156-215.75 Online Practice Questions and Answers
How can you most quickly reset Secure Internal Communications (SIC) between a Security Management Server and Security Gateway?
A. Run the command fwm sic-reset to initialize the Internal Certificate Authority (ICA) of the Security Management Server. Then retype the activation key on the Security Gateway from SmartDashboard.
B. Use SmartDashboard to retype the activation key on the Security Gateway. This will automatically Sync SIC to both the Security Management Server and Gateway.
C. From cpconfig on the Gateway, choose the Secure Internal Communication option and retype the activation key. Next, retype the same key in the Gateway object in SmartDashboard and reinitialize Secure Internal Communications (SIC).
D. From the Security Management Server's command line, Type fw putkey p
ALL of the following options are provided by the SecurePlatform sysconfig utility, EXCEPT:
A. DHCP Server configuration
B. GUI Clients
C. Time and Date
D. Export setup
Which of the following is a CLI command for Security Gateway R75?
A. fwm policy_print
B. fw shutdown
C. fw merge
D. fw tab -u
You are running a R75 Security Gateway on SecurePlatform. In case of a hardware failure, you have a server with the exact same hardware and firewall version installed. What backup method could be used to quickly put the secondary firewall into production?
A. upgrade_export
B. manual backup
C. snapshot
D. backup
You want to generate a cpinfo file via CLI on a system running SecurePlatform. This will take about 40 minutes since the log files are also needed. What action do you need to take regarding timeout?
A. Log in as the default user expert and start cpinfo.
B. No action is needed because cpshell has a timeout of one hour by default.
C. Log in as Administrator, set the timeout to one hour with the command idle 60 and start cpinfo.
D. Log in as admin, switch to expert mode, set the timeout to one hour with the command, idle 60, then start cpinto.
Your Security Management Server fails and does not reboot. One of your remote Security Gateways managed by the Security Management Server reboots. What occurs with the remote Gateway after reboot?
A. Since the Security Management Server is not available, the remote Gateway cannot fetch the Security Policy. Therefore, no traffic is allowed through the Gateway.
B. Since the Security Management Server is not available, the remote Gateway cannot fetch the Security Policy. Therefore, all traffic is allowed through the Gateway.
C. Since the Security Management Server is not available, the remote Gateway uses the local Security Policy, but does not log traffic.
D. The remote Gateway fetches the last installed Security Policy locally and passes traffic normally. The Gateway will log locally, since the Security Management Server is not available.
You can include External commands in SmartView Tracker by the menu Tools > Custom Commands.
The Security Management Server is running under SecurePlatform, and the GUI is on a system running Microsoft Windows. How do you run the command traceroute on an IP address?
A. There is no possibility to expand the three pre-defined options Ping, Whois, and Nslookup.
B. Go to the menu Tools > Custom Commands and configure the Windows command tracert.exe to the list.
C. Use the program GUIdbedit to add the command traceroute to the Security Management Server properties.
D. Go to the menu, Tools > Custom Commands and configure the Linux command traceroute to the list.
A company has disabled logging for some of the most commonly used Policy rules. This was to decrease load on the Security Management Server and to make tracking dropped connections easier. What action would you recommend to get reliable statistics about the network traffic using SmartReporter?
A. Turn the field Track of each rule to LOG.
B. Network traffic cannot be analyzed when the Security Management Server has a high load.
C. Configure Additional Logging on a separate log server.
D. SmartReporter analyzes all network traffic, logged or not.
Which command gives an overview of your installed licenses?
A. cplic print
B. showlic
C. cplicense
D. lic print
What is true about the Rule Base shown?
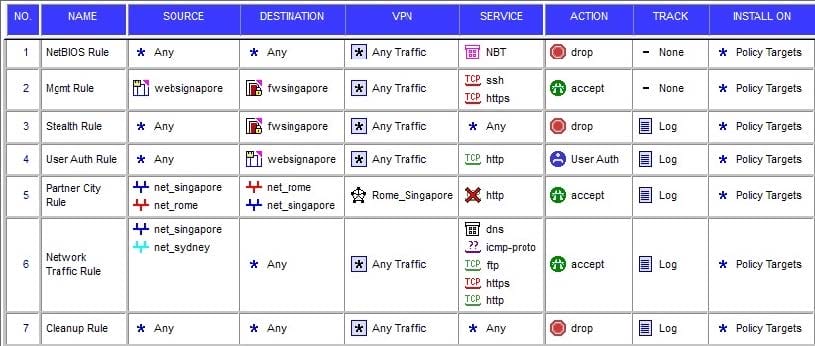
(i). HTTP traffic from webrome to websingapore will be encrypted (ii). HTTP traffic from websingapore to webrome will be encrypted (iii). HTTP traffic from webrome ro websingapore will be encrypted (iv). HTTP traffic from websingapore to webromw will be blocked
A. (ii) and (iii)
B. (iii) and (iv)
C. (i), (ii) and (iii)
D. (iii) only
You plan to create a backup of the rules, objects, policies, and global properties from an R75 Security Management Server. Which of the following backup and restore solution can you use?
1.
Upgrade_export and upgrade_import utilities
2.
Database revision control
3.
SecurePlatform backup utilities
4.
Policy package management
5.
Manual copies of the $CPDIR/conf directory
A. 2, 4, 5
B. 1, 3, 4
C. 1, 2, 3
D. 1, 2, 3, 4, 5
Which of the following items should be configured for the Security Management Server to authenticate using LDAP?
A. Domain Admin password
B. Check Point Password
C. Windows logon password
D. WM1 object
Which command allows Security Policy name and install date verification on a Security Gateway?
A. fw ver -p
B. fw stat -l
C. fw show policy
D. fw ctl pstat -policy
Users with Identity Awareness Agent installed on their machines login with __________, so that when the user logs into the domain, that information is also used to meet Identity Awareness credential requests.
A. ICA Certificates
B. Key-logging
C. SecureClient
D. Single Sign-On
Which Check Point mechanism used for controlling traffic enables firewalls to incorporate layer 4 awareness in packet inspection?
A. Stateful Inspection
B. Packet filtering
C. Application Intelligence
D. IPS
