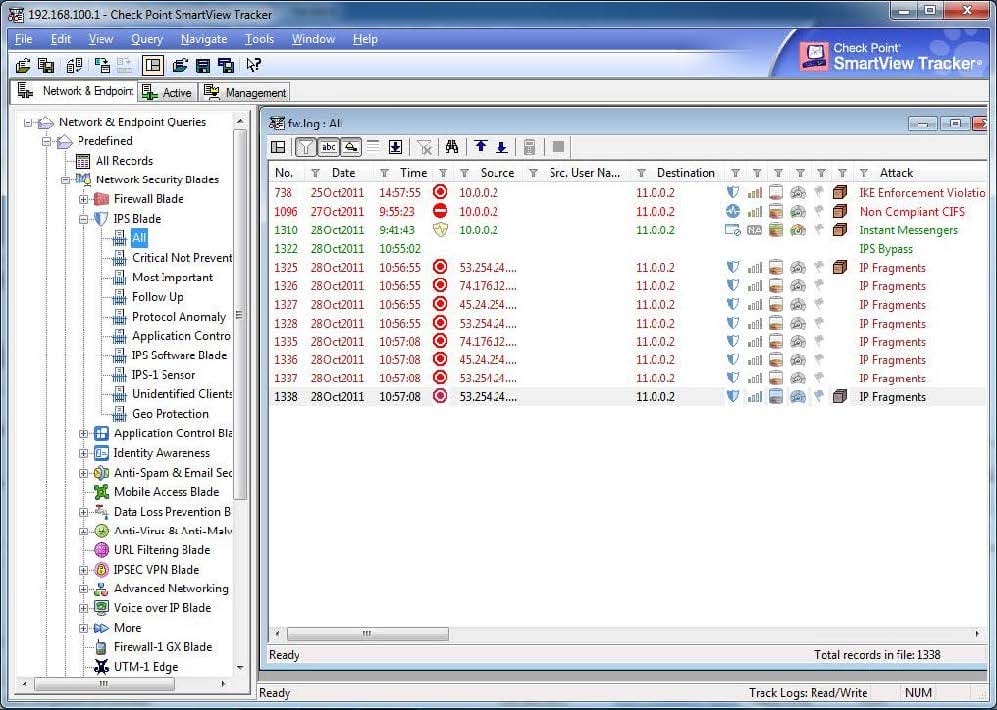
A. An IPS rule was installed, causing IPS to temporarily stop working
B. The Gateway was rebooted, causing IPS to temporarily stop working
C. A new IPS policy was installed, causing IPS to temporarily stop working
D. IPD Inspections were temporarily suspended, due to high load on the gateway
_______________ enforces or monitors traffic, based on the source or destination IP address of the country.
A. IPS Recommended_Protections Profile
B. Geo-protection
C. Secure Web Gateway
D. ThreatCloud
This graphic shows traffic being blocked from certain countries.
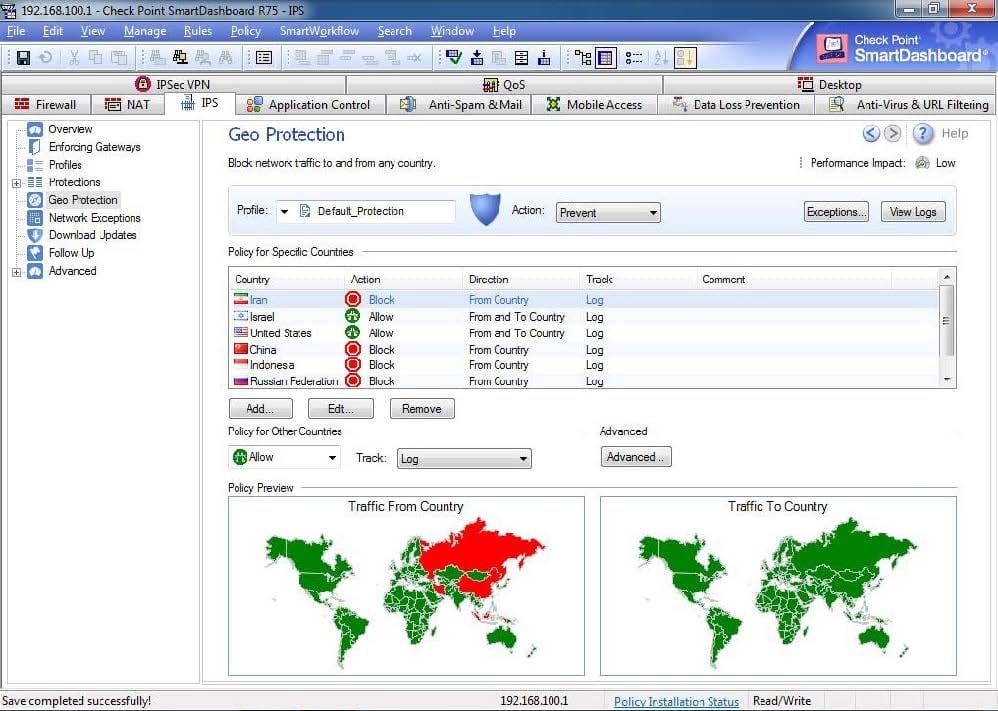
What is the deciding factor for this?
A. The traffic from selected countries is being blocked because of an IPS traffic-type rule in the rulebase
B. The traffic from selected countries is being blocked because it is overloading the Gateway
C. The traffic from selected countries is being blocked due to the GeoProtection ruleset
D. The traffic from selected countries is being blocked due to IPS-detected specific attacks originating there
Damage from a bot attack can take place after the bot compromises a machine. Which of the following represents the order by which this process takes place? The bot:
A. infects a machine, communicates with its command and control handlers, and penetrates the organization.
B. penetrates the organization, infects a machine, and communicates with its command and control handlers.
C. communicates with its command and control handlers, infects a machine, and penetrates the organization.
D. penetrates the organization, communicates with its command and control handlers, and infects a machine.
Which of the following statements regarding the threat prevention database is NOT correct?
A. The Security management server connects to the internet to get Malware Database updates.
B. By default, updates run on the security gateway every two hours.
C. The malware database only updates if you have a valid Anti-Bot/ or Anti-Virus contract.
D. The security gateway contains a local cache of the malware requests.
A customer does not own Check Point Gateways, but he wants to use Threat Emulation Service to detect SMTP Zero-Day vulnerabilities. What is his option?
A. Needs to buy a Check Point security gateway.
B. Purchase TE cloud service.
C. Use SMTP plug-in on his exchange server.
D. Needs to install Mail Transfer Agent on his firewall.
SmartLog displays:
A. Information about known threats and provides steps for remediation
B. Events in chart format, with detailed data about threats
C. Real time data, to help identify ongoing threats
D. Historic data that can be used for research purposes
Which of the following are valid Boolean search terms that can be used in custom SmartLog queries?
A. And, or, with
B. And, or, not
C. None, Boolean search terms cannot be used in SmartLog.
D. And, or, not, with
